Contents:
Picking the right cybersecurity system for your business can be tricky, especially when you have options like Tenable and Qualys.
In this article, we’ll check two popular solutions: Nessus by Tenable and VMDR by Qualys.
We’ll analyze both solutions, see what are their strong points, touch on their weaknesses, check if there are other suitable alternatives in the market, and ultimately, help you decide.
Let’s get started!
Introduction to Tenable and Qualys
What Is Tenable Nessus?
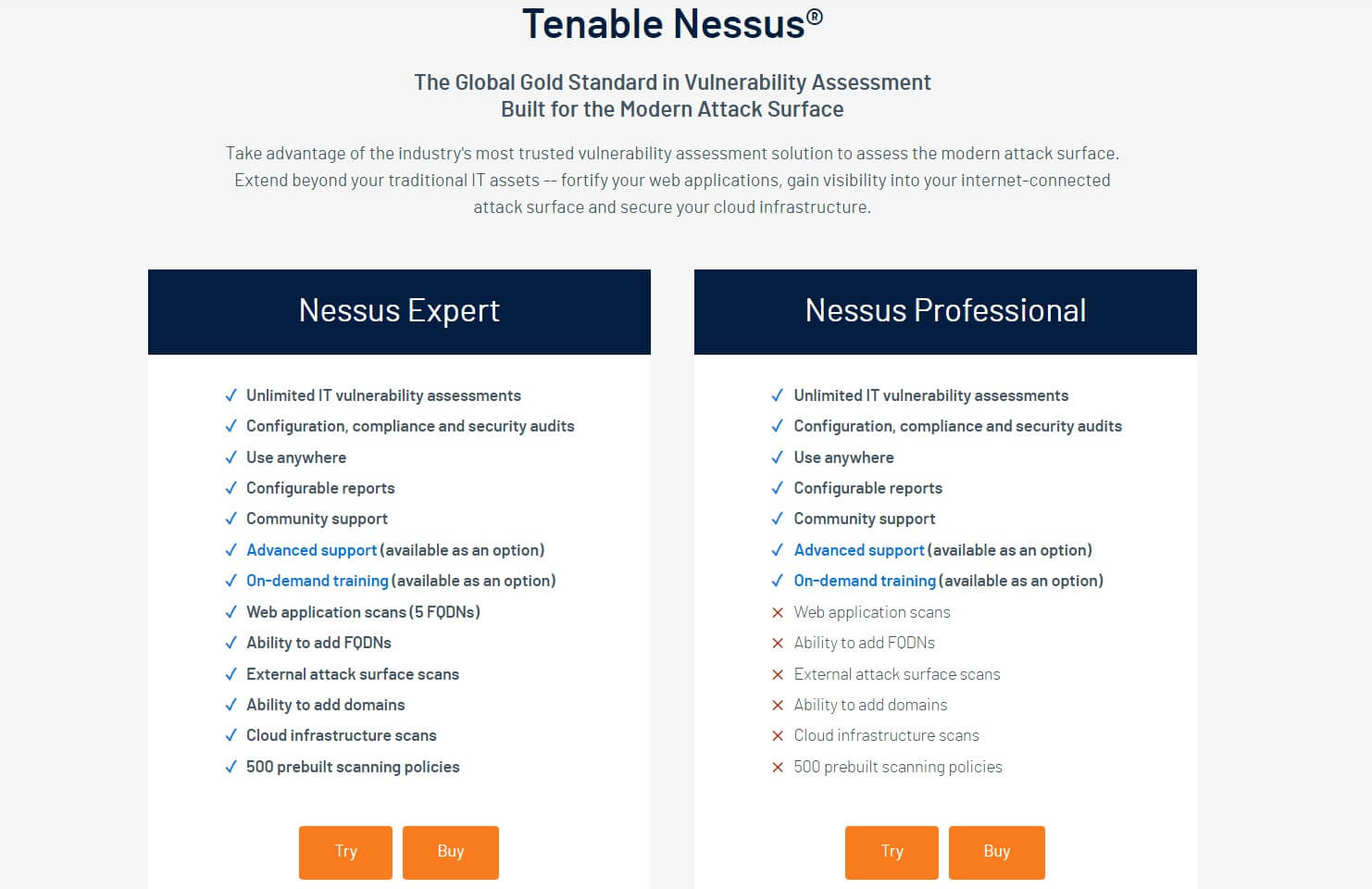
Tenable Nessus is a cybersecurity tool which became available 1998, first for free, and gained popularity in 2005, when it became a paid product.
