
Cybersecurity News | QUICK READ
Math Symbols Used for Spoofing Purposes in Phishing Campaigns
The Mathematical Symbols Were Used to Evade Detection.

Cybersecurity News | QUICK READ
New Phishing Attack Uses a Compromised SharePoint Website as a Lure
The M.O. Relies on Convincing Emails and Other Techniques Used to Bypass Phishing Detection.

Cybersecurity News | QUICK READ
FBI Is Warning Investors of Fraudsters Posing as Brokers
The Scheme Tries to Lure the Targets Into Investment Scams by Using Spoofed Sites, Fake Social Media Profiles, Cold Calling, and Doctored Documents.
Cybersecurity News | QUICK READ
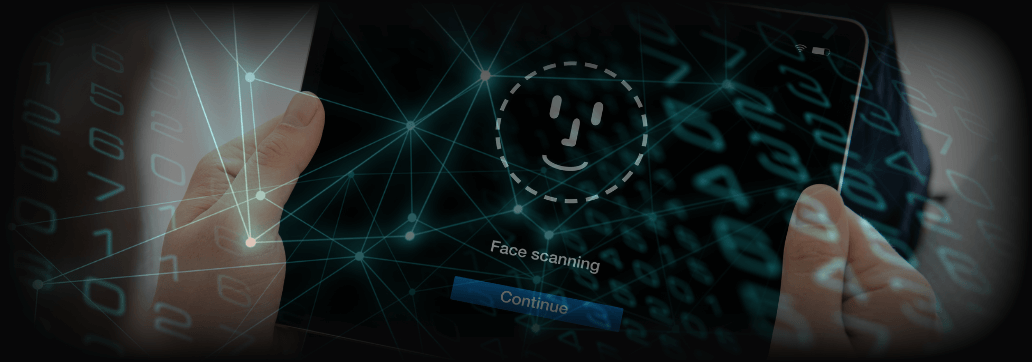
A Windows Hello Authentication Bypass Vulnerability Was Fixed by Microsoft
The Authentication Bypass Vulnerability Was Able to Let Threat Actors Spoof A Target’s Identity by Tricking the Face Recognition Mechanism.

Account security | SLOW READ
11+ PayPal Scams: How They Work and How to Protect Your Account
How to Safeguard your PayPal Account

One Platform. Total Security.
Experience the Power of Heimdal XDR the Unified Security Platform that Delivers Comprehensive Protection against Next-gen Threats