Contents:
These past few days security researchers from the Bitdefender Cyber Threat Intelligence Lab have detected a new malware strain known as Scranos which aims at stealing passwords, financial information, and other sensitive data from home users and organizations across the globe. First identified in November 2018, with a massive spike in December and January, specialists continued to track it and raised a red flag in the past months when it was extremely active.
This attack looks like a work in progress, with many components in the early stage of development,
researchers described it. Dubbed “Scranos”, this newly rootkit-based malware appears to be continuously evolving, developing new components or making minor improvements to the old ones. Unlike other types of malware, rootkits are notoriously difficult to detect in the first place, persistent and complex threats out there.
How does the infection process happen?
The attack vector is usually cracked, pirated software or Trojanized application disguised as legitimate software you may be tempted to download and install on your computers such as (video) drivers, software programs, or even security products. One of the main components of rootkits is the dropper, which is an executable program or file that installs the rootkit. In this spam campaign, the dropper acts like a password stealer and installs a digitally-signed rootkit driver. According to researchers, the digital signature of this driver seemed to be issued by a Chinese company, and hackers may have obtained the original digital code-signing certificate illegally or compromising it. Once the dropper is installed, it tries to communicate with a malicious Command-and-Control (C&C) server (which is controlled by the attacker) and downloads one or more payloads.

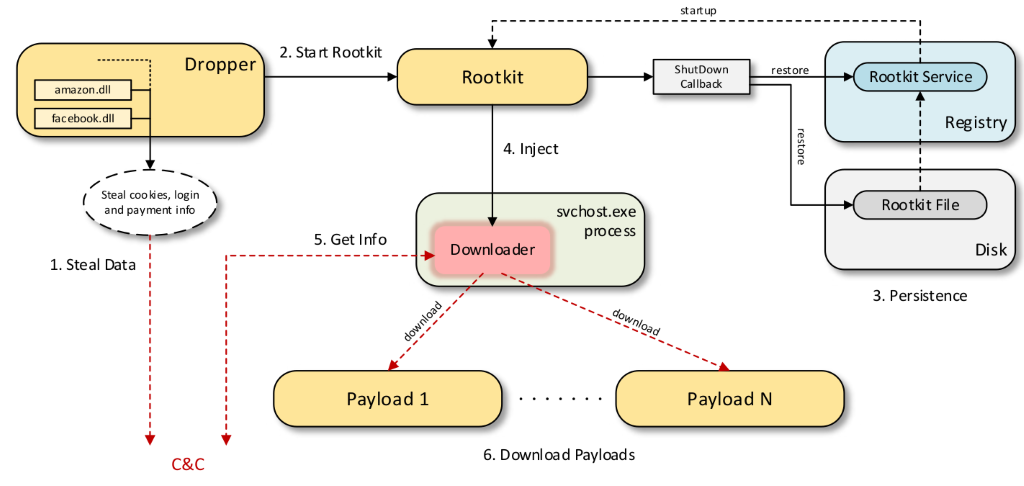 Image credits: Bitdefender Labs Security researchers from Bitdefender also shared some of the most important components of the Scranos malware and what can perform:
Image credits: Bitdefender Labs Security researchers from Bitdefender also shared some of the most important components of the Scranos malware and what can perform:
- Steal users’ payment information from popular sites like Facebook, Amazon or Airbnb where the victim has shared sensitive data
- Extract cookies and login credentials from Chrome, Chromium, Mozilla Firefox, Opera, Microsoft Edge, Internet Explorer, Baidu Browser and Yandex Browser
- Inject JavaScript adware in browsers, as well as exfiltrating browser history
- Install various Chrome and Opera extensions with the malicious purpose of launching adware
- Send phishing messages to the victim’s Facebook friends containing malicious files.
- Steal login and password data for the user’s account on Steam
- Subscribe users to different YouTube channels
- Installing and running malicious payloads
More technical details provided by security researchers can be found in the full paper. Who’s been targeted? While the spam campaign was originally spotted in China, according to the telemetry collected by the Romanian security researchers, in the last months, the Scranos malware started to spread to other countries too. However, it’s been “more prevalent in India, Romania, Brazil, France, Italy, and Indonesia.” 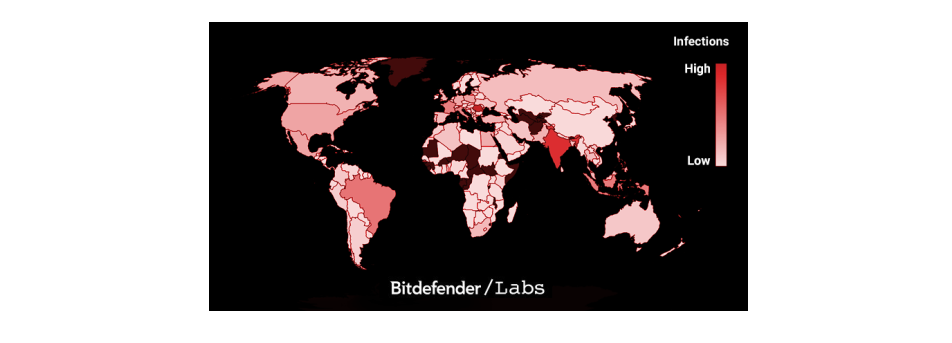 This type of attack stands out because of its rootkit capabilities, and security experts pointed out that “rootkit-based malware is rare, and accounts for less than 1% of the malware they see daily.” More than that, it is a dangerous and significant malware with multiple functionalities (rootkit, backdoor, info stealer, adware) which can provide cybercriminals lots of creative methods to spread infection.
