Contents:
Brute force attacks are a persistent security threat that has evolved over the years as technology advances. In this article, we’ll explore what a brute force attack is, its modus operandi and variants, and what prevention strategies you can use to protect your data.
What Is a Brute Force Attack?
A brute force attack is a type of cyberattack where the attacker attempts to gain access to a computer system or network by guessing passwords or personal identification numbers (PINs). Sometimes, attackers use automated software to make guessing easier and faster.
A brute force attack is also called a cryptanalytic attack since it relies on cryptologic functions to ‘crack’ the cipher and infiltrate the machine.
Brute force attacks can be very successful if the attacker has enough time and computing resources. However, they are also very difficult to pull off and usually take a long time to complete. As such, they are not commonly used by attackers except in very specific circumstances.
How Does a Brute Force Attack Work?
Many believe BFAs to be crude, rudimentary, and rough. Nothing could be further from the truth. They rely heavily on password and passphrase dictionaries and on cryptologic ‘magic tricks’ that allow the malicious actors to guess the user’s credentials.
Brute force attacks usually follow a common modus operandi: the attacker tries to log in to a user account by using different combinations of username and password until he or she finds the right combination. If the attacker is successful, he or she can then access the victim’s accounts and data.
Brute force attacks can be online and offline. Online brute force attacks occur when the attacker has direct access to the victim’s system, while offline brute force attacks take place when the attacker tries to guess passwords from a database that has been compromised.
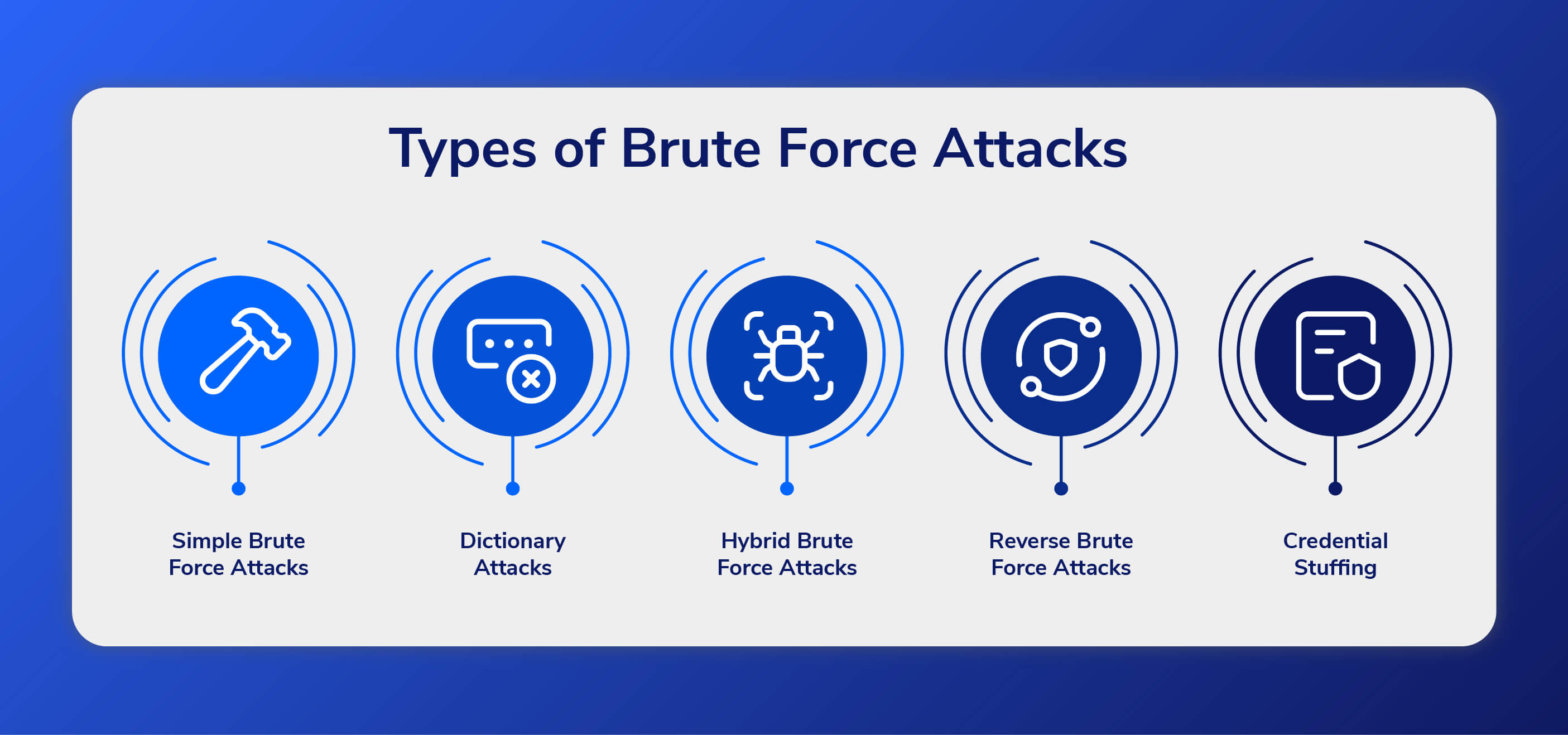
Brute Force Attack Types
There are several different types of brute force attacks, each with its own specific goals and methods:
Simple Brute Force Attacks
This type of attack tries every possible combination of characters in an attempt to guess the password. This can be a very time-consuming process, but modern computing power makes it feasible for attackers.
