Contents:
The social engineering techniques used by callback phishing operations have developed: while they still use typical bogus subscription lures for the initial phase of the attack, they now flip to attempting to assist victims in dealing with a virus or hack.
Victims are infected with a malware loader, which drops additional payloads such as remote access trojans, spyware, and ransomware.
What Are Callback Phishing Attacks?
Callback phishing attacks are email campaigns that masquerade as high-priced subscriptions, causing the recipient to become confused because they never subscribed to these services.
According to Bleeping Computer, the email includes a phone number where the receiver can learn more about this ‘subscription’ and quit it. Unfortunately, this results in a social engineering operation that installs malware on victims’ devices and potentially ransomware attacks.
The current campaigns are aimed at users in the United States, Canada, the United Kingdom, India, China, and Japan, as shown in a new report published by cybersecurity researchers at Trellix.
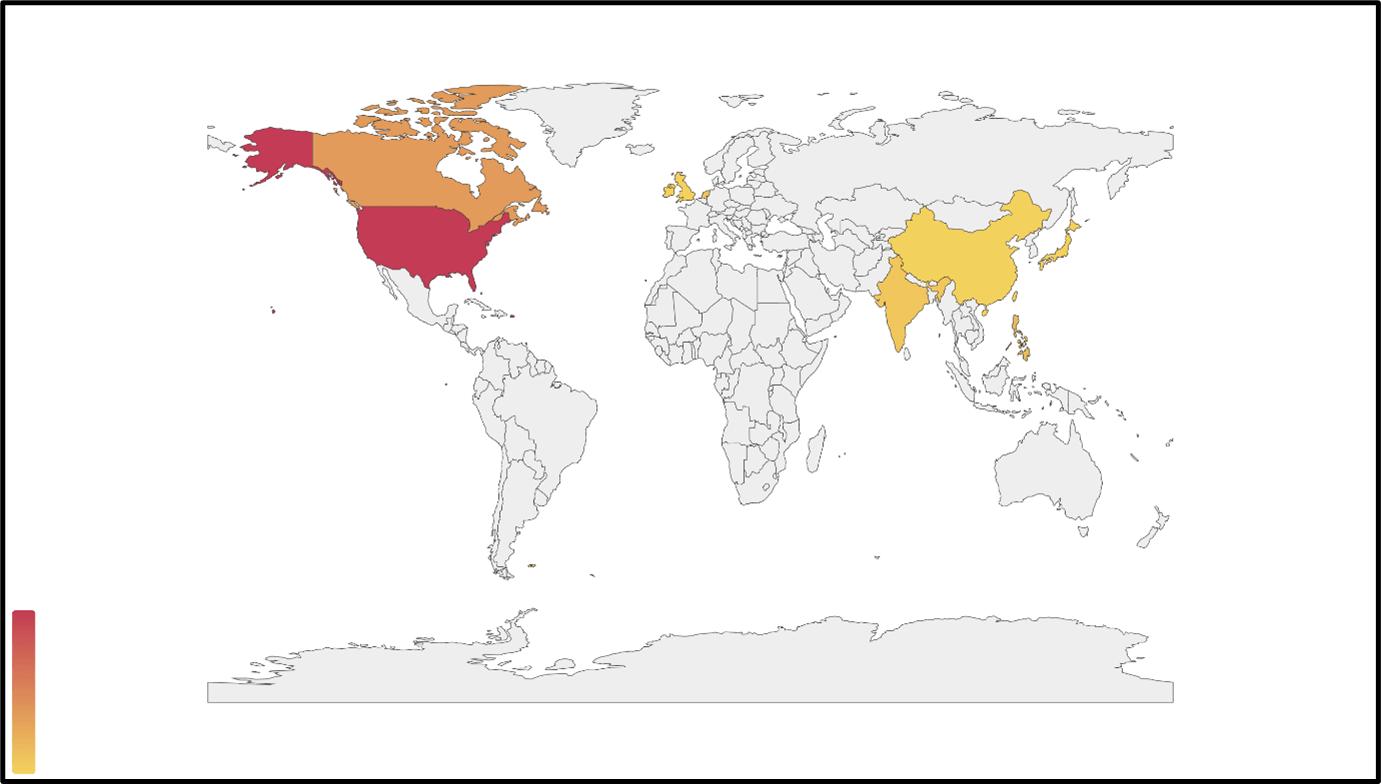
Heatmap of the latest attacks (Source)
BazarCall – The First Callback Phishing Attack Operation
Callback phishing attacks first emerged in March 2021 under the name ‘BazarCall‘, when threat actors began sending emails posing as a subscription to a streaming service, software product, or medical services organization, including a phone number to call to cancel the payment.
