Contents:
Pursuant to Microsoft’s July press release regarding the default enforcement of Account Lockout policies for local administrators, Heimdal® has published the findings of its report on Brute-Force-type events in the context of H.O.M (i.e., Human Operated Malware). Per Microsoft’s announcement, all Windows builds, including the latest Windows 11 Operating System, will benefit from this change in the local administrative policies, thus increasing the machine’s overall protection during an active brute-force attempt.
Brute-Force Blocking Enabled by Default
In late July, David Weston of Microsoft announced on the company’s Twitter page that a new safeguard is to be adopted to counter brute-force attempts and subsequently cull existing attack surfaces. The new policy, which is enabled by default in Windows 11, is called Account Lockout and uses the 10-10-10 rule (i.e. both user and administrative accounts will go into lockdown for 10 minutes if 10 failed login attempts are detected within a 10-minute interval).
Furthermore, sysadmins curating older Windows builds will be able to manually enforce this new policy from the Security Settings section in the Local Group Policy Editor.
To enable this feature, follow this pathway:
Local Computer Policy\Computer Configuration\Windows Settings\Security Settings\Account Policies\Account Lockout Policies.
From the rightmost panel, you may set account lockdown duration, and threshold, allow or block administrative account lockdown, and reset the account lockout counter after a predetermined interval.
Heimdal® and the Rising Challenge of Human Operated Malware.
Heimdal® commends Microsoft’s initiative and is inclined to share our 4-year-long experience of addressing adversarial activity utilizing brute-force attacks. Introduced in late 2018, Heimdal®’s port-level brute-force attack blocking technology has achieved phenomenal results, proving itself to be a redoubtable (and functional) countermeasure against threat actors leveraging brute-force attacks for infrastructure infiltration purposes.
Based on analysed telemetry, we have determined that the 2020 – 2022 timeframe is of great significance, internal probing having suggested a brute-force attack recrudescence.
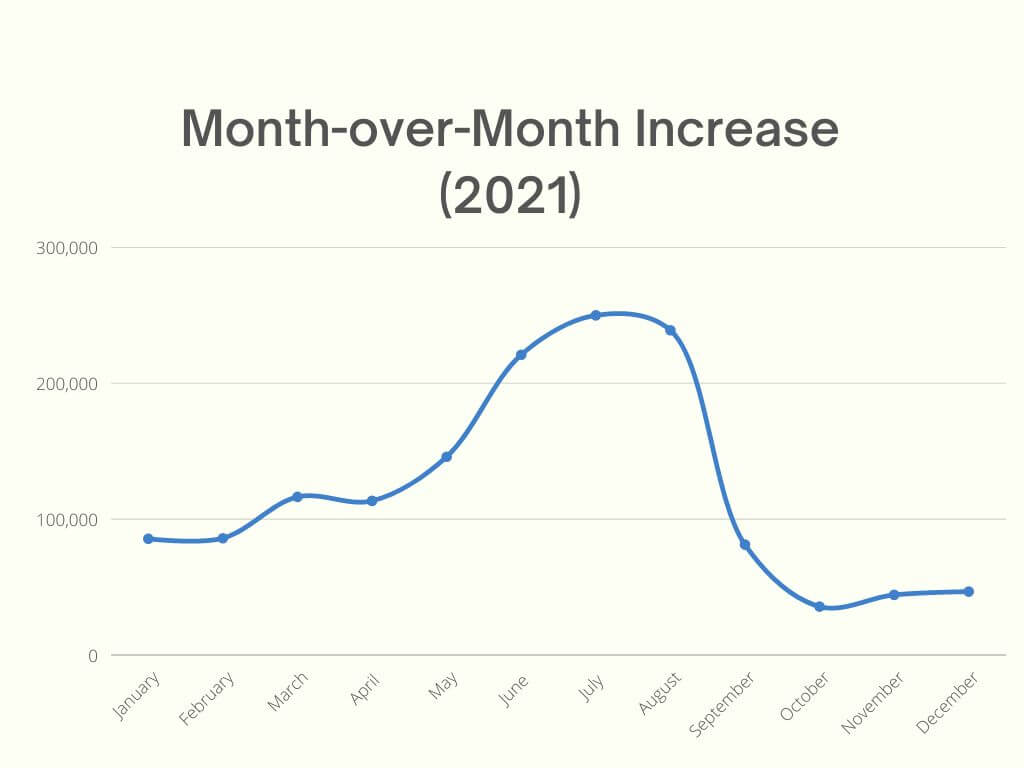
Throughout the referenced interval (i.e., I.O.R), Heimdal® has detected and blocked 3,269,213 brute-force attempts affecting over 10,000 endpoints. As far as distribution is concerned, based on our observations, most of the attacks were concentrated around 2021, an assumption corroborated by numerous cybersecurity-related publications and analysts that have, indeed, observed a significant increase in brute-force attacks, especially in Q1 2021.