Dictionary Attacks
These are the most common type of brute force attacks, where the attacker uses a list of commonly used passwords and attempts to guess them.
Dictionary attacks are so named because they involve hackers going through dictionaries and replacing words with symbols and numbers. Compared to more recent, more successful attack strategies, this type of attack is usually time-consuming and has a relatively low chance of success.
Hybrid Brute Force Attacks
When a hacker uses both a dictionary attack method and a simple brute force attack, the result is a hybrid brute force attack. Once the hacker has a username, they can use dictionary attacks and simple brute force techniques to find the account login information.
The attacker starts with a list of potential words, then experiments with character, letter, and number combinations to find the correct password. This approach allows hackers to discover passwords that combine common or popular words with numbers, years, or random characters, such as “SanFrancisco123” or “Toyota2020.”
Reverse Brute Force Attacks
A reverse brute force attack is when an attacker uses a known password or pattern and tries to find a username or account number to gain access to a system. This is in contrast to a traditional brute force attack, where the attacker tries various combinations of characters in an attempt to discover the password.
Credential Stuffing
A credential stuffing attack makes use of stolen login credentials on numerous websites. Credential stuffing is effective because people frequently reuse their login names and passwords. As a result, if a hacker gains access to a person’s account with an online shop, for example, there is a high likelihood that the same credentials will also grant access to that person’s online bank account.
Another classification would be that of prolonged versus distributed brute force attacks:
Prolonged Brute Force Attacks
The targeted machine will be assailed over a long period. It can vary from several days to a couple of weeks, depending on the user-pass pair strength, pair length, computational speed, code-cracking method, and countermeasures. BFA research has revealed that a single machine can sustain between 50 and 100 brute-force attacks per day. Also, the access requests can be launched from more than one IP address. Prolonged brute-force attacks have increased chances of being detected.
Distributed Brute Force Attacks
In the case of distributed brute-force attacks, login attempts will be in the form of short and highly ‘concentrated’ bursts (e.g. 40 login attacks initiated from a single IP, distributed over 3 to 4 minutes). Conclusions: decreased detection rate and increased chances of success.
Brute Force Attack Prevention
To prevent brute force attacks, it’s important to use strong passwords that are hard to guess. Avoid using easily guessed words like your name or birthday. Instead, use a mix of upper and lowercase letters, numbers, and special characters.
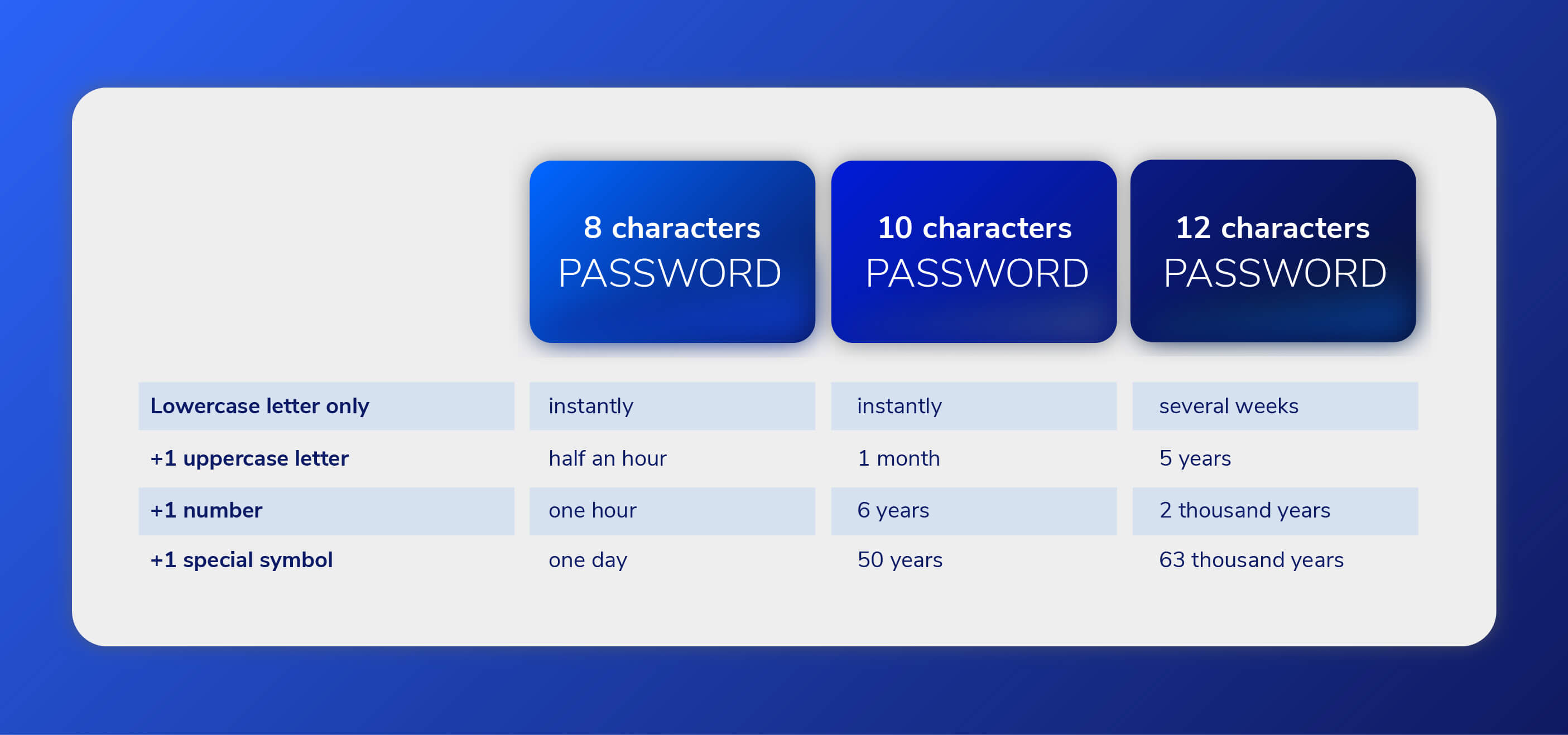
Another prevention strategy is to rate-limit login attempts so that an attacker cannot just keep trying different passwords indefinitely. Additionally, account lockout policies can be put in place so that accounts are automatically locked after a certain number of failed login attempts.
Two-factor authentication can also make brute force attacks much more difficult to pull off because even if an attacker knows the correct username and password, they will still need access to the second factor (usually a physical token or code sent via SMS) in order to log in.