Nessus is like a detective for your computer network, finding weak points that could let bad guys in. It looks at everything from apps to cloud services to keep your network safe.
Its job is to help IT teams find and fix problems before hackers can take advantage of them.
It’s really good at spotting things like software bugs, viruses, and mistakes in how things are set up. When it finds something wrong, it tells the IT team right away so they can fix it fast.
In short, Tenable Nessus is like a watchdog, always on the lookout to keep your digital assets safe from harm.
What is Qualys VMDR?
Qualys VMDR is a viable option for businesses, helping them locate and fix endpoint vulnerabilities before threat actors can exploit them.
It’s a one-stop-shop that does everything from keeping track of what’s on your network to finding and fixing security holes in real-time.
It works automatically, constantly scanning for problems, prioritizing them, and even finding the best way to fix them.
This system also learns from past experiences, making sure to focus on the most important risks first.
Overall, Qualys VMDR makes cybersecurity easier and stronger, giving businesses peace of mind that their digital assets are safe.
Tenable vs Qualys: Core Features
Tenable Nessus Core Features

Nessus comes equipped with a bunch of features designed to enhance vulnerability assessment and remediation processes. Let’s check them out:
- Extensive Plugin Database: Nessus is known for having a huge collection of plugins. These plugins help it scan systems faster and find vulnerabilities more effectively. You can customize these plugins to match your organization’s specific needs.
- Common Vulnerability Scoring System (CVSS) Integration: Nessus gives each vulnerability a rating called Vulnerability Priority Rating (VPR). This rating is compared to the Common Vulnerability Scoring System (CVSS). Higher ratings mean more serious vulnerabilities, helping IT teams prioritize which issues to fix first.
- Predictive Prioritization: Using advanced technology, Nessus sorts vulnerabilities by how urgent they are. This helps IT teams quickly identify and address the most critical threats.
- Live Results: Nessus can perform vulnerability assessments even without an internet connection. This means it can find and fix issues faster, without needing to rescan everything again.
