Contents:
START (start.ru), a Russian media streaming platform, has confirmed the rumors that emerged on Sunday, August 28, about a data breach.
The cybercriminals extracted a 2021 database from START network which translates into account details of 7,455,926 users.
START assures via Telegram that the vulnerability has been fixed and the malicious actors no longer have access to their databases. However, the already stolen data is now scattered online starting on Sunday, August 28 when a 72GB MongoDB JSON dump was distributed over a social network.
What Information Contains the Stolen Data
The stolen database contains:
– email addresses
– phone numbers
– usernames.
Information is characterized by START as being unappealing to most cybercriminals as it is not useful for doing further harm.
Financial information, bank card data, browsing history, or user passwords have not been impacted because these details were not present in the database.
The stolen database contained records until September 22, 2021, so users that joined the platform after that moment should not be impacted. However, all START users are advised to change their login credentials.
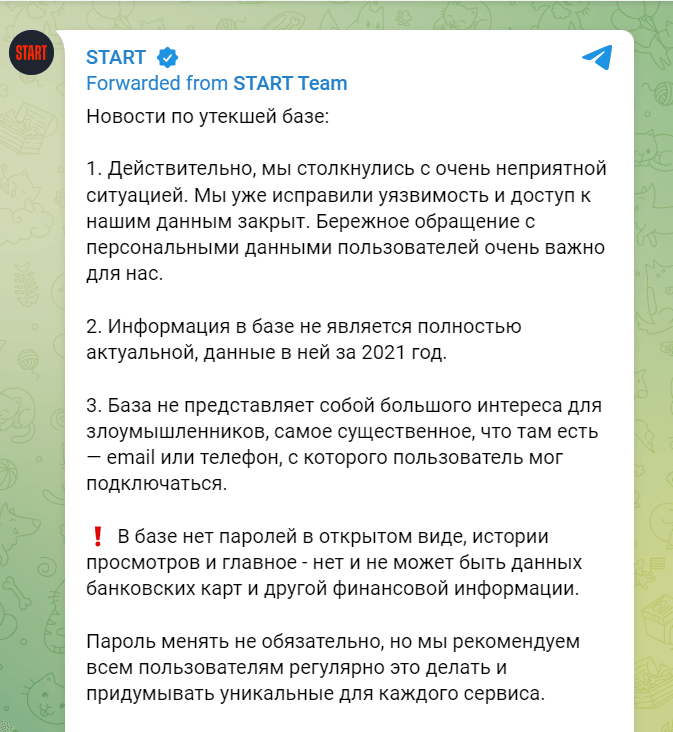
A certain amount of concern regarding the information contained in the stolen data is raised by the differences between START’s statement and the leaked dump. “The latter contains md5crypt-hashed passwords, IP addresses, login logs, and subscription details, which have not been included in the official statement from the platform.”, according to BleepingCooputer.
New Data Leak Rules for Russia
Moscow is trying to deal with the raised number of cyberattacks that target Russian online platforms by introducing new methods to protect users data.
The Ministry of Digital Development is planning to raise awareness regarding cybersecurity among organization leaders through a register of “unacceptable IT security practices”.
Earlier this month, the same ministry proposed establishing a fund that would be used to compensate victims of database leaks. The fund would be backed by fines imposed on the entities responsible for the security breaches.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