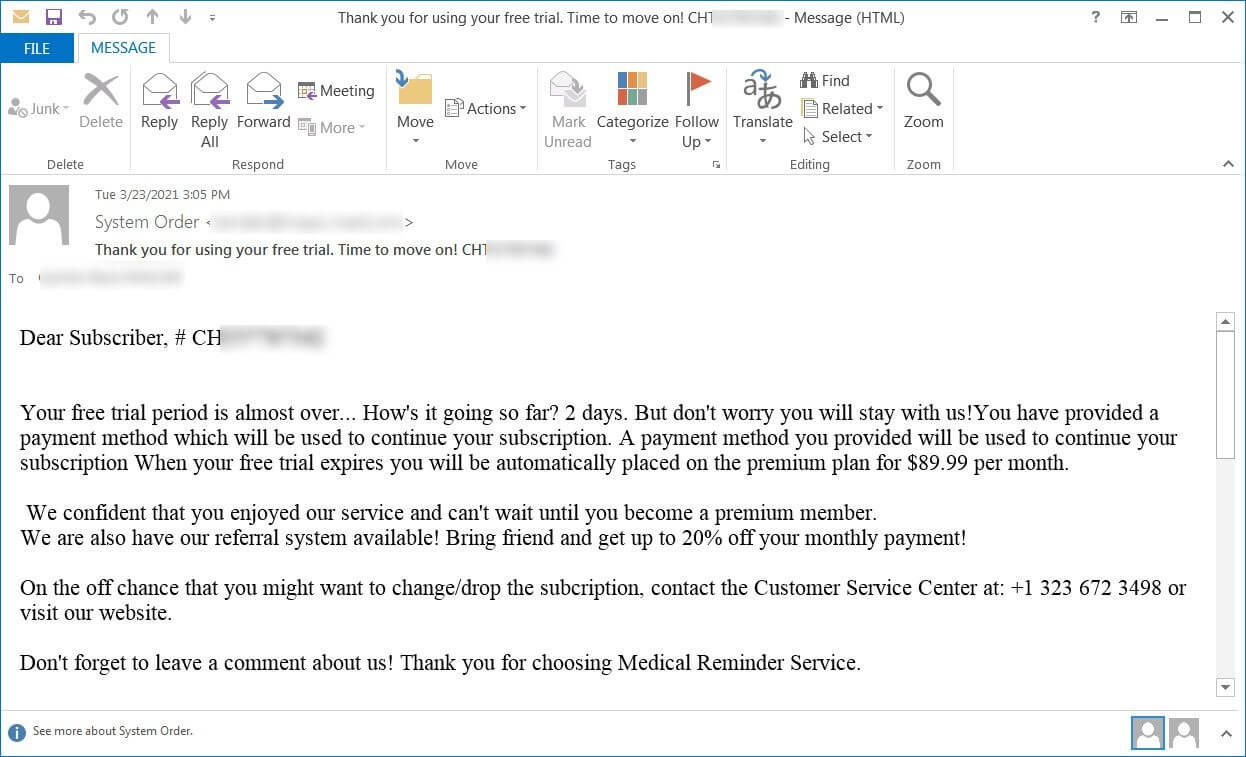
Original BazarCall email (Source)
When a victim dialed the number, the threat actors guided them through a series of steps that resulted in the download of a malicious Excel file that installed the BazarLoader malware.
BazarLoader would then grant remote access to an infected device, allowing initial access to corporate networks before progressing to Ryuk or Conti ransomware attacks.
Callback phishing assaults have become a significant concern over time, as they are currently used by several hacking groups, including the Silent Ransom Group, Quantum, and the Royal ransomware/extortion operations.
The Operation’s Social Engineering Techniques Have Evolved
Although the bait in the phishing email stays the same, the social engineering technique changed: the attackers now use an invoice for a payment made to Geek Squad, Norton, McAfee, PayPal, or Microsoft.