- Configurable Reporting: You can create different kinds of reports with Nessus, like HTML or CSV files. This makes it easier to share information and metrics about the vulnerabilities it finds.
- Grouped View: Nessus organizes similar vulnerabilities into groups, making it easier for IT teams to prioritize and fix security risks efficiently.
- Packet Capture: This feature helps IT teams quickly diagnose and solve any issues that might be slowing down the scanning process. It ensures continuous protection for the IT environment with minimal disruptions.
Qualys VMDR Core Features
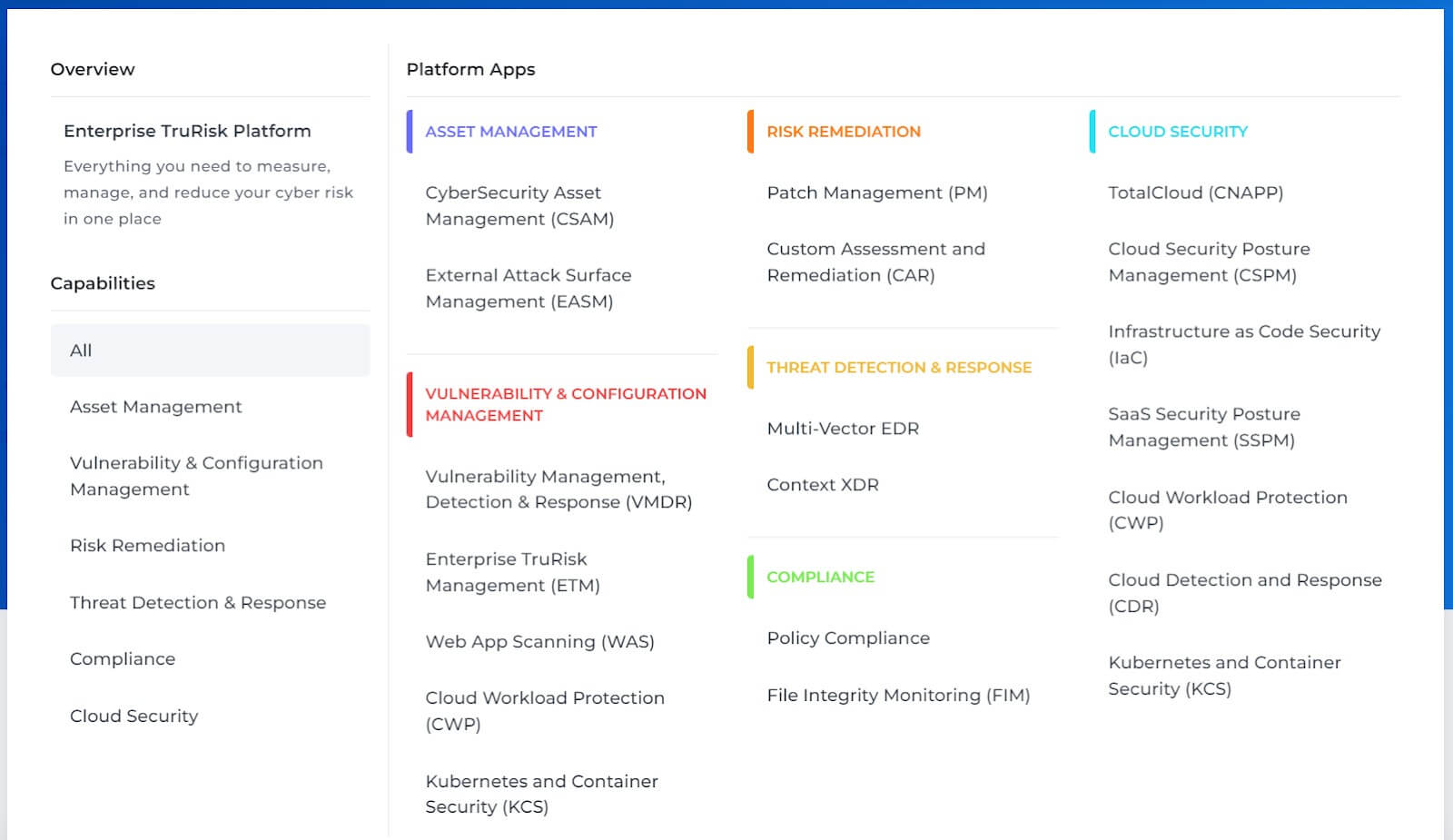
Qualys VMDR (Vulnerability Management, Detection, and Response) also comes with a pretty diverse list of functionalities. Let’s explore its key features:
- Comprehensive Asset Visibility: You have visibility over all your computer systems and devices. Plus, you get extra information about the risk they pose to the organization if breached.
- Accelerated Threat Detection: This helps you find the most serious problems quickly. You can fix them faster, making your systems safer sooner.
- Transparent Risk Prioritization: It’s easy to decide which problems to fix first. This can reduce the number of issues by a lot and make your systems safer.
- Automated Remediation Orchestration: Fixing problems is made easier with automatic processes. This can make fixing issues faster than doing it by hand.
- Risk Visualization and Measurement: Use tools to see and measure how risky your systems are accurately. This helps your decision-making process about fixing problems.
- Confident Prioritization: You can use lots of information about threats to know which issues are most urgent. This helps you focus on fixing the most important problems first.
Tenable vs Qualys: What Does Reddit Think?
Cybersecurity professionals appreciate Tenable Nessus for its clear confirmation readouts, aiding in quickly assessing vulnerabilities and guiding remediation. They find Qualys prone to more false positives and dislike its scanner licensing costs.
Tenable’s inclusion of CIS controls for free is valued. While historically, Qualys had superior reports, both tools are now comparable.
Qualys is praised for its swift detection, especially for critical vulnerabilities like Log4J. Some prefer Qualys for its flexibility in deployment options, including portable hardware appliances.
