Contents:
On Wednesday, JBS Foods, the world’s largest meatpacking organization, was forced to shut down production at several sites all over the world following a cyberattack that affected its production facilities, including those from the United States, Australia, and Canada.
Following the incident, the FBI released a statement, attributing the attack to REvil Ransomware operation.
As the lead federal investigative agency fighting cyber threats, combating cybercrime is one of the FBI’s highest priorities. We have attributed the JBS attack to REvil and Sodinokibi and are working diligently to bring the threat actors to justice. We continue to focus our efforts on imposing risk and consequences and holding the responsible cyber actors accountable. Our private sector partnerships are essential to responding quickly when a cyber intrusion occurs and providing support to victims affected by our cyber adversaries. A cyberattack on one is an attack on us all. We encourage any entity that is the victim of a cyberattack to immediately notify the FBI through one of our 56 field offices.
Source: FBI Statement on JBS Cyberattack
JBS has not revealed if it received any ransom demand. However, the company reported that its restoration efforts were continuing to proceed quickly and that it expected to resume full operations on Thursday.
JBS USA CEO Andre Nogueira issued a statement saying that JBS USA and Pilgrim’s continue to make significant progress in restoring their IT systems and returning to business as usual.
He added that the company is not aware of any evidence at this time that any customer, supplier, or employee data has been compromised.
“Given the progress our teams have made to address this situation, we anticipate operating at close to full capacity across our global operations tomorrow,” Nogueira added.
Discovered in April 2019, Revil, also known as Sodinoki, is a highly evasive and upgraded ransomware, which uses a special social engineering move – the ones who spread it threaten to double the ransom if not paid within a certain number of days. This aspect makes Sodinoki ransomware dangerous for companies of all sizes.
The REvil Ransomware gang has not yet taken credit for the attack. They would have normally issued a post on the “happy blog” data-leak site, reachable only via the anonymizing Tor browser, naming and pressuring the victim into paying.
Cybersecurity experts say that before victims get listed on data-leak sites, REvil will typically attempt to engage with victims and begin negotiations. Usually, the threat actor will demand a ransom for a decryption tool.
According to ransomware incident response firm Coveware, REvil was the most-seen type of malware encountered by ransomware victims in the first quarter of the year.
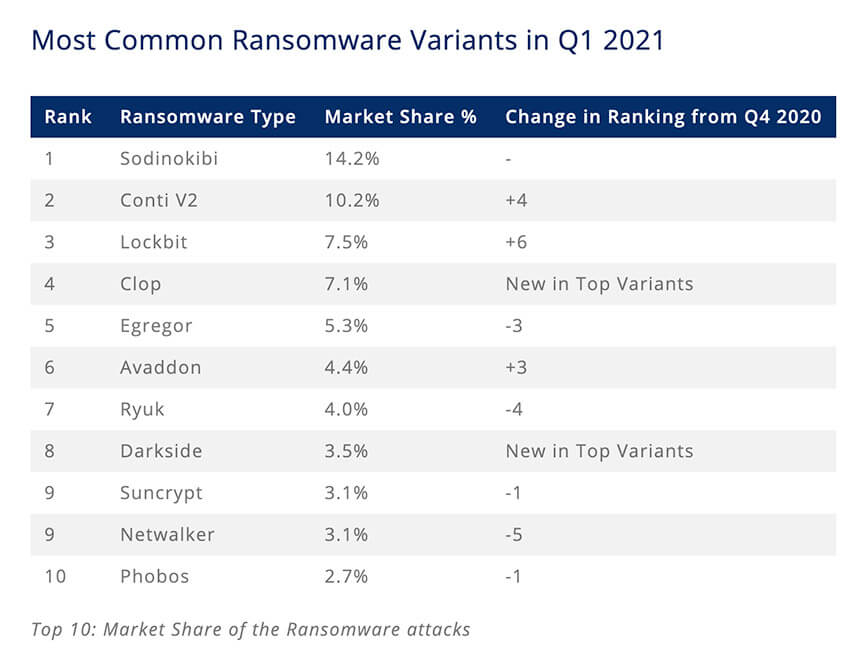
Image Source: Coveware
REvil ransomware is responsible for several high-profile infections in recent months, including Acer, Apple supplier Quanta, Asteelflash, Laboratoires Pierre Fabre, and UnitingCare Queensland.
There seem to be no boundaries for the REvil Ransomware gang. In early March, a security researcher discovered that REvil Ransomware launched a service for contact to news media, companies for the best pressure at no cost, and DDoS (L3, L7) as a paid service.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










