Contents:
In the cyber world, one of the most important things you can do is harden your system. System hardening is a key step in keeping your business safe and protecting your customers’ information. In this article, I will provide you with an overview of system hardening, its benefits, and how you can apply it to your business to strengthen your security.
Defining System Hardening
According to the National Institute of Standards and Technology (NIST), system hardening can be defined as a process intended to eliminate means of attack by patching vulnerabilities and turning off nonessential services.
One common goal of system hardening is to make it more difficult for attackers to access files or steal data. Other goals may include preventing attacks from taking control of a system, guarding against viruses and malware, and protecting against Distributed Denial of Service (DDoS) attacks.
There are many different ways to perform system hardening. The most important factor is determining which measures are necessary to protect your system and network from attack.
Types of System Hardening
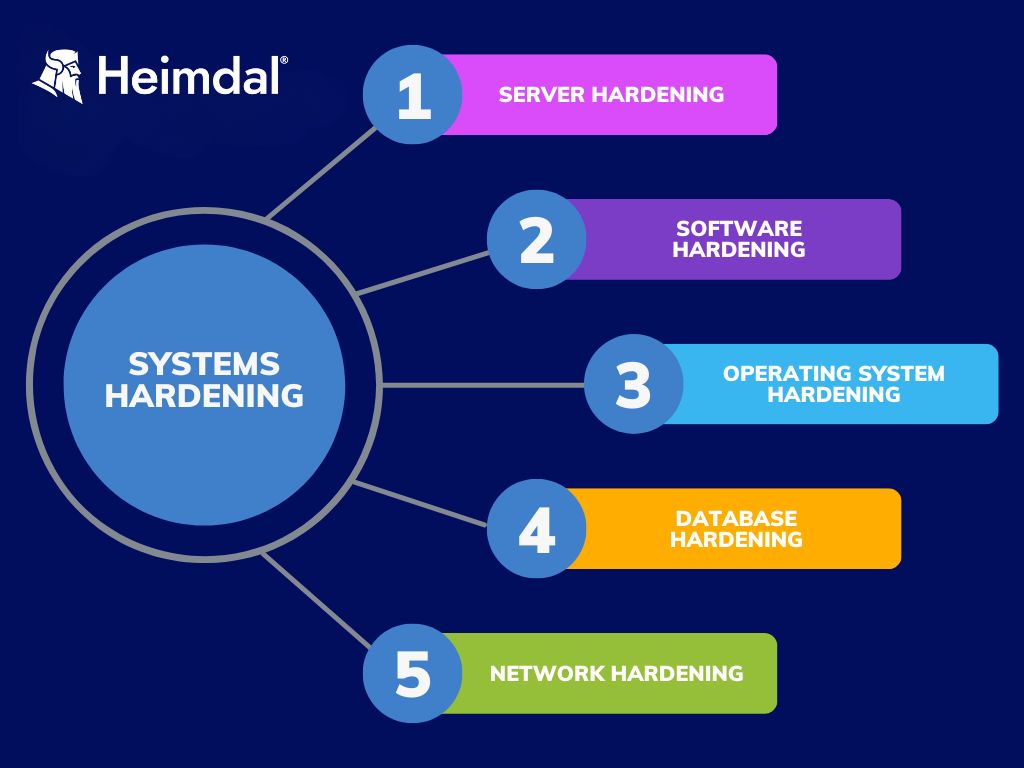
System hardening should be applied to every layer of a company’s IT infrastructure, ranging from servers to networks, and even endpoints. There are five categories into which the process can be divided:
- Server Hardening
- Software Hardening
- Operating System Hardening
- Database Hardening
- Network Hardening
Server Hardening
Server hardening is a broad technique that involves applying advanced security measures at the hardware, firmware, and software layers to secure a server’s data, ports, components, functions, and rights.