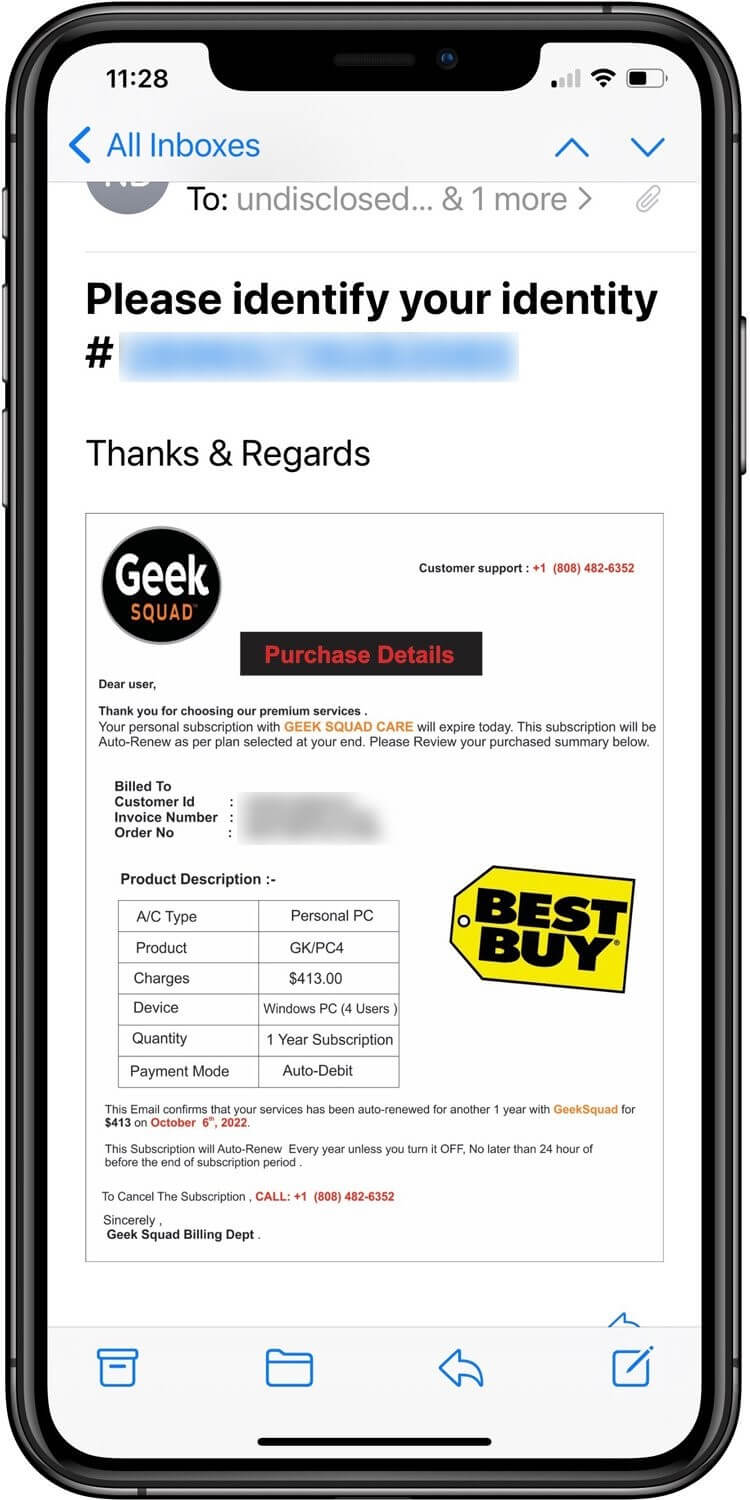
Example of new callback phishing attack email (Source)
The recipient is asked to supply the invoicing details for ‘verification’ after calling the fraudster at the provided number. The scammer then claims that the system has no matching entries and that the email the victim received was spam. The victim is then alerted by the fake customer service representative that the spam email may have caused a malware infection, suggesting to put them in touch with a technical expert.
After some time, a different fraudster contacts the victim and redirects them to a website where they download malware disguised as anti-virus software.
Another technique employed in PayPal-themed phishing attacks is to question the victim if they use PayPal and then falsely check their email for compromise, indicating that their account was accessed by eight devices located all over the world.
In their bogus security software subscription renewal efforts, fraudsters claim that the victim’s laptop’s pre-installed security program had run out of protection and had been automatically renewed.
In the end, the fraudster leads the victim to a cancellation and refund page, once again a malware-dropping website.
All Devices Are at Risk of Remote Control
According to the same report, the majority of these new campaigns push the installation of the ScreenConnect remote access tool by launching a ClickOnce executable named ‘support.Client.exe’.
In certain incidents, security analysts noticed scammers opening bogus cancellation forms and asking victims to fill them out with their personal information.
The attacker can also show a fake lock screen and make the system inaccessible to the victim, where the attacker is able to perform tasks without the victim being aware of them.
Finally, in order to collect the reimbursement, the victim is directed to their bank account, where they are misled into sending money to the fraudster instead.
This is achieved by locking the victim’s screen and initiating a transfer-out request and then unlocking the screen when the transaction requires an OTP (One Time Password) or a secondary password. The victim is also presented with a fake refund successful page to convince him into believing that they have received the refund. The scammer may also send an SMS to the victim with a fake money received message as an additional tactic to prevent the victim from suspecting any fraud.
However, losing money is just one of the issues that infected users may have because the threat actors may any moment launch new, more dangerous malware that will spy on them for a longer period of time and steal highly sensitive data.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








