Contents:
NSA recently released a new advisory, in which it states that the Russian GRU’s 85th Main Special Service Center (GTsSS), military unit 26165, has been using a Kubernetes cluster since 2019 in order to perform password spray attacks on US and foreign organizations that are including the US government and Department of Defense agencies.
GTsSS malicious cyber activity has previously been attributed by the private sector using the names Fancy Bear, APT28, Strontium, and a variety of other identifiers.
The 85th GTsSS directed a significant amount of this activity at organizations using Microsoft Office 365 cloud services; however, they also targeted other service providers and on-premises email servers using a variety of different protocols. These efforts are almost certainly still ongoing.
Kubernetes Brute Force Attacks Used to Compromise Networks
The Kubernetes brute force attacks have targeted cloud services, like Microsoft 365 with the purpose of compromising accounts that are then used in conjunction with known vulnerabilities and gain access to corporate and government networks.
It looks like the threat actors are using various exploits including the Microsoft Exchange CVE-2020-0688 and CVE-2020-17144 remote code execution vulnerabilities.
The NSA says that once the malicious actors have gained access, they will spread laterally through the network while deploying a reGeorg web shell used harvesting other credentials and stealing files.
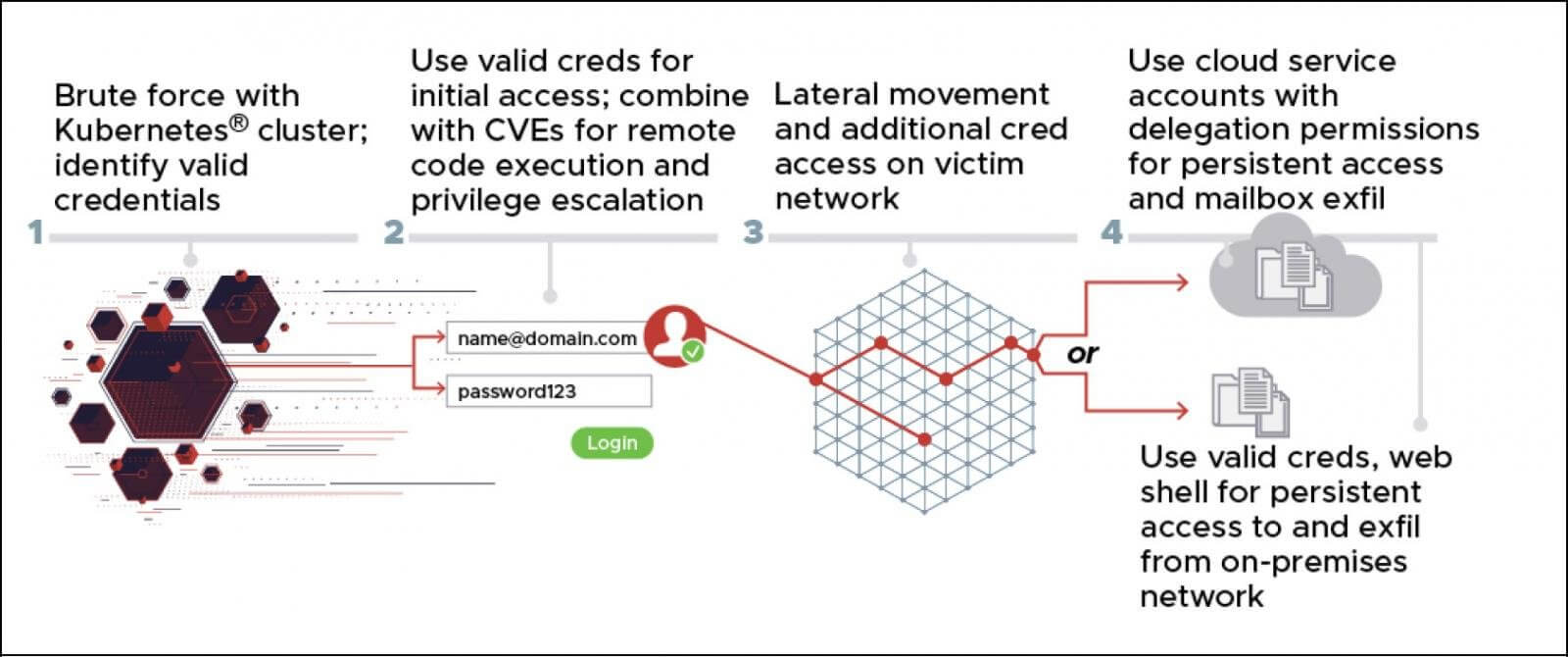
In order to obfuscate the origin of the attacks, the Kubernetes cluster is performing brute force attacks through TOR and VPN services, including CactusVPN, IPVanish, NordVPN, ProtonVPN, Surfshark, and WorldVPN.
According to the NSA between November 2020 and March 2021, the hackers have conducted brute force attacks without using an anonymization service, thus exposing the following IP addresses as being used by the Russian GTsSS’ Kubernetes cluster:
|
|
The attacks were targeted at the US and foreign entities like:
- Government and military organizations
- Political consultants and party organizations
- Defense contractors
- Energy companies
- Logistics companies
- Think tanks
- Higher education institutions
- Law firms
- Media companies
NSA declared for the news publication BleepingComputer in regards to the government agencies breached that:
The NSA does not publicly share details on victims of foreign malicious cyber activity.
How to Defend Yourself Against These Attacks?
NSA recommends for the organizations to expand their use of multi-factor authentication (MFA) in order to be able to restrict the use of stolen credentials and implement a Zero Trust security model.
This lengthy brute force campaign to collect and exfiltrate data, access credentials and more, is likely ongoing, on a global scale. Net defenders should use multi-factor authentication and the additional mitigations in the advisory to counter this activity.
The NSA also advises organizations to block inbound connections from anonymization services that are not typically used in an organization, such as commercial VPN providers and TOR.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