The numbers reveal that between January 1st and December 31st, 1,466,101 brute-force events occurred, representing 55.15% of all attacks registered and addressed by Heimdal®’s brute-force protection module. Our in-depth investigation has also shed some light on the most used attack vectors.
Although arcane and with a low likelihood of success, threat actors still favor TCP 3389 (i.e. default RDP port). The list of most targeted ports includes FTP (ports 20 and 21), SSH (port 22), SMB (ports 139, 137, and 445), DNS (port 53), HTTP and HTTPS (ports 443, 80, 8080, and 8443), and Telnet (port 23).
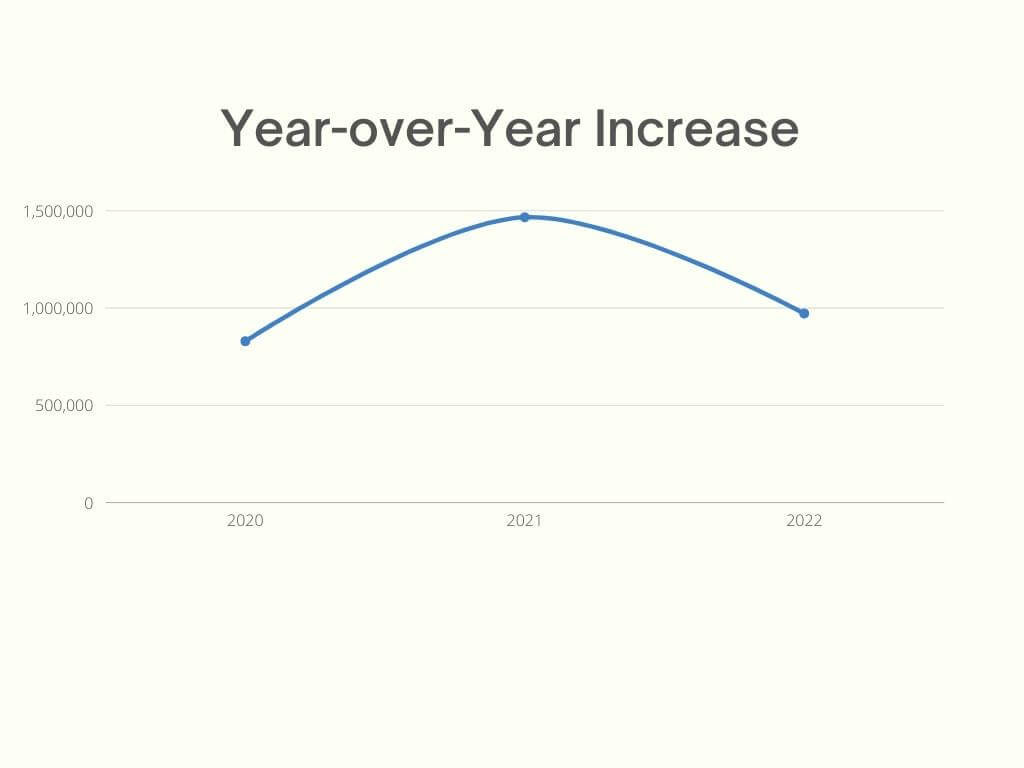
Heimdal® and other cybersecurity actors have closely observed the brute-force phenomenon and based on the available telemetry we can state that regardless of how many countermeasures are taken on the defender’s side, there’s no indication of a slowdown or volumetric decrease. Our statistics indicate a steady 76% YoY (i.e., Year-over-Year) increase. Graphical representations of these facts of these facts are available below.