However, the decision often comes down to individual needs and preferences, emphasizing the importance of trial evaluations.
Here’s what some have to say about Nessus and VMDR:
I’ve used both and would overall recommend Nessus. Qualys would be better than nothing but if you can afford it, go with Nessus. I’ve seen more false positives with Qualys but it may depend on the type of environment you are scanning.
Consider which platform is easier to work within. Paying a little more up front may be better if it will save you time every day when you are setting up scans, reviewing findings, reviewing reports, etc.
Reddit Review of Nessus and VMDR
Nessus is worth the price from time savings alone. It gives a confirmation readout of each plugin why it was triggered, and usually includes the “how to resolve it” for that specific device.
This is helpful in confirmation of the vulnerability vs wasting time fixing false positives. Both Qualys and Nessus have unique ways to determine vulnerability, not always are they correct. It also helps frame the perspective of the vulnerability plug-in so it’s easier to reproduce and validate its resolved outside of another scan. Nessus has a remediation scan option as well for verification by the ticket owner so they don’t need to bother the Security Team to rescan.
Reddit Review of Nessus and VMDR
I don’t like the fact that Qualys charges you for each scanner even when that’s just a VM running on your hardware. You’d think that a company would want to allow you to run as many scanners as you’d need in order to make the product work better. If you’re only using agents that doesn’t matter quite as much.
I also like that Tenable includes things like CIS controls for free as well.
Reddit Review of Nessus and VMDR
It feels like overall, cybersecurity professionals engaging on Reddit have a stronger sentiment towards Nessus, based on its pricing plan, quality of reports, and smaller percentage of false positives.
Pricing Comparison
When making your decision between two cybersecurity solutions, pricing is an important aspect to consider.
Pricing Structure of Tenable Nessus
Tenable Nessus offers a multi-year pricing plan which starts at $4708.20 per year.
If you decide on purchasing the license for 2 or 3 years, discounts are applied. Additionally, Nessus makes you pay an extra $472 for support, giving you access to a 24×365 platform, and an extra $295 for on-demand training (video course for 1 person).
Pricing Structure of Qualys VMDR
Qualys VMDR’s price depends on your selection of Cloud Platform Apps, IPs, web apps, and user licenses.
For a pricing quote you will have to contact them directly and offer this information.
Tenable vs. Qualys: What Do Users Think?
Tenable Nessus User Reviews
Users appreciate Tenable Nessus for its versatility and user-friendly interface, making security scans and vulnerability assessment easy.
However, they criticize its high rate of false positives, especially on Linux systems, and its reliance on reading banners, causing frustration with server administrators.
Tenable Nessus is versatile and flexible to use. This software can be used for security scans, network scanning, vulnerability assessment and scanning. Its interface is user friendly and anyone can use it very easily. It has the ability to automate scanning and reporting tasks. This software can help organizations identify vulnerability, threats to their systems and networks.
G2 User Review of Tenable Nessus
Nessus generates a large amount of false positives, particularly on Linux systems for applications like Apache, Tomcat, etc. It generally only reads the banners, and even if you run an authenticated scan, it often does not detect patches that are backported by the distribution. This leads to a lot of heartburn when working with server administrators.
G2 User Review of Tenable Nessus
Qualys VMDR User Reviews
Users like Qualys VMDR for its user-friendly interface and customizable scanning options, which have boosted scanning efficiency.
However they complain about the complex workflow required by the design solution for downloading data into a single CMDB table, stating it doesn’t align with their business case.
The best aspect of Qualys VMDR is its user-friendly interface that allows for easy and intuitive vulnerability scanning. The platform empowers us to select and customize the specific types of scans we need, providing a tailored approach to address our unique security requirements. This flexibility and simplicity have significantly improved our overall scanning efficiency and helped us stay on top of potential vulnerabilities, ensuring a robust security posture for our organization.
G2 User Review on Qualys VMDR
I didn’t like the design solution of downloading data from Qualys into a single table into CMDB. This design solution requires a complex workflow design in the CMDB side, for that reason this solution does not fit our business case.
