Contents:
Last week, a ransomware developer decided to publish the complete source code of the Babuk encryption program on a Russian XSS hacker forum. The threat actor who leaked it is a 17 years old man diagnosed with Stage-4 lung cancer.
One of the developers for Babuk ransomware group, a 17 year old person from Russia, has been diagnosed with Stage-4 Lung Cancer. He has decided to leaked the ENTIRE Babuk source code for Windows, ESXI, NAS.
You can download the Babuk source here: vx-underground[.]org/tmp/
— vx-underground (@vxunderground) September 3, 2021
What is Babuk Ransomware?
Babuk (or Babyk) ransomware is a ransomware threat found in 2021 that has affected multiple large organizations and works by the modus operandi known as the Big-Game hunting strategy.
It’s is known that the threat actors behind Babuk usually publish proof of the breach in order to convince their targets that they really have in their possession important data.
Babuk ransomware group made some changes as they stated:
Babuk changes direction, we no longer encrypt information on networks, we will get to you and take your data, we will notify you about it if you do not get in touch we make an announcement.
Among the gang’s victims are the Phone House chain of stores for mobile devices and PDI Group, an Ohio-based company manufacturing different types of ground support equipment for military needs.
Babuk Actor Stops Operating
Earlier this year, Babuk ransomware hit the Metropolitan Police Department (MPD) and stole more than 250 gigabytes of data that allegedly included police reports, internal memos, and PII of confidential informants, and work staff.
The threat actors threatened MPD to leak the stolen information if the requested ransom is not paid.
Following this attack, the Babuk operation announced they will halt their operations. Despite this announcement, a few months later, the gang came back employing a new version of their file-encrypting malware (Babuk V2) that is still operational.
Following their return, the original admin accused his gang members of trying to make his new site unusable by subjecting it to a series of DDoS attacks.
vx-underground security specialists were first to see the source code leak and according to them, responsible for the leak is a Babuk developer.
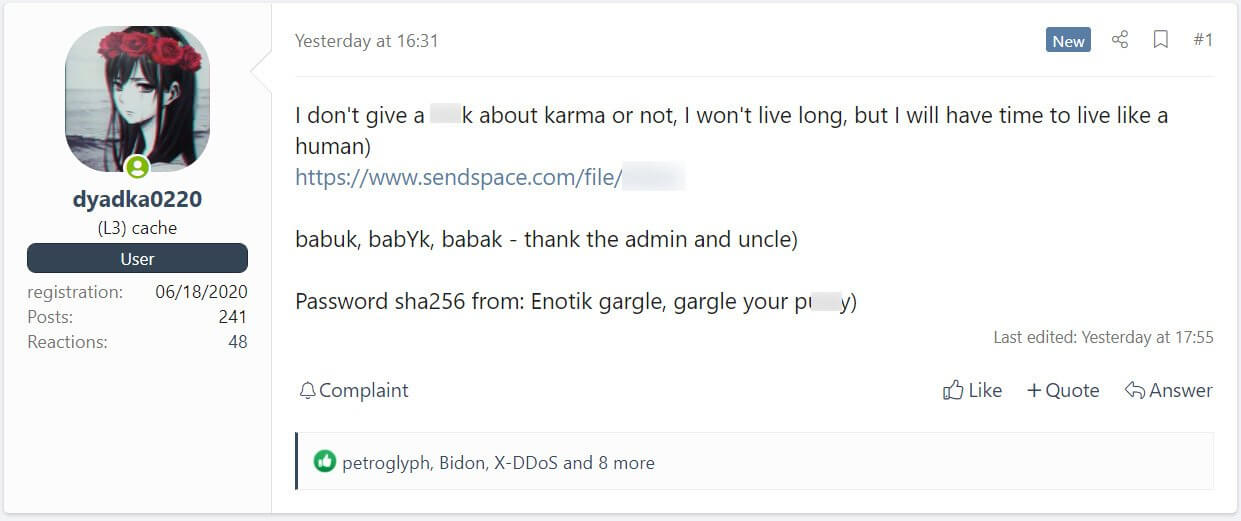
The source code enables easy access to an advanced ransomware strain and it has everything a threat actor needs to create an operational ransomware executable.