This type of attack stands out because of its rootkit capabilities, and security experts pointed out that “rootkit-based malware is rare, and accounts for less than 1% of the malware they see daily.” More than that, it is a dangerous and significant malware with multiple functionalities (rootkit, backdoor, info stealer, adware) which can provide cybercriminals lots of creative methods to spread infection.
How to remove the infection?
Rootkits are probably the most difficult types of malware to remove from a computer because these infections root themselves deep into the victim’s machine, are sneaky and can also bypass antivirus products. Before you start the removal process, we highly recommend backup all your valuable data, because there’s no telling how the rootkit will react. Chances are it can have strong defensive measures that might wipe your computer or make it unfunctional. If you’re a victim of Scranos, you should follow these steps that can help you remove the infection:
- Kill processes running from the Windows temp folder path and delete those files which are detected as malicious. If you don’t know how to do it, use this guide to learn more.
- Open Task Manager and stop the rundll32.exe process which represents a security risk and could harm your computer
- Reboot your PC to Safe Mode to Networking to limit the access of the rootkit. This step-by-step guide will show you how to perform this action.
- Install a rootkit removal tool like Malwarebytes Anti Rootkit which can scan, detect and eliminate the nasty rootkit.
- Delete suspicious extensions from your browsers and clear your browsing history.
Also, make sure you follow the detailed removal instructions shown by the Romanian security researchers.
Apply these security measures to prevent the Scranos rootkit-enabled malware from infecting your computer
It goes without saying that prevention is always the best cure, so applying these actionable security measures might prevent a rootkit infection from happening. Rootkit malware is one of the most challenging and nasty threats faced by home users and organizations, so we want to raise awareness about them, as well as to learn how to better detect and prevent these attacks. Here’s what you should do right now:
- Do not download or install pirated software, because this type of malware is mainly distributed via programs, which are at a high risk of infection. Instead, use valid and reliable software programs and install them from trusted sources.
- Change all your current passwords ASAP and make sure you use only strong and unique ones. We recommend reading this password security guide that will teach you how to manage passwords like a pro and make them hard to be hacked.
- Outdated software remains one of the biggest sources of malware infection, so we keep reminding you that software updates are critically important. Like many other security pros and companies, we advocate for applying updates as early and regularly as possible. You can use our Heimdal™ Free security product to keep your apps up to date automatically and silently.
- Remember to do a backup of all your essential data on external sources such as a hard drive or in the cloud (Google Drive, Dropbox, etc.). You can learn how to do that by reading our guide.
- Be cautious about phishing attacks which continue to be a serious and risky threat, with more and more phishing emails flooding into users’ inbox and luring them to click on malicious files of attachments. Here’s a more in-depth look at how phishing works and what can you do to prevent it.
- Before you install any browser extension, pay attention to the rating and read the users’ reviews, because some extensions can compromise your safety and privacy. If you are using Chrome, you should check out this list of 10 Chrome extensions that will enhance your online safety.
- If you’re using an Antivirus solution, make sure is a reliable one. Better than that, consider adding multiple layers of protection, because new malware is getting more and more sophisticated and harder to be detected by traditional AV. Use proactive cybersecurity software like our Heimdal™ Premium Security Home, which provides complete and all-in-one protection.
- If you are an organization, it is safer to restrict admin rights on computers for employees and limit access only to specific data they need and use. Also, restrain the authority to install software programs and encourage them to report back to you when they notice/receive suspicious emails from untrusted sources.
- Organizations NEED to start investing in cybersecurity training for their employees and help them become more resilient to all types of threats. The same thing applies to home users who should train themselves not to be an easy target for cybercriminals.
- We are strong believers that education is key to be safer on the Internet and protect your digital assets. If you want to learn how to better detect online threats and have a stronger defense against them, you can check our free educational resources such as the Cyber Security for Beginners course, or The Daily Security Tip which offer actionable tips you can apply.
Stay safe!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