G2 User Review of Qualys VMDR
Tenable vs. Qualys: How to Choose the Best Solution
Choosing the right cybersecurity solution is crucial for protecting your data and privacy. Here are some important factors to consider:
- Security Features: Look for a solution that offers robust security features such as antivirus protection, firewall, intrusion detection, and encryption. Make sure it covers all aspects of cybersecurity that your organization needs.
Businesses should ensure the cybersecurity solutions they purchase reduce their risk, not increase it. This sounds like a no-brainer, but recent vulnerabilities—such as Citrix Bleed and coordinated attacks on firewalls at dozens of energy suppliers—show that there’s real risk. Look for solutions that have secure development practices and zero-trust policies in place so they can’t be leveraged as an attack vector.
Geoffrey Mattson, Xage Security
- Compatibility: Ensure that the cybersecurity solution is compatible with your existing systems and software. It should seamlessly integrate with your IT infrastructure without causing any disruptions.
When choosing a cybersecurity platform, consider how easy it will be to integrate it with your existing tech infrastructure. Seamless integration minimizes implementation time and cost, reduces operational disruptions, and ensures that the cybersecurity enhancement doesn’t hinder daily business processes, maintaining operational efficiency alongside robust security measures.
Andres Zunino, ZirconTech
- Scalability: Choose a solution that can grow with your business. It should be able to accommodate increasing data volumes and expanding user bases without compromising security.
Scalability is critical, and businesses should look at products that can scale with their organization and not just solve the “problem du jour.” Point-in-time solutions may address a pain point today, but products that can grow with your business will provide more comprehensive, long-term protection.
Andrew Kahl, BackBox
- Ease of Use: Opt for a solution that is user-friendly and easy to manage. It should have a simple interface and intuitive controls to make it easier for your IT team to monitor and manage security.
The majority of cybersecurity incidents happen because of human error. Even the most advanced platform will be rendered useless if it’s not used effectively by your people. So businesses should prioritize ease of use and intuitiveness when selecting a cybersecurity platform, ensuring seamless integration with existing infrastructure as well as a quick onboarding process.
Tom Okman, Nord Security
- Cost: Consider the cost of the cybersecurity solution, including upfront expenses and ongoing maintenance fees. Balance the cost against the level of protection it provides and the value it adds to your organization.
Another factor to consider when selecting a solution is its cost. While some solutions may have lower upfront costs, they often come with additional fees for maintenance or upgrades over time. Therefore, you need to determine what kind of financial commitment your organization is willing to make for the chosen solution.
Arun KL, Security Architect
- Reputation and Reviews: Research the reputation of the cybersecurity solution provider and read reviews from other users. Look for testimonials and case studies to gauge the effectiveness of the solution in real-world scenarios.
Review the vendor’s ability to attract and retain top cybersecurity talent (the type who actively avoids working on dated technologies). Also, assess the potential brand hit of being breached through the vendor’s specific solution—some tools provide stronger “due diligence” optics after an incident. Adopting limited-lifespan solutions raises costs due to the need for constant skill retraining, and you may risk negative public perceptions of your brand.
Mani Padisetti, Digital Armour
- Compliance Requirements: Ensure that the solution meets regulatory compliance standards relevant to your industry. This is especially important for industries such as healthcare and finance, which have strict data protection regulations.
Ensure compliance with the privacy laws in your jurisdiction(s). In the U.S., make sure you’ll be compliant with California’s Consumer Privacy Act, and in the E.U., with the General Data Protection Regulation. Also, remember that the legal obligation you owe customers under some privacy laws becomes more strict as the sensitivity of the data you hold increases (for example, geographic data versus medical information).
Jordan Yallen, MetaTope
- Future-proofing: Anticipate future cybersecurity challenges and select a solution that is adaptable and future-proof. It should have the capability to evolve and adapt to emerging threats and technologies.
When choosing a cybersecurity platform, businesses should look beyond current features to the product’s future roadmap and its ability to adapt to evolving cybersecurity threats. It’s essential to consider how the platform updates to counter new risks, as well as the strength of its ecosystem, including integrations, community support, its partner landscape and long-term security solutions.
