Contents:
Threat actors exploited a compromised Kubernetes container to attempt privilege escalation into an AWS account.
Operation Scarleteel, as it was later dubbed, did not only result in a cryptojacking attack. Hackers also attempted to steal source code and credentials.
Operation Scarleteel Explained
The first step was to exploit a public-facing app in a self-managed Kubernetes cluster. The cluster was hosted inside an AWS cloud account.
Then the hackers deployed an XMRig coin miner. Apart from the financial reasons, the cryptojacking attack was considered a diversion, since the operation did not stop there. Further on, threat actors used a script to extract account credentials. The adversaries succeeded to enumerate AWS resources and obtain credentials of another identity. They used the credentials to perform a lateral movement.
The stolen credentials were then used to perform AWS API calls to gain persistence by stealing further credentials or creating backdoor users and groups in the company’s cloud environment. These accounts were then used to spread further through the cloud environment.
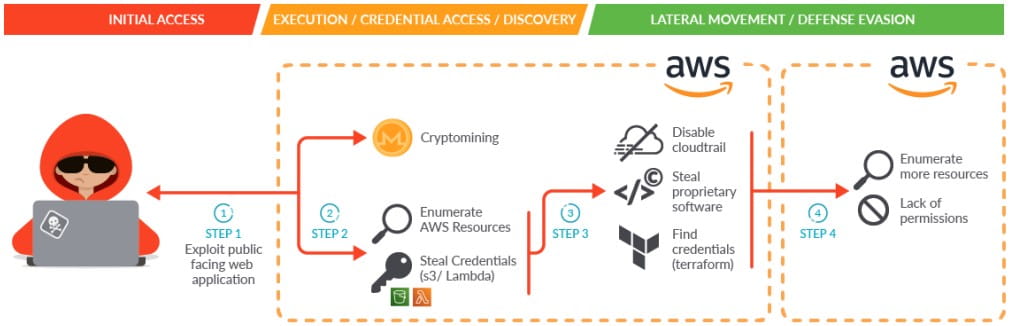
As a result, they managed to steal proprietary software and also obtained the credentials of an IAM user which was related to another AWS account.
When trying to move laterally again and repeat the attack, hackers failed to enumerate resources. This happened because all their AWS API requests were rejected due to a lack of permissions.
To evade detection, threat actors disabled CloudTrail logs.
Cloud-Based Infrastructure Security Measures
Developers rely more and more on cloud services for their infrastructure and data, so hackers also followed. According to cyber researchers, cloud attacks raised by 56% in 2022, while their complexity also increased by 59%.
Operation SCARLETEEL is proof of how a vulnerability in the cloud environment can lead to network infiltration and data theft. So here are some security best practices you should enforce to protect your cloud environment:
- First of all, never miss a patch.
- Enforce IMDS v2 instead of v1 to avoid unauthorized metadata access.
- Enforce the principle of least privilege.
- Only permit read-only access to resources that may contain sensitive data.
- Disable any permissions that you don`t currently need or use.
- Use AWS KMS, GCP KMS, and Azure Key Vault key management services.
And since the attack could not have been possible if it wasn`t for a compromised container, also make sure to enforce best practices to secure your containers.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









