Contents:
To gain control of infected systems and, likely, to construct a botnet network, a new Go-based malware is targeting Redis servers. The attacks exploited a critical security flaw to plant a hidden backdoor and enable command execution.
Redis (Remote Dictionary Server) is an open-source, in-memory data structure store, used by developers as a database, cache, and message broker with optional durability.
The vulnerability, identified as CVE-2022-0543 (CVSS score: 10.0), belongs to a sandbox escape instance in the Lua scripting engine that may be exploited to achieve remote code execution.
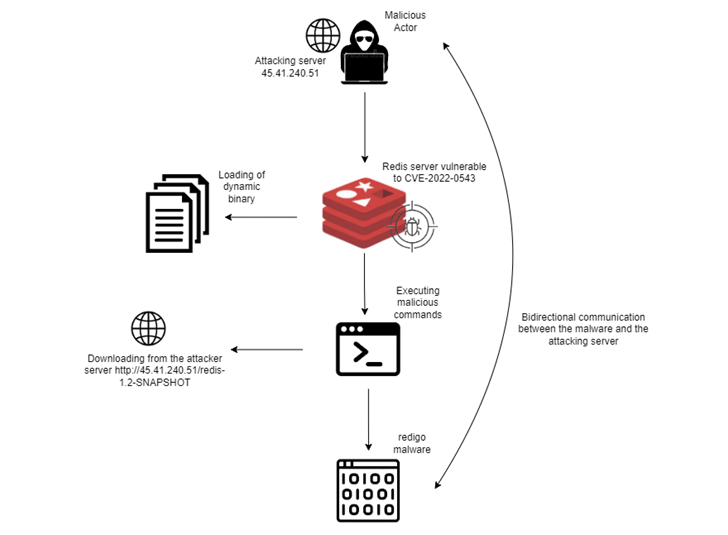
Redigo Malware Attack Flow
CVE-2022-0543 is a maximum severity vulnerability in the Redis software. In February 2022, it was found and fixed. But even after the fix came out and proof-of-concept exploit code was made public, attackers kept using it on machines that hadn’t been patched.
The Malware Mimics the Redis Server Communication
The Redigo infection chain is similar in that the adversaries search for exposed Redis servers on port 6379 to gain initial access before downloading a shared library called “exp lin.so” from a remote server, explains The Hacker News.
This library file includes an exploit for CVE-2022-0543 that executes a command to retrieve Redigo from the same server, as well as steps to cover up its activity by simulating legitimate Redis cluster communication over port 6379, to a report published last week by cybersecurity researchers from AquaSec.
The dropped malware mimics the Redis server communication which allowed the adversaries to hide communications between the targeted host and the C2 server.
The cybersecurity researchers also noted that Redigo’s ultimate purpose is likely to include the vulnerable server as a bot in a network for distributed denial-of-service (DDoS) attacks or to run crypto miners on infected computers.
Furthermore, because Redis is a database, accessing the data in order to steal it could also be a plausible outcome in Redigo attacks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










