Contents:
The ransomware unpacks itself and encrypts files on the affected computer, once the user opens the file by adding extensions like “.paradise”, “.2ksys19”, “.p3rf0rm4”, and “.FC”.
The Paradise ransomware also works by deleting the backups in an attempt to obtain maximum impact and therefore more easily pressuring the victim into paying the ransom.
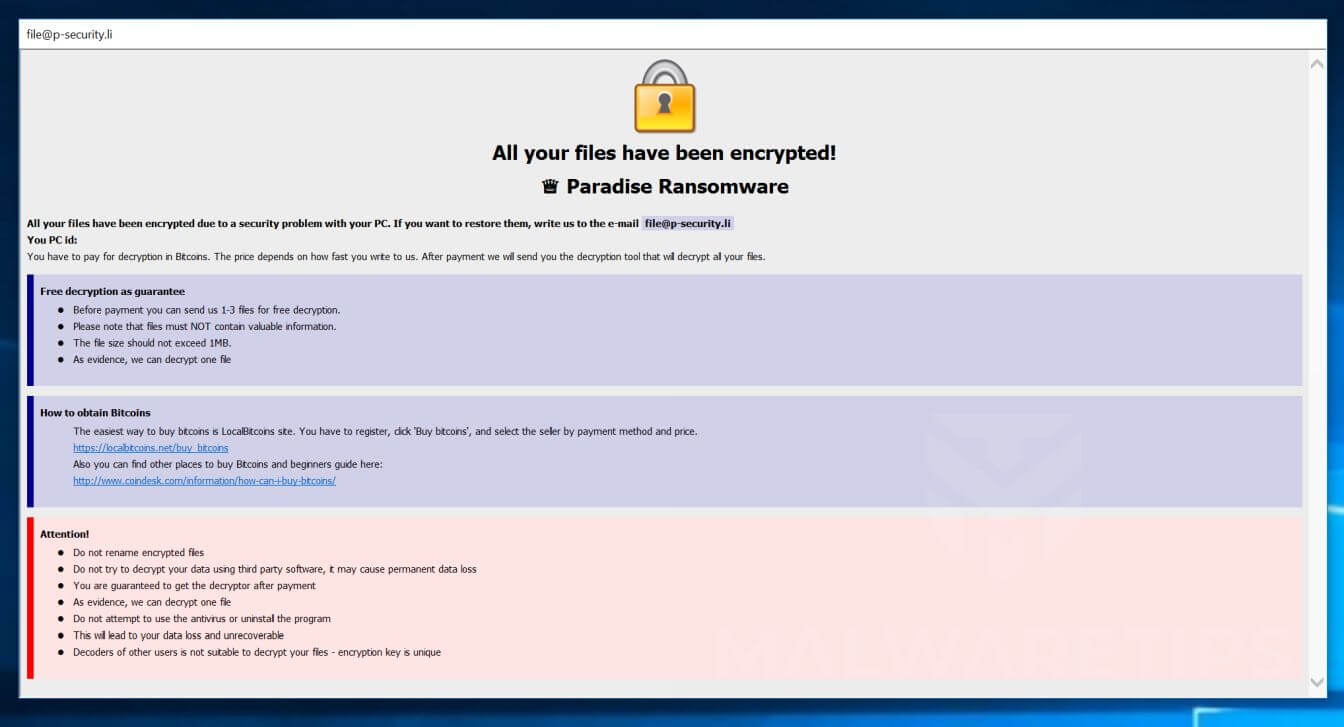
Recently the complete source code for the Paradise Ransomware has been released on a hacking forum, in this way allowing any cybercriminal to be able to develop their own customized ransomware operation.
What happened?
The source code was released on the hacking forum XSS with the source code link only accessible to active users on the platform. These users must have previously replied or reacted to other similar posts on the website.
Previously this year, the XSS hacking forum removed all ransomware topics from its website most likely in order to prevent any unwanted attention in the current international context where RaaS type activities have grown in numbers and are now far more common and easy to encounter.
