Contents:
The number of cyberattacks spreading EvilExtractor malware across Europe and the U.S. is raising. Researchers warn that threat actors used the data theft tool in a massive phishing campaign in March 2023.
Hackers designed this malicious program to extract data and files from endpoints while targeting Windows operating systems.
Details About EvilExtractor
A company named Kodex sells the malware for $59/month. The product has seven modules, among which are ransomware, credential stealer, and bypass for Windows Defender.
Kodex claims that EvilExtractor is an educational tool, but they mainly advertised it for threat actors on hacking forums. The tool first surfaced on October 2022. Since then, cybercriminals use it as an information-stealing malware in the wild, Fortinet’s researchers say.
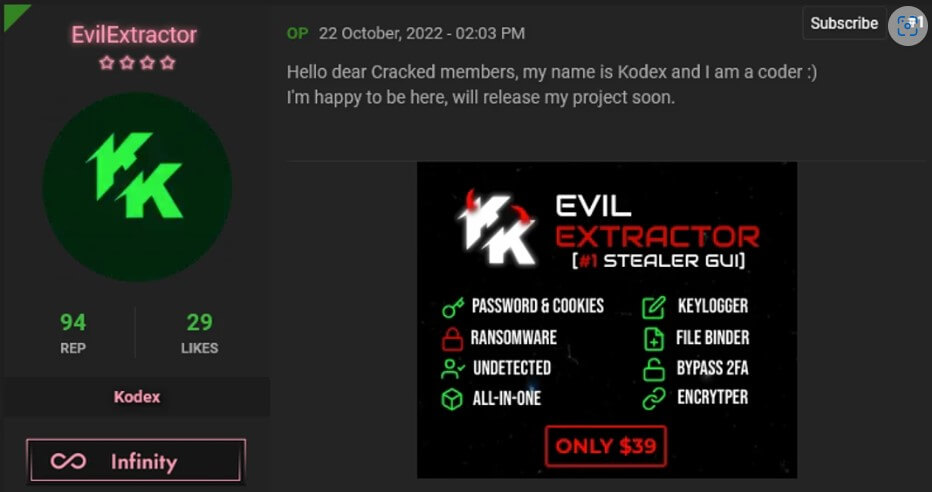
The developer continues to add features to the initial variant, which made it more potent and stable. This is why this malicious program is gaining traction in the hackers’ community.
Its use spiked in March 2023 due to a phishing campaign deploying this malware.
EvilExtractor in a Phishing Attack
The attack starts with a phishing email posing as an account confirmation request. The email message has an attachment containing a gzip-compressed executable. The executable looks like a legitimate PDF or Dropbox file but it is a Python executable program.
When the target opens the file, a PyInstaller file is executed and launches a .NET loader that uses a base64-encoded PowerShell script to launch an EvilExtractor executable.
Firstly, the malware will look for a virtual environment or analysis sandbox. If it finds one, it will exit the system.
The following modules are part of the version of EvilExtractor used in these attacks: Date time checking, Anti-Sandbox, Anti-VM, Anti-Scanner, FTP server setting, Steal data, Upload Stolen data, Clear log, and Ransomware.
The Steal Data module will deploy three extra Python programs: “KK2023.zip,” “Confirm.zip,” and “MnMs.zip.”
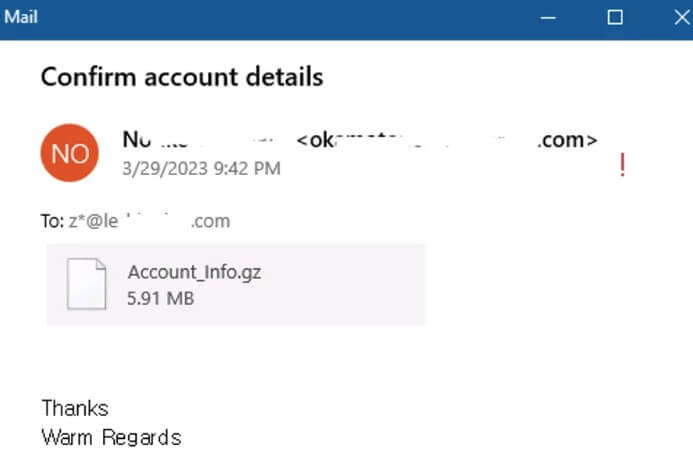
The first component steals cookies from Google Chrome, Microsoft Edge, Opera, and Firefox. It also extracts browsing history and saved passwords from a wide set of programs.
The second component is a keylogger. It collects keystrokes and stores them in a folder on the machine so it can steal them.
The third component is a webcam extractor. It can activate the webcam without permission in order to capture video recordings or images. This component will later send the files to an FTP server controlled by the cybercriminal.
But EvilExtractor does not stop at this, it also takes screenshots, steals numerous document and media file kinds from the Desktop and Downloads directories, and then sends all of the stolen information to its owner.
The ‘Kodex ransomware’ module is nested in the loader and, if activated, downloads an additional file (“zzyy.zip”) from the product’s website.
It’s a simple yet effective file-locking tool that abuses 7-Zip to create a password-protected archive containing the victim’s files, effectively preventing access to them without the password.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







