Contents:
Every day, new cyberthreats emerge. Malicious actors frequently use different methods and weaknesses to steal data, install ransomware, or disable services. Cybersecurity experts must continue to develop new defenses against this expanding threat or risk losing vital assets for their company.
A new idea that has developed from Secure Access Service Edge is known as Security Service Edge (SSE), a name that was invented by Gartner (SASE). Read on to gain a complete grasp of SSE, why it’s significant in the cybersecurity landscape, the advantages it offers, how it differs from SASE, and how to address its issues in order to stay at the forefront of technology.
What is Security Service Edge (SSE)?
As defined by Gartner, Security Service Edge (SSE) is a combination of cloud platforms that are specifically designed to supply network security services. SSE can be thought of as a subset of the Secure Access Service Edge (SASE) framework because of the architecture’s clear emphasis on security services.
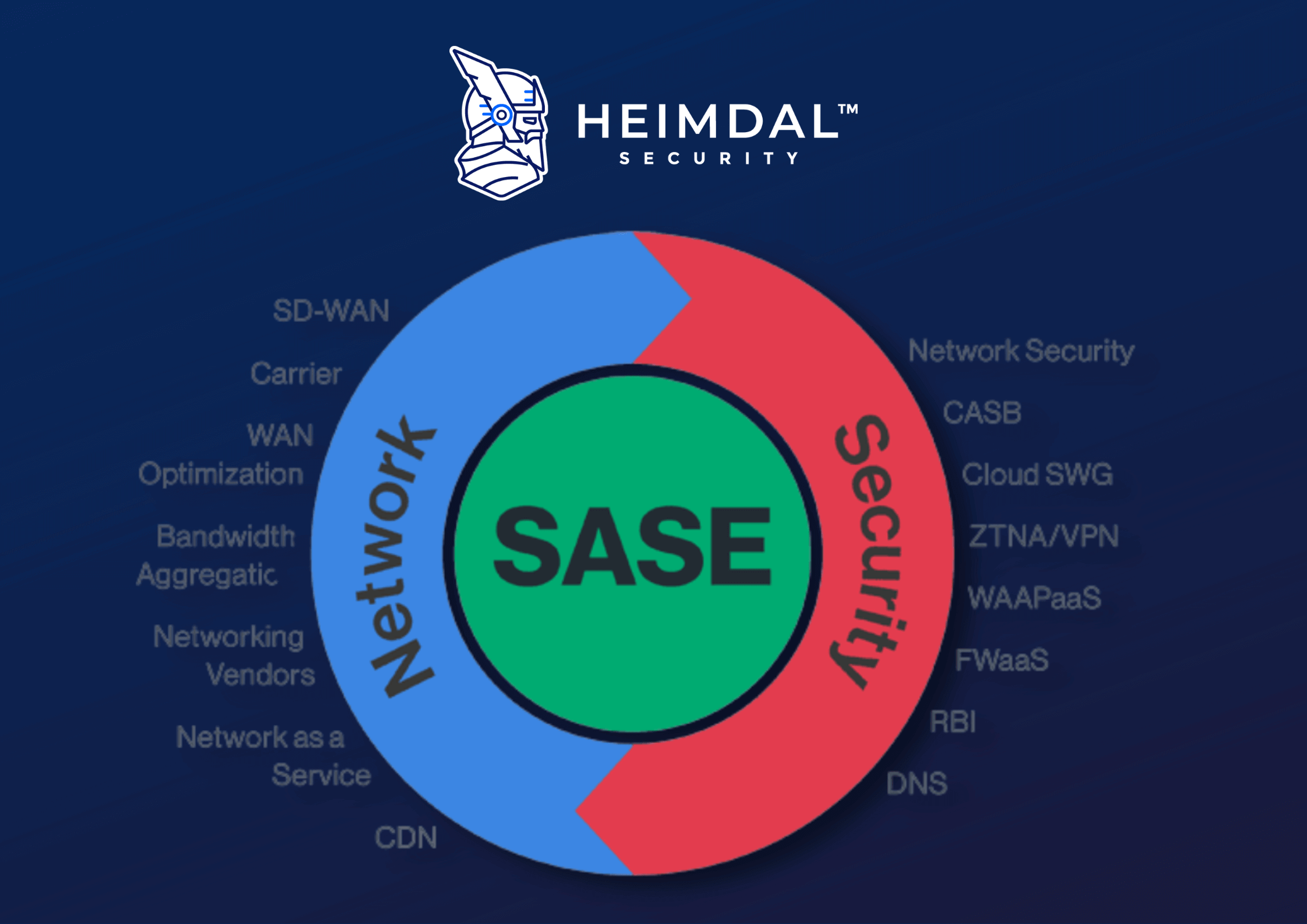
SSE offers safe access to online, software-as-a-service, and private applications while keeping hackers out and sensitive data in. This hybrid, three-in-one spear strategy enables a business to integrate threat protection, security management, and access control into a single network security mechanism, regardless of the location of the application or data.
To put it short, SSE is not a standalone product; rather, it is SASE’s security components reimagined as a unified, cloud-centric approach.