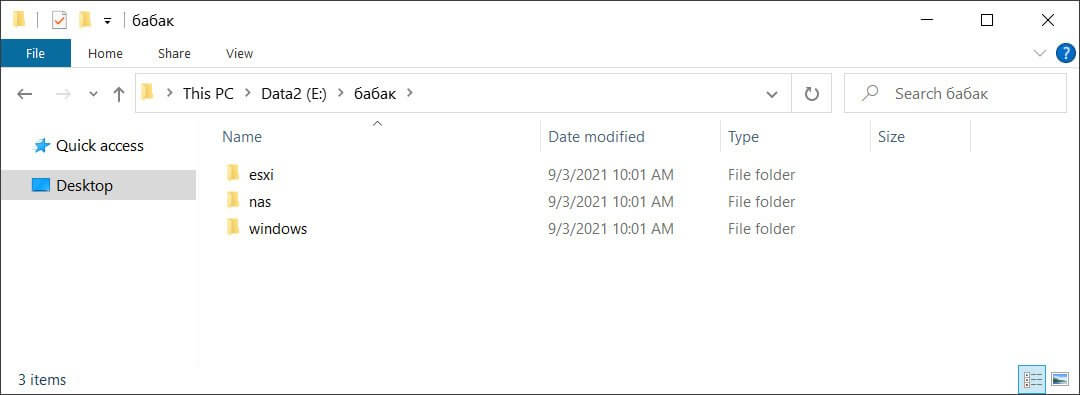
The published file includes various Visual Studio Babuk projects for VMware ESXi, NAS, and Windows.
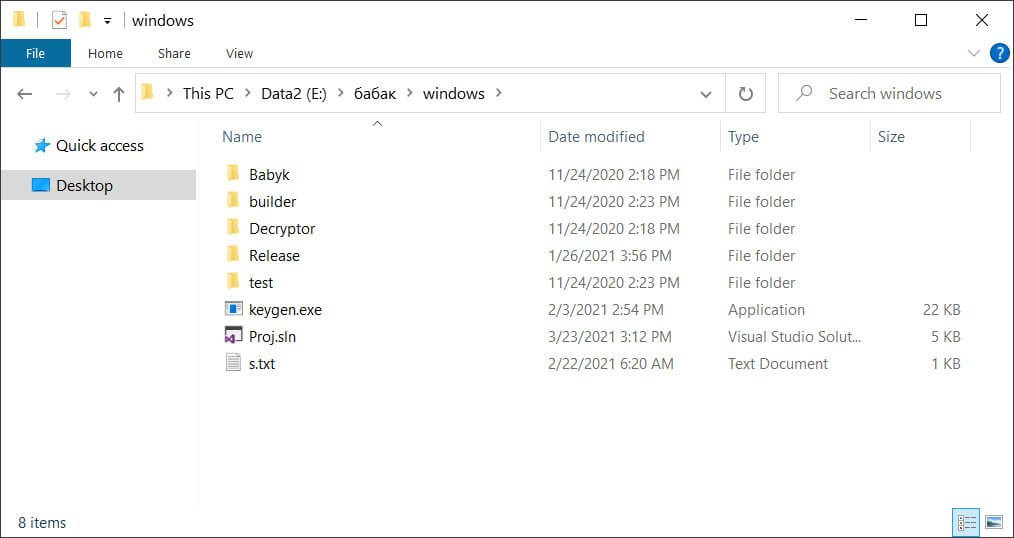
The Windows folder contains the full source code for the Windows encryptor, decryptor, and a private and public key generator.
The leak has been confirmed to be authentic by Emsisoft experts. Apparently, among other things, the leak also includes ransomware and decryptors for certain victims of the ransomware actor.
At the beginning of July, the builder for the Babuk Locker ransomware, a tool that is employed to create custom ransomware executables, was published online. Shortly after the leak, a hacker started using it to initiate a very active ransomware operation targeting victims all over the world.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