Raj Polanki, Wacker Chemical Corporation
An Alternative to Tenable and Qualys? How About Heimdal®
Maybe Tenable and Qualys aren’t the solutions you are looking for. You can explore more Qualys alternatives in this article.
What if you want a more unified, automated, and broader solution instead, scalable so that grows and adapts to your business needs? Then, look no further than Heimdal®!
Heimdal® stands as a robust cybersecurity solution provider, offering a suite of advanced tools designed to protect organizations against sophisticated cyber threats.
At the core of Heimdal®’s offerings lies the MXDR service, built upon the Heimdal® XDR – Unified Security Platform.
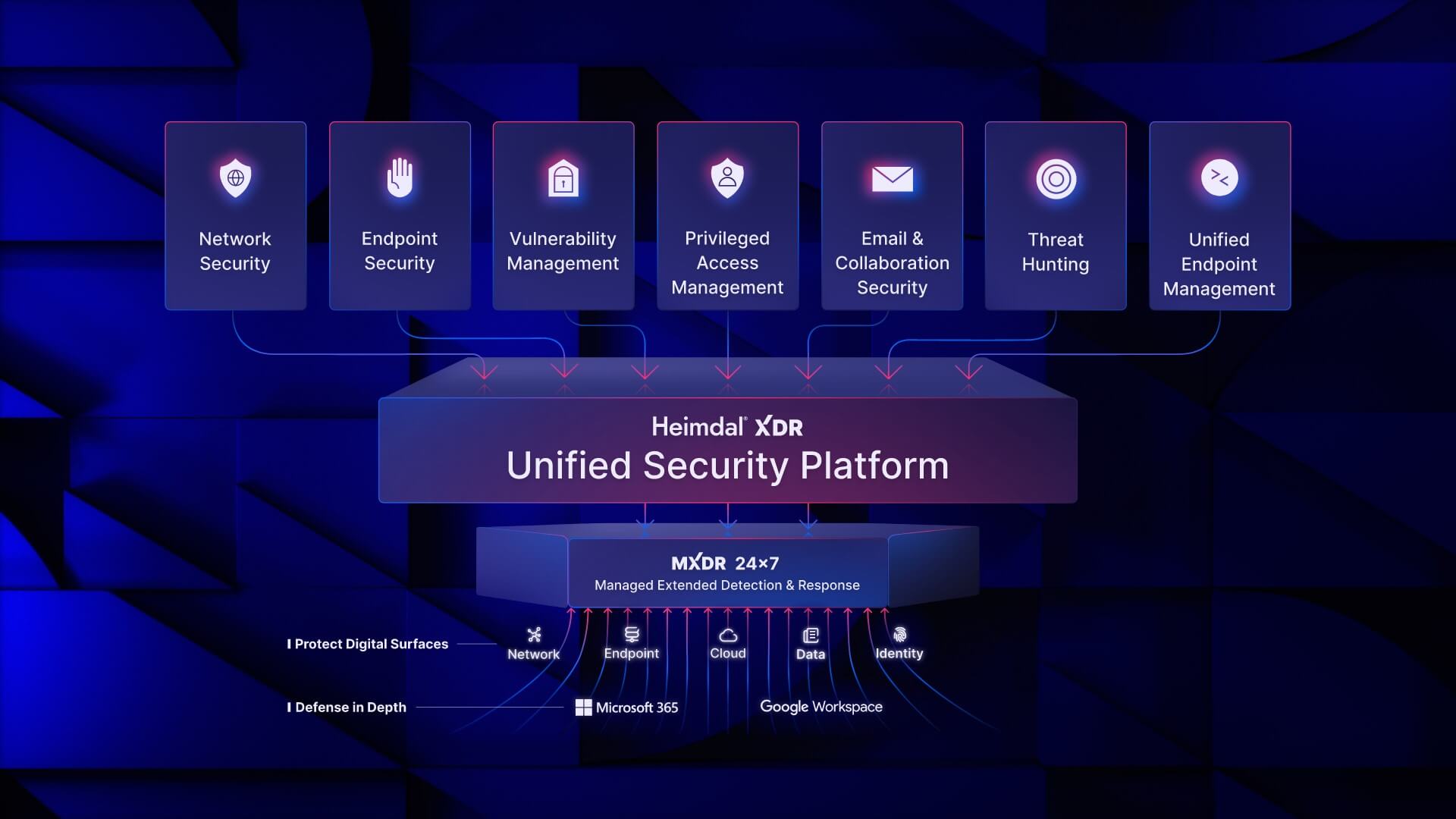
This platform integrates various cybersecurity solutions to deliver holistic protection across endpoints, networks, and data, ensuring organizations stay one step ahead of evolving threats.