SSE Advantages
An organization gains from a strong SSE solution in a number of ways:
- Safety and security transparency and accuracy wherever people work
- Decrease in complexity
- Better user experience
- Coordination of strategy and functioning
- Greater adaptability
- Cost-cutting
As it merges several services into a single platform, SSE shows value right away. As a result of the probable removal of additional services, complexity is reduced while cost savings are also made possible. Zero Trust Network Access (ZTNA), for instance, eliminates the requirement for VPNs to access applications. Due to SSE’s improved performance, a decrease in complexity also improves user experience.
Security may more effectively defend the network without slowing it down by combining functionality and strategy. A network needs constant, real-time security to remain safe because malicious actors are constantly hunting for vulnerable points to exploit.
Components of Security Service Edge
SSE is consisting of three essential parts: Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), and Cloud Access Security Broker (CASB). Each element adds a unique set of capabilities to the table, and when combined, they provide a strong security solution.
Zero Trust Network Access (ZTNA)
Incorporating the principle of least privilege (POLP), a Zero Trust Network Access (ZTNA) grants a user safe access to internal apps depending on their specific access context. This SSE component focuses on identity and access management (IAM), utilizing features like single sign-on (SSO) and multi-factor authentication (MFA). The ZTNA should provide both agent and agentless deployment for the most efficient SSE setup.
Cloud Access Security Broker (CASB)
Developed by Gartner, the Cloud Access Security Brokerage profile proposes a mediator between users and providers of cloud services. By enforcing policies, a Cloud Access Security Broker (CASB) offers data and threat protection in the cloud, enabling protection for any device, at any time, and any place. A multi-mode next-gen CASB architecture is suggested for the most efficient SSE setup as it offers dynamic scalability with agent-based, agentless, and API-based approaches.
Secure Web Gateway (SWG)
A Secure Web Gateway (SWG) guards against malware and upholds corporate rules. In addition to preventing data leakage, it uses content inspection checks to safeguard user-initiated communications. Additionally, application controls are included.
SWGs can be implemented by either employing a cloud proxy or by installing the SWG directly on the end device. The SWG must offer real-time protection for the SSE setup to be most effective.
There is frequently confusion between the phrases Secure Access Service Edge (SASE) and Security Service Edge (SSE). Despite the fact that they may sound similar, they are not the same. SASE stands for the more comprehensive structure that many IT executives want to use. It’s the idea of mixing contemporary safe access services (such as SD-WAN, content distribution, and QoS) with contemporary network optimization services (ZTNA, SWG, CASB, etc.). SSE is, to put it plainly, one-half of the SASE framework.
In order to enable a quick, secure transition to the cloud, Gartner initially introduced the Secure Access Service Edge (SASE) back in 2019. It merged networking and security technologies into a single cloud-based platform. According to Gartner, SASE capabilities are provided as a service based on the identity of the entity, real-time context, enterprise security/compliance regulations, and continuous risk/trust assessment during the sessions. People, groups of people, devices, apps, services, IoT systems, and edge computing locations can all have identities linked with them.
How to Choose the Best SEE Platform?
Avoid using multiple vendors
You can avoid issues like complicated policy management, managing various user interfaces, and potential architectural conflicts by working with a single vendor.
Cloud-delivered SSE platforms are a higher priority than hardware-based ones
Not all SSE services are entirely cloud-based. By thoroughly examining each service and making sure it is supplied via the cloud, you can lower appliance expenses, use the cloud to expand automatically as needed, and provide a better user experience because there are more points of contact (some SSE services are supported by the AWS and GCP infrastructure).
Choose vendors that better enable simple regulations
SSE capabilities are offered by many SSE suppliers via bolt-on purchases. Once this occurs, it may take several years until those technologies are truly integrated. When it comes to policy, this may give IT managers issues. SSE systems that are fully integrated and utilize the same cloud result in simplified administration.
Select an SSE platform with inspection ZTNA
IT departments must be able to see what apps are accessed by staff members and outside users, what they install, and what actions they take when using an app. IT security teams won’t be able to get this crucial visibility via zero trust network access (ZTNA) services that lack inspection. What is more, they will fail to modify access privileges in response to context-based modifications.
Opt for an SSE platform with Digital Experience Monitoring (DEM)
User experience should not be hampered by security. Network operating systems can monitor hop-by-hop analytics for users connecting to SaaS and internal apps using DEM technologies. By identifying the precise source of the user interruption, they are able to better understand the user experience and decrease the average time to resolve support requests.
Wrapping Up…
Thanks to enhanced security features and services, Security Service Edge platforms will be future-proof as enterprises adopt SSE as a single platform. Digital experience management, which enables IT to immediately discover technical difficulties in the user-to-cloud app link, is one tool that is starting to move into SSE.
In addition, network service aggregation and an SSE platform are important, as stated by the SASE architecture. This offers solid support for multi-cloud connectivity, local branch office accessibility, and SD-WAN services communication. As the cloud environment for your company evolves, you can guarantee capacity for expansion without increasing complexity by concentrating on SASE service providers who are also pushing SSE development.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