Some security measures applied when conducting server hardening are:
- Regularly updating and patching a server’s operating system;
- Updating third-party software that is necessary for the server’s functioning on a regular basis and getting rid of third-party software that doesn’t adhere to accepted cybersecurity standards;
- Developing a strong password policy;
- Locking the accounts of users after a certain number of failed login attempts;
Software Hardening
Software hardening, also known as application hardening, consists of updating or adding new security precautions to safeguard both native and externally supplied applications that are installed on your server.
While server hardening focuses broadly on securing the entire server system by design, software hardening focuses exclusively on securing the server’s apps. At a basic level, software hardening involves updating existing apps or patching them with new code to improve security.
Operating System Hardening
To secure a server’s operating system, operating system hardening entails applying patches and adopting cutting-edge security measures (OS). Having updates, patches, and service packs loaded automatically is one of the greatest ways to get the operating system into a hardened condition.
Because the operating system is theoretically a type of software, OS hardening is similar to application hardening. However, OS hardening secures the underlying software that grants those programs access to do specific things on your server, in contrast to application hardening, which focuses on securing standard and third-party applications.
Database Hardening
Database hardening refers to the process of safeguarding a digital database’s contents as well as the database management system (DBMS), the application that users use to store and process data in a database.
Database hardening can be divided into three main processes:
- Controlling and limiting user privileges and access;
- Database encryption;
- Disabling unnecessary database services and functions.
Network Hardening
Last, but not least, the last type of system hardening is network hardening. The process of “network hardening” entails safeguarding the fundamental communication architecture of numerous servers and computer systems utilizing a specific network.
A few examples of network hardening techniques are properly configuring and securing network firewalls, auditing network rules and access privileges, turning off specific network protocols and unused or unnecessary network ports, encrypting network traffic, and turning off network services and devices that are never or infrequently used.
Benefits of Systems Hardening
As we have seen so far, system hardening is no easy task. Although systems hardening takes ongoing work, your company will benefit significantly from your attention via the:
- Improved Security – probably the most obvious benefit. A smaller attack surface means a lesser chance of malware, system hacking, illegal access, or data breaches.
- Improved System Functionality – because programs that are irrelevant to a system’s functions are deleted throughout the process of hardening a system, hardened systems often perform better than other systems. The risk of system misconfiguration is decreased, and system compatibility is improved.
- Compliance and Auditing – a system becomes simpler after being “hardened,” which reduces the number of programs in the system. This makes compliance and auditing, which are typically difficult tasks, simpler.
Standards & Best Practices to Follow
Throughout the lifecycle of technology, system hardening is a crucial step that is called for under laws like PCI-DSS and HIPAA. Best practices for system hardening are maintained by the National Institute of Standards and Technology (NIST) and the Center for Internet Security (CIS). For example, the Special Publication 800-123 developed by NIST mentions some practices to follow when conducting system hardening, such as establishing a security plan and perform regular patch management.
A comprehensive system hardening strategy must include:
- A system hardening standard to adhere to (such as CIS, NIST, ENISA, etc.);
- A well-established plan based on the needs of your organization;
- System audits to manage your inventory and identify vulnerabilities in your system easily;
- Strong user rights and access controls: Remove unused privileges and accounts from the infrastructure.
- The implementation of an automated vulnerability scanning and patching tool to easily identify the missing patches, security updates, and misconfiguration when necessary.
Heimdal®’s Patch & Asset Management is a fully automated patching solution, tailor-made for your company’s needs. This technology gives you the flexibility to mitigate exploits, achieve compliance, address vulnerabilities, and schedule software installation anywhere in the world.
Additionally, you gain powerful vulnerability knowledge that enables you to quickly act on specific endpoints if risks are allowed to persist for an extended period of time. You will be updated constantly on what has already been repaired and the present liabilities in your environment.

Heimdal® Patch & Asset Management
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here...
Conclusion
Systems hardening is a term used to describe the process of modifying or increasing the resistance of a computer system against attacks. By understanding systems hardening, you can better protect your computer from becoming compromised by malicious actors. Additionally, systems hardening can help prevent unauthorized access to data and networks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








