Contents:
The builder for the Babuk Locker ransomware, a tool that is employed to create custom ransomware executables, was leaked online.
Shortly after the builder was published online, a hacker started using it to initiate a very active ransomware operation targeting victims all over the world.
Babuk ransomware was a ransomware threat discovered at the beginning of 2021 that was targeting big enterprises in order to steal their data in double-extortion attacks.
The Babuk Locker operators shut down their operations at the end of April following the cyberattack against the Washington, DC police department.
Babuk Locker Ransomware Rebranded as Payload.bin
A month later, the Babuk Locker group rebranded their ransomware leak website into Payload.bin and began offering the opportunity to other gangs to use it to leak data stolen from their victims.
Cybersecurity specialists think that the group’s decision to stop operating could be the consequence of an operational error. They probably realized it wasn’t a good idea to threaten the US police department due to the information that it holds.
The ransomware group broke into the Washington, D.C., Metropolitan Police Department, encrypted its files, and requested a $4 million ransom. The Babuk ransomware gang declared to have stolen 250GB of files, including sensitive information belonging to police members and informers.
Last week, cybersecurity expert Kevin Beaumont discovered that someone uploaded the code used to build copies of Babuk ransomware to malware-scanning service VirusTotal.
Ransomware leak time – Babuk’s builder. Used for making Babuk payloads and decryption.
builder.exe foldername, e.g. builder.exe victim will spit out payloads for:
Windows, VMware ESXi, network attached storage x86 and ARM.
note.txt must contain ransom.https://t.co/K3J3zr1XBv pic.twitter.com/1bl7oc0TvO
— Kevin Beaumont (@GossiTheDog) June 27, 2021
Specialists who obtained and studied a copy of the builder confirmed that it allows creating custom versions of the Babuk Locker ransomware that targets Windows systems, VMWare ESXi servers, and ARM-based network storage attached (NAS) devices.
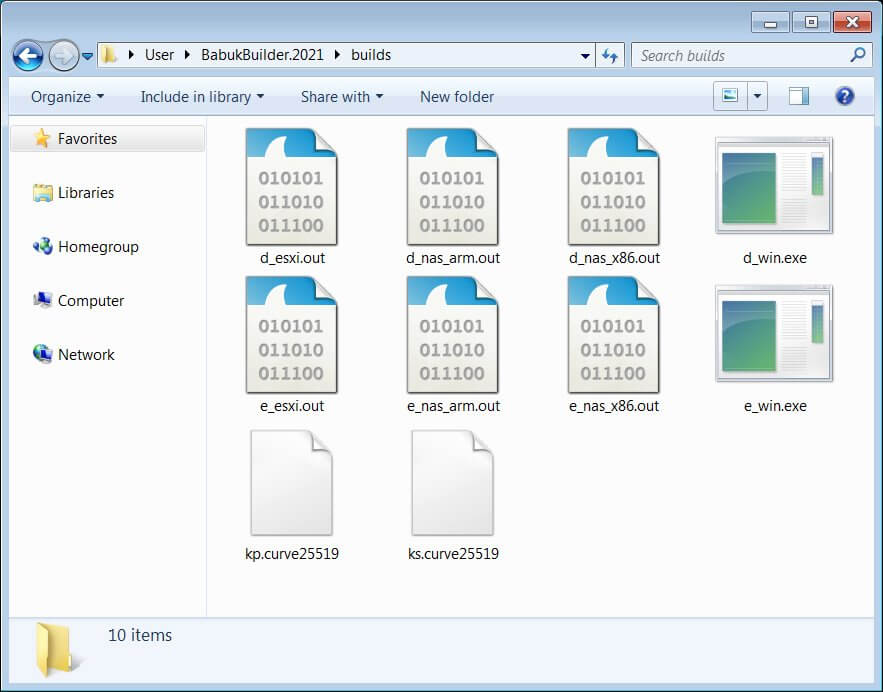
Many companies depend on NAS as part of their backup and restore strategy, meaning that if cybercriminals are able to crypto-lock not just Windows PCs but also these backups, then more victims may be forced to pay a ransom in order to have their files decrypted.
The available builder also creates decrypters that could be used by victims to recover the encrypted files.
At the moment, it is not clear if the Babuk ransomware group attempted to sell the builder to a third party and the deal went bad, or if it was leaked by a competitor.
Recently the complete source code for the Paradise Ransomware has been released on the hacking forum XSS allowing hackers to develop their own customized ransomware operation.
While the two incidents are believed to be unrelated, the availability of these builders online is concerning because other low-effort cybercrime groups can now adopt the two tools and use them to target businesses all over the world.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










