Contents:
Researchers disclosed a new Intel CPU vulnerability that allows escalation of privileges, access to sensitive data, and denial of service via local access.
CVE-2023-23583 has an 8.8 CVSS score and impacts various Intel desktop, mobile, and server CPUs. According to Intel, until now there is no evidence of active exploitation of this flaw.
More About the Intel CPU Vulnerability
CVE-2023-23583, also known as Reptar, was first discovered by an Intel partner during the testing phase in Sapphire Rapids product development. Initially, researchers considered it a functionality bug and fixed it in Sapphire Rapids, Alder Lake, and Raptor Lake.
After that, the analysis of the bug revealed that hackers could use it for temporary denial of service (TDoS). Further on, researchers discovered a vector that permitted escalation of privilege. That`s when the vulnerability`s CVSS score rose from 3.0 to 8.8 (high).
In parallel, a team of researchers within Google also independently discovered the Intel CPU vulnerability and dubbed it Reptar. Tavis Ormandy, researcher at Google, said:
We observed some very strange behavior while testing. For example, branches to unexpected locations, unconditional branches being ignored, and the processor no longer accurately recording the instruction pointer in xsave or call instructions
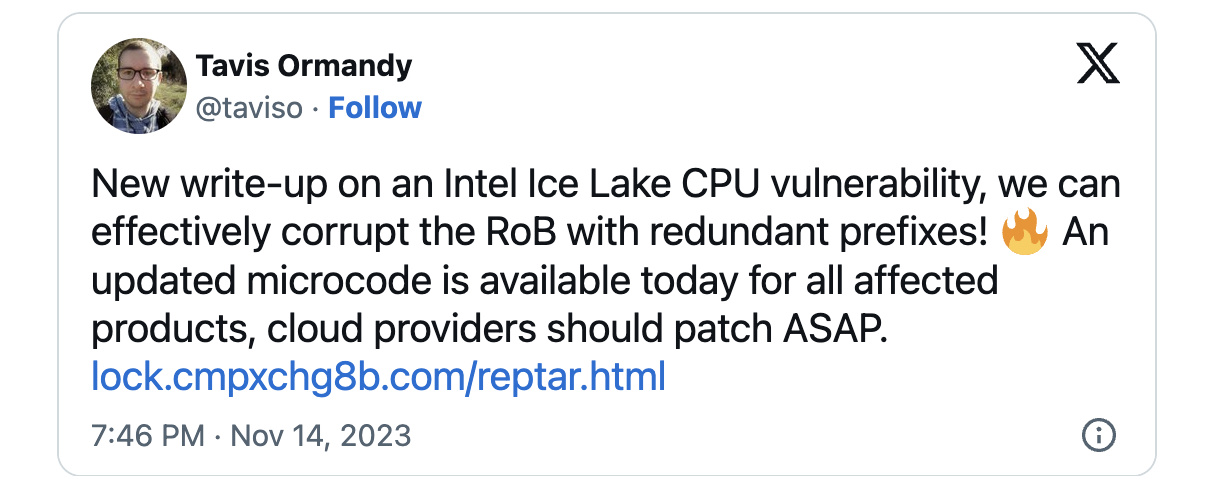
Source: BleepingComputer.com
Intel already released updates to address the vulnerability.
CVE-2023-23583 Impact and Mitigation Measures
Intel published here the list of all CPUs affected by the CVE-2023-23583 vulnerability.
The tech giant described the glitch as a sequence of processor instructions that results in unpredictive behavior for some Intel(R) Processors. As a result, unauthenticated users could be able to:
- gain escalation of privilege,
- compromise data integrity
- use local access to generate denial of service.
As a security measure, Intel urges users to apply patches and update processors to the microcode version.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security