YoY increase in Brute-Force Attacks (based on Heimdal® telemetry)
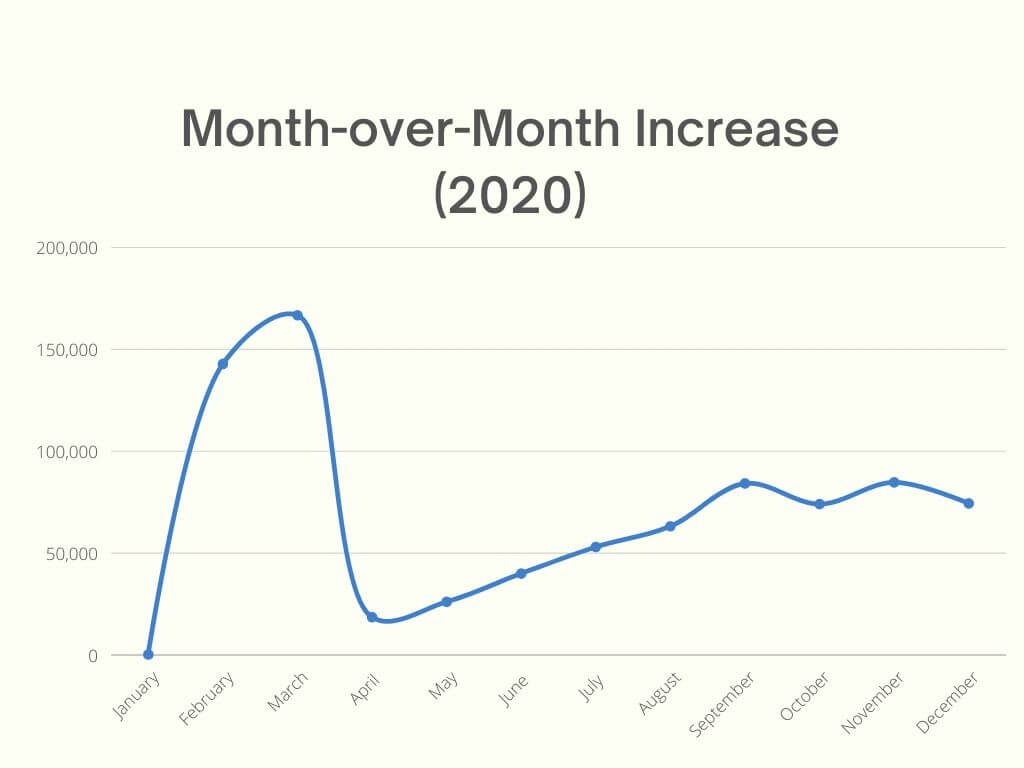
MoM increase 2020 (based on Heimdal® telemetry)
MoM increase 2021 (based on Heimdal® telemetry)
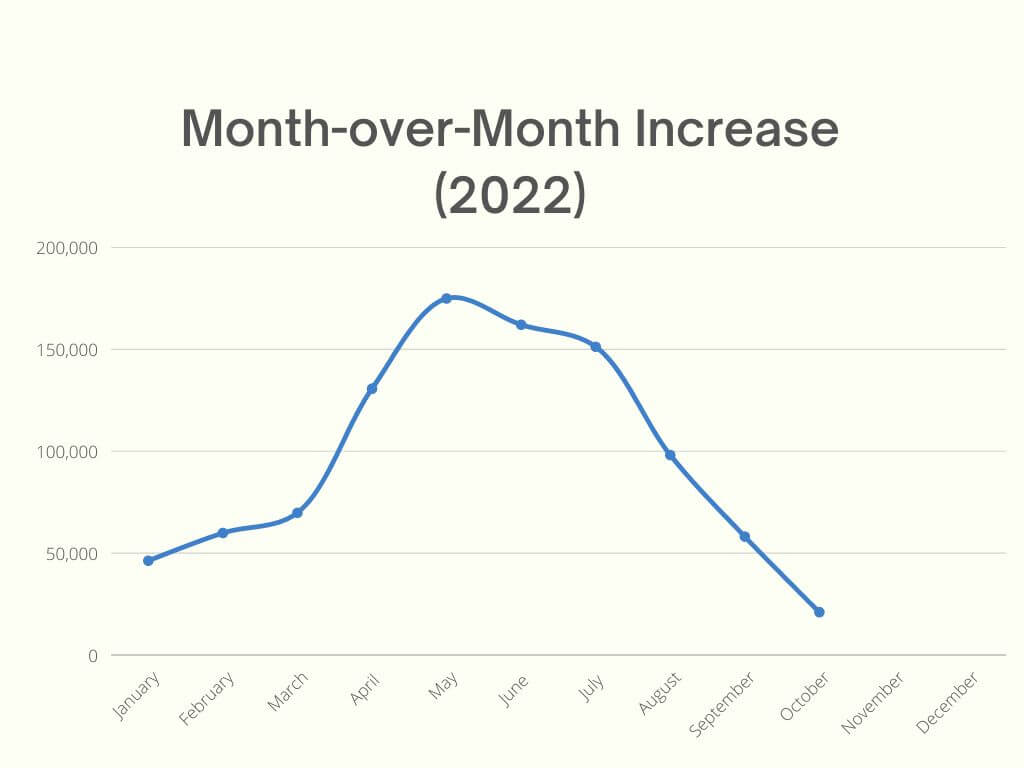
MoM increase 2022 Q1+Q2+Q3+early Q4 (based on Heimdal® telemetry)
Going Beyond Detection & Mitigation
As previously mentioned, our collected data highlights the fact that brute-force attacks continue to be the technique of choice during the early infiltration stage. At this point in time, the natural question arises – “what is the best defense against brute-force attacks?” In alignment with Microsoft’s latest decision to enforce lockdown policies for both user and administrative accounts, Heimdal® campaigns for stronger firewall ruling and using multi-modal approaches in order to block the event, create automatic rules, and isolate the affected machine(s) for further investigation. Lessons learned after nearly half of decade of tackling brute-force attacks:
- Brute-force attacks will never go out of fashion. In fact, in-field data suggests that brute forcing has become a golden standard in the malware industry. For instance, every package marketed under the RaaS banner has at least one brute-forcing utility.
- Brute-force attacks no longer prey on overtly vulnerable RDP ports. As mentioned, threat actors will attempt to attack any type of open or improperly secured port.
- Finally, brute-force attacks are commonly used to probe the victim’s defenses.
Heimdal® recommends that you enforce Microsoft’s lockdown feature for all your Windows-running machines as soon as possible. If most of your machines are running the latest Windows version (i.e., Win 11), this feature will be switched on by default. Secondly, we recommend that you review and, if necessary, modify your firewall setting for both inbound and outbound connections. Lastly, you should consider bolstering your defenses by deploying an EPP-type solution that has brute-force protection features. Heimdal®’s Next-Generation Antivirus & MDM Anti-Brute-Force module will ensure safety against this type of threat, by automatically generating blocking rules for ports under assault and isolating the affected machine.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security