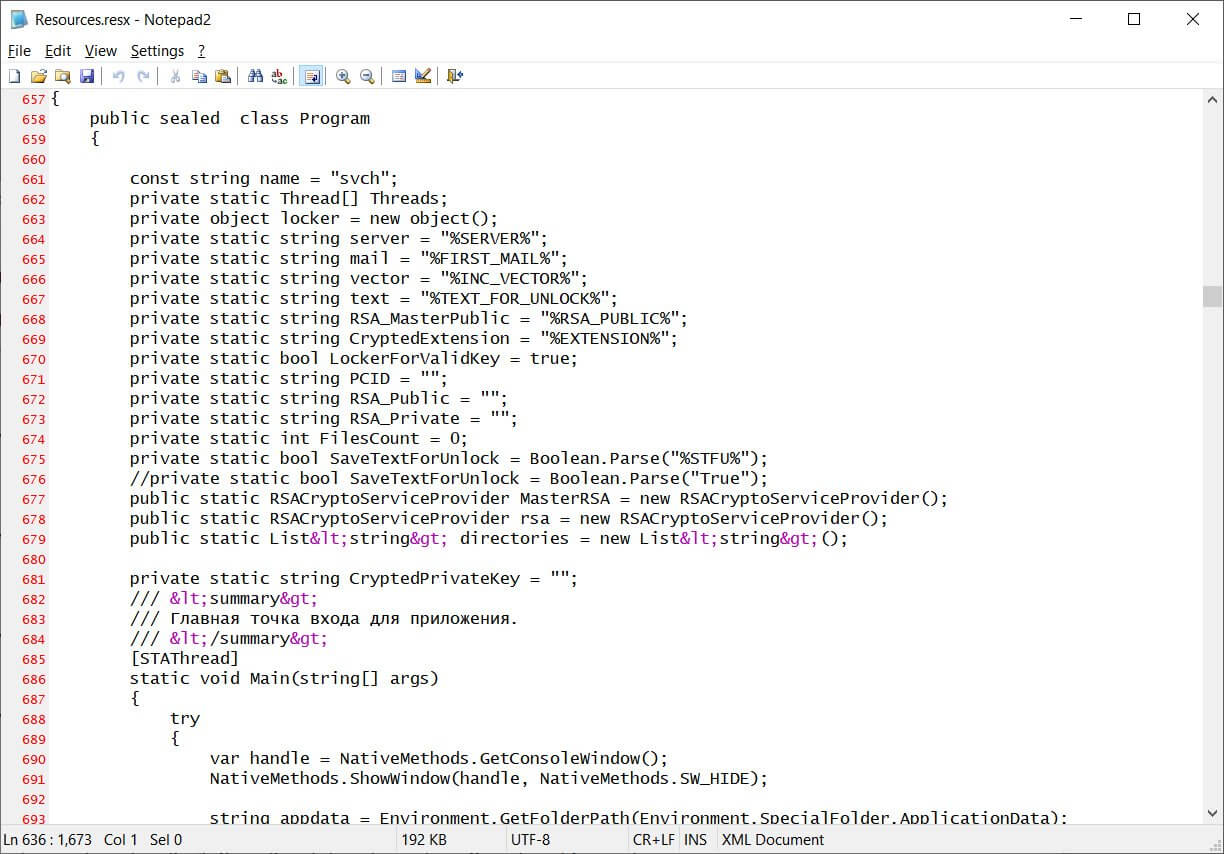
Security researcher Tom Malka shared the source code with the news publication BleepingComputer. He compiled the package and found that it creates three executables, a ransomware configuration builder, the encryptor, and a decryptor.
It’s interesting to note that throughout the source code can be found Russian comments, this clearly demonstrating that Russian is probably the native language of the developer.
The Paradise ransomware affiliates are now able to make use of the builder in order to customize their own version of the ransomware and include a custom command and control server, encrypted file extension, and contact email address to distribute the malware in their campaigns to target victims.
The Paradise Ransomware operation was first seen in September 2017. At that time, it was using phishing emails that were containing malicious IQY attachments that downloaded and installed the ransomware, but in time more versions of the ransomware were released, with the initial versions containing flaws that led to the release of a Paradise Ransomware decryptor.
The new versions switched the encryption method to RSA, in this way preventing the free decryption of files.
Michael Gillespie the researcher that created the original Paradise Ransomware decryptor disclosed that the versions of Paradise that were released include:
- Paradise – Native version that had the flaws allowing decryption.
- Paradise .NET – A secure .NET version that switched encryption algorithms to use RSA encryption.
- Paradise B29 – A “Team” variant that only encrypted the end of a file.
The researcher said that it is not clear at this time if the versions were all developed by the same group as they were all circulating at around the same time with thousands of different extensions.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Unfortunately, the leaked source code is one of the secure version of Paradise Ransomware that makes use of the RSA encryption, therefore by using this source code, the threat actors can easily modify it to release their own customized version of the ransomware, leaving room for an easy entry point into the birth of new ransomware operations.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security