Contents:
A system administrator discovered that the Android TV box bought from Amazon had pre-installed malware. According to him, the box was reaching out to a whole list of active malware addresses.
Daniel Milisic is the person who found the malware and announced it on GitHub. He also wrote a script and instructions to assist users in neutralizing the payload and halting contact with the command and control server.
More about the Malware Discovered on the T95 Android TV Box
According to Milisic, the device had the ”CopyCat” Android malware on, malware that was previously reported to infect 14 million Android devices in an adware campaign.
Milisic originally purchased the T95 Android TV Box to operate the Pi-hole DNS sinkhole, which guards against unwanted content, ads, and dangerous websites without the need for software installation.
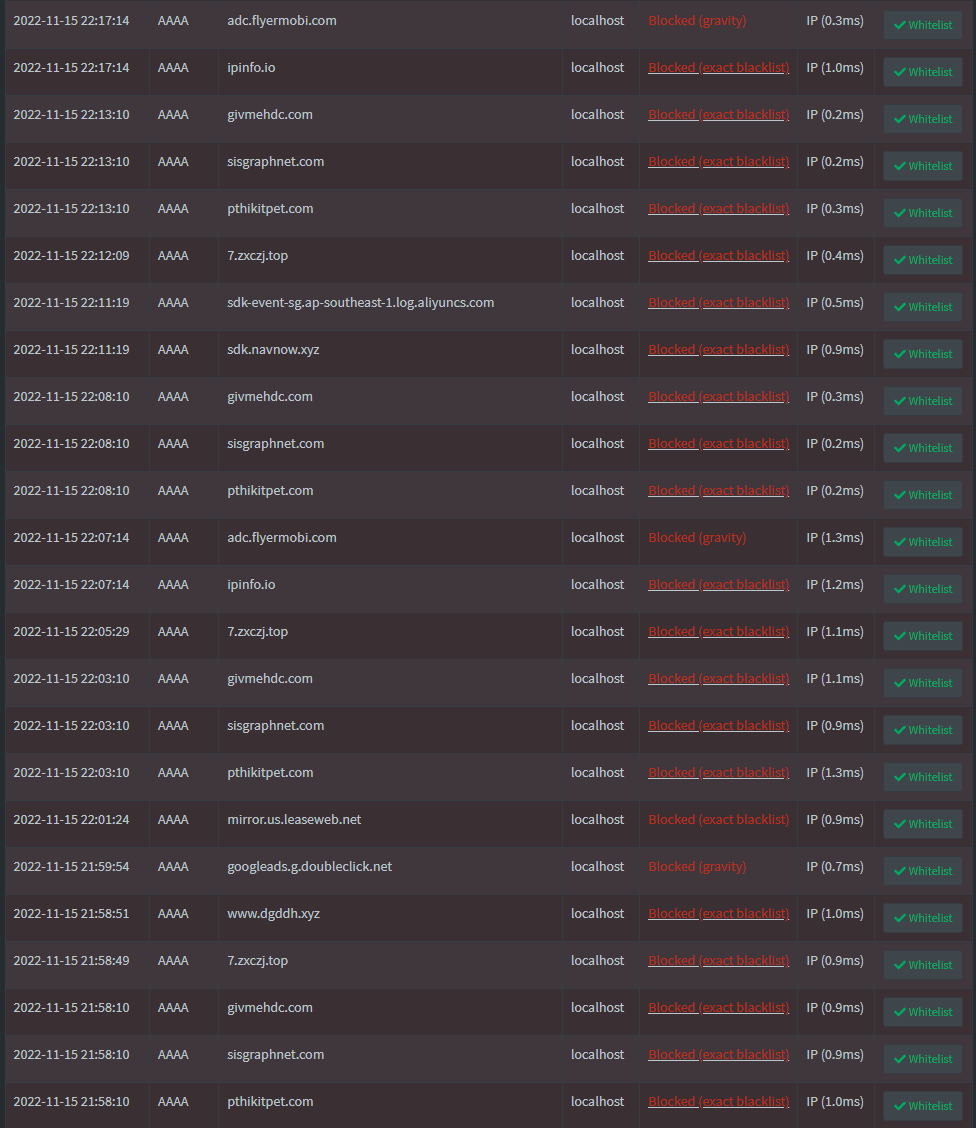
As he examined the DNS request in Pi-hole, he found that the device was trying to connect to a number of IP addresses linked to malware.
He also stated:
I found layers on top of layers of malware using ‘tcpflow’ and ‘nethogs’ to monitor traffic and traced it back to the offending process/APK, which I then removed from the ROM. The final bit of malware I could not track down injects the ‘system_server’ process and looks to be deeply baked into the ROM.
and revealed a list of the malicious domains that the T95 Android TV box attempted to connect to:
Safety Measures for T95 Android TV Box Users
It is still unknown whether only this device was impacted or if the malicious code affects all products from this model or brand.
To make sure their devices are clean and remove any potentially present virus, according to Bleepingcomputer.com, T95 users are advised to:
- Reboot into recovery mode or perform “Factory Reset” from the settings menu.
- Upon reboot, connect to ADB via USB or WiFi-Ethernet and run this script.
Then check if the malware was neutralized and run ”adb logcat | grep Corejava”, and make sure the chmod command failed to execute.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