What else could you do?
Enable Network Level Authentication
NLA will add an extra layer of protection since it requires the user to authenticate themselves before the session initiation. To do that, open Control Panel, head to System and Security and click on System.
Go to Remote Settings, click on Remote, and then on Remote Desktop. Highlight the option “Allow connections only from computers running a remote desktop with Network Level Authentication.”
Manually block TCP port 3389
Head to Control Panel, select System and Security, and click on Windows Firewall. Head to Advanced Setting >> Inbound Rules, click on New Rule, and then choose your Port. When you’re done, click Next. Highlight TCP and then select Specific Local Ports. Type in 3389. Click on next, type in a name for your newly created rule and then click on Finish.
Enforce 2FA for RDP requests
Tokens can be used to enforce two-factor authentication for RDP connections. Refer to Microsoft’s documentation on 2FA rule enforcement for setup and configuration.
Determine if your endpoint has been subjected to a brute force attack
According to Microsoft, machines assaulted and/or compromised as a result of a brute-force attack have tell-tale signs. Here are the signals you should look out for:
- Hour of day and day of the week of failed sign-in and RDP connections;
- Timing of successful sign-in following failed attempts;
- Event ID 4625 login type (filtered to network and remote interactive);
- Event ID 4625 failure reason (filtered to %%2308, %%2312, %%2313);
- Cumulative count of distinct username that failed to sign in without success;
- The count (and cumulative count) of failed sign-ins;
- Count (and cumulative count) of RDP inbound external IP;
- Count of other machines having RDP inbound connections from one or more of the same IP.
via Microsoft Security Blog
How Can Heimdal® Help?
Heimdal’s Next-Generation Antivirus & MDM Anti-Brute-Force module for enterprises can protect against brute force attacks by generating blocking rules for vulnerable ports and isolating affected machines.
This is particularly useful for companies that acquire our NGAV solution or any service that includes this module – like our EDR or XDR software.
Heimdal’s Next-gen Endpoint Antivirus’s traditional firewall features like port and application management go hand in hand with unique features that ensure brute force and ransomware prevention and device isolation.
From the unified, intuitive Heimdal dashboard you can even choose to automatically block the RDP port on brute force detection. You also have the option to isolate an endpoint – in this case, all its external connections will be rerouted through the Heimdal systems.
Morten Kjaersgaard, Heimdal’s CEO
Final Thoughts
In summary, brute force attacks are cyberattacks designed to guess passwords and other credentials by trying different combinations, usually with the help of an automated script.
These attacks can be highly damaging since they often go unnoticed as the scripts work continuously in the background. Fortunately, there are various prevention strategies such as setting up two-factor authentication and implementing a complex password policy that could significantly reduce your risk of becoming a victim of this type of attack.
P.S. Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security