Contents:
Cybersecurity researchers identified several fake antivirus websites used by cybercriminals to distribute malware. These websites closely mimic legitimate antivirus sites but deliver malicious software instead of protection.
In mid-April, Trellix’s Advanced Research Center discovered that these fake websites host malicious files, including .apk, .exe, and installer files created with Inno Setup.
The malware includes espionage and infostealing functions, targeting users seeking to protect their devices.
Which fake websites have been identified?
The fake websites mimic well-known antivirus brands, such as:
- avast-securedownload[.]com
- bitdefender-app[.]com
- and malwarebytes[.]pro.
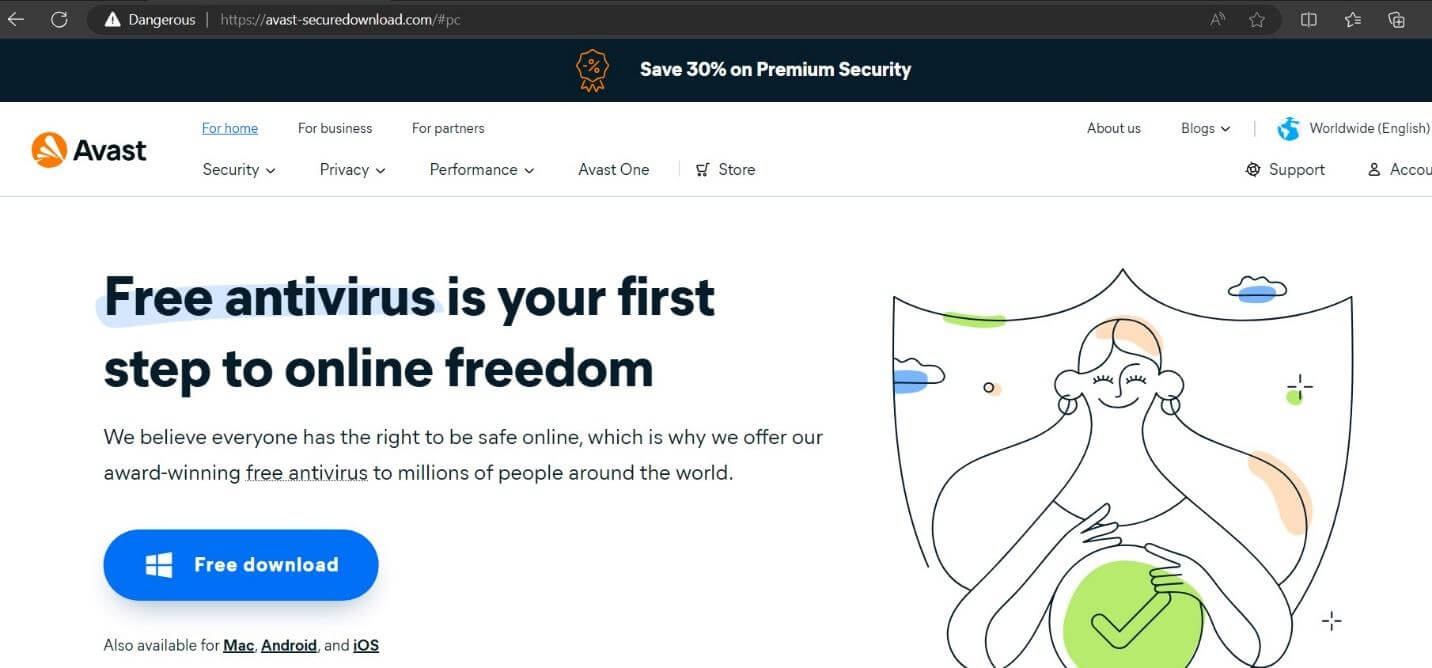
‘Avast’ fraudulent website (source)
These sites distribute files like:
- Avast.apk
- setup-win-x86-x64.exe.zip
- and MBSetup.rar
containing malware instead of legitimate software.
According to Trellix’s analysis, the malicious files have various harmful capabilities.
- For example, the fake Avast APK can install and delete packages, read call logs, SMS, and saved data, and access network settings.
- The fake Bitdefender file contains the Lumma stealer, which exfiltrates information, and the fake Malwarebytes file contains the StealC malware, which steals data and access tokens.
- The fake Trellix software collects PC information and sends it to a command-and-control server.
To learn more, read the full report here.
Safety recommendations
To protect against these dangerous websites you can follow good cyber hygiene practices such as:
- Always double-check links before clicking on them.
- Make sure the website you are visiting is legitimate.
- Put powerful cybersecurity technologies to use to make sure you are safe from these kinds of malicious attempts.
- Never use pirated software, as it often leads to downloading fake or malicious binaries.
- Make sure your endpoint security provider approves the program you are downloading.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










