Contents:
Cybercriminals have recently launched a marketplace named Industrial Spy, which sells information stolen from compromised organizations while also “spoiling” its customers with stolen data that’s free of charge.
Unlike traditional stolen data marketplaces, where data is used to extort enterprises and threaten them with GDPR fines, Industrial Spy promotes itself as a marketplace where organizations can buy their rival companies’ data to gain access to trade classified information, manufacturing diagrams, accounting reports, and client databases.
Nevertheless, it would not be exactly a surprise if the new marketplace is used to extort victims into buying their information in order to prevent it from being sold to other cybercriminals.
Industrial Spy Prices
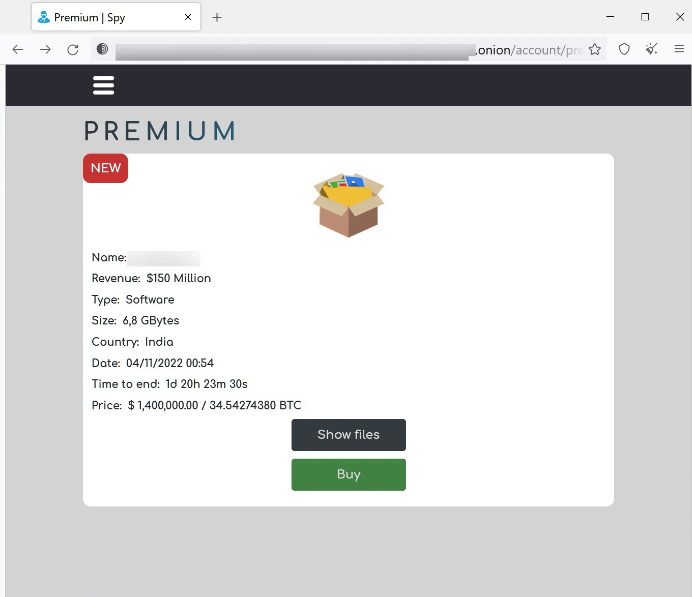
The recently launched marketplace offers a variety of data tiers, with “premium” stolen data packages costing millions of dollars and lower-tier data available for as little as $2 per file.
For example, in their premium section, Industrial Spy is currently selling data stolen from an Indian organization for $1.4 million in bitcoin.
On the other hand, a significant part of their data is sold as individual files, allowing hackers to buy the files they want for $2 each. Also, free stolen data packages are available on the marketplace, which will probably attract even more malicious actors.
Some of the businesses whose information is available in the “General” category are known to have suffered ransomware attacks in the past. As a result, the cybercriminals may have downloaded this information from ransomware groups’ leak sites in order to resell it on the Industrial Spy market.
According to BleepingComputer, MalwareHunterTeam security specialists were the ones to discover malware executables [1, 2] that create README.txt files to promote the site. When these malware files are executed, they generate text files in every folder on the machine, including a description of the service as well as a link to the Tor website.
There you can buy or download for free private and compromising data of your competitors. We public schemes, drawings, technologies, political and military secrets, accounting reports and clients databases.
All these things were gathered from the largest worldwide companies, conglomerates, and concerns with every activity. We gather data using a vulnerability in their IT infrastructure.
An investigation conducted by BleepingComputer shows that these executables are being distributed via other malware downloaders that are frequently camouflaged as cracks and adware.
For example, the STOP ransomware and password-stealing malware, which are frequently spread via cracks, are installed alongside the Industrial Spy executables.
Furthermore, according to VirusTotal, the README.txt files are observed in various collections of password-stealing trojan logs, suggesting that both programs were run on the same machine. This shows that the Industrial Spy website’s creators probably collaborate with adware and crack developers to distribute the program that advertises the marketplace.
While the site isn’t very popular yet, businesses and security professionals are recommended to keep an eye on it and the information it claims to sell.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security