Heimdal® Suite of Solutions
Heimdal® offers a comprehensive suite of solutions tailored to meet the diverse needs of organizations:
- MXDR Service: Heimdal®’s MXDR service combines threat detection and response, endpoint security, and data protection into a unified platform, providing organizations with robust defense mechanisms against cyber threats.
- Patch and Asset Management: Heimdal®’s Patch and Asset Management solution streamlines the patching process, ensuring systems remain up-to-date and secure against known vulnerabilities. With automated patch deployment, customizable policies, and comprehensive reporting capabilities, organizations can maintain compliance and mitigate risks effectively.
- Cybersecurity Tools: Heimdal® provides a wide range of cybersecurity tools, including network security, vulnerability management, privileged access management, endpoint management, threat hunting, email, and collaboration security, among others. These tools equip IT professionals with everything they need to deliver top-notch cybersecurity services to their clients.
Heimdal®’s Patch & Asset Management Solution
Heimdal®’s Patch & Asset Management software is a completely automated vulnerability management solution that you govern! With automated software becoming the new business standard, opting for a manual patching and vulnerability management tool will make you less efficient and lacking in front of your competitors.
We said that you govern our solution, what we mean is that Heimdal®’s software is fully customizable, and you can make it fit your organization’s needs perfectly.
With our patch & vulnerability management solution, you will be able to:
- Patch Windows, Linux, macOS systems, and even third-party and proprietary software;
- Keep track of all your organization’s software and assets and their vulnerability state from the inventory tab;
- Easily adhere to highly-requested industry compliance standards such as NIST, HIPAA, PCI-DSS, Cyber Essentials, UK PSN, and more;
- Conduct vulnerability and risk management processes automatically;
- Close vulnerabilities, mitigate exploits, deploy updates, both globally and locally, anytime, from anywhere in the world.
Why is Heimdal® a Great Alternative?
- Comprehensive Protection: Heimdal®’s MXDR service offers holistic protection against cyber threats, covering detection, response, endpoint security, and data protection. This comprehensive approach ensures organizations of all sizes and industries can effectively safeguard their assets and sensitive information.
- Tailored Security Features: Heimdal®’s solutions are adaptable to organizations’ unique requirements, making them suitable for multinational corporations, SMBs, and everything in between. IT professionals can leverage Heimdal®’s flexible offerings to enhance their clients’ security posture and mitigate cyber risks efficiently.
- Customization and Integration: Heimdal®’s Patch and Asset Management solution stands out for its customization capabilities, allowing IT professionals to tailor the software to their specific business needs. Furthermore, Heimdal® offers seamless integration with other modules, providing IT professionals with a unified platform to address their clients’ cybersecurity needs comprehensively.
- Ease of Management: With Heimdal®, IT professionals can efficiently manage cybersecurity tasks across multiple clients through an intuitive dashboard and automated processes. This saves time and resources while ensuring clients’ systems remain secure and compliant with industry regulations.
What People Like About Heimdal®
People love Heimdal® for its generous selection of cybersecurity solutions boasting the world’s widest cybersecurity platform with 13 products , unified all-in-one approach, amazing customer support and overall ease of use.
It features highly customizable solutions, meaning that companies of all kind will find the right balance for their needs whatsoever.
Pricing:
Heimdal®’s pricing is flexible and tailored to the specific needs of IT professionals. Organizations can book a call with Heimdal®’s experts to receive more information on pricing plans and benefit from an exclusive demo of the solutions.
This personalized approach enables organizations to choose the right package that aligns with their budget and requirements, ensuring maximum value and ROI.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










