Contents:
Over 16,400 global organizations are at risk due to a critical security flaw that could lead to the remote compromise of systems, an investigation by Heimdal has found.
Tracked as CVE-2024-6387 and known as RegreSSHion, this vulnerability carries a CVSS score of 8.1, raising alarms within the cybersecurity community for its potential to enable remote code execution (RCE) on Linux systems.
Malware analyst Andrei-Mihai Minca conducted a Shodan analysis, revealing an extensive list of vulnerable organizations.
To prevent attackers from exploiting these vulnerabilities, we are keeping the identities hidden. However, the list includes:
- Top academic institutions in the United States, United Kingdom, and Zurich.
- Major energy companies in France, Canada, and Zimbabwe.
- Reputable education and government bodies in the United States, Italy, and Taiwan.
The flaw, discovered by Qualys in June, has widespread implications, affecting a significant number of OpenSSH servers worldwide.
If left unpatched, attackers could gain full root access to systems, including critical servers, network devices, and IoT systems.
A patch is available, and it is crucial for businesses to prioritize updating affected systems to mitigate the risk of attackers exploiting this vulnerability.
Morten Kjaersgaard, founder of Heimdal®, emphasized the severity and complexity of the issue:
It’s important to note that while the vulnerability is severe, actual exploitation is quite complex and time-consuming, requiring thousands of attempts and specific system configurations.
This makes widespread, indiscriminate exploitation less likely. However, targeted attacks by skilled threat actors remain a significant concern for organizations running vulnerable versions of OpenSSH.
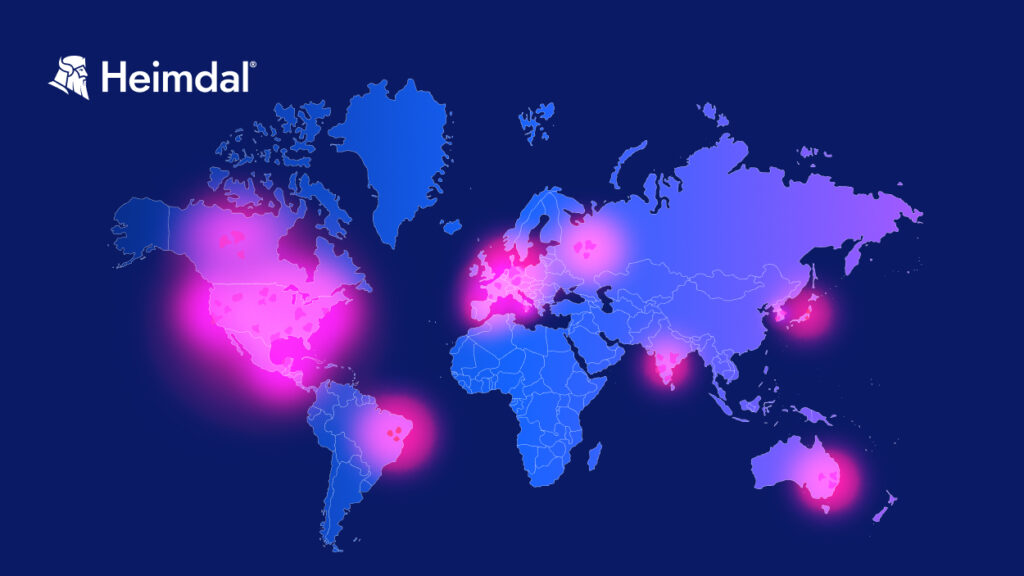
The vulnerability affects businesses across the world, with significant numbers reported in the United States (6,592), Germany (3,784), and France (1,164), among others.
Heimdal is reaching out to larger businesses at the highest risk and sharing this story to spread the message – patch this vulnerability now.
The Deeper Dive
What is the CVE-2024-6387 (RegreSSHion) vulnerability?
CVE-2024-6387 abuses the regression function in OpenSSH systems. If the flaw is exploited correctly, it could allow the threat actor to execute arbitrary code on the victim’s machine or cause a Denial-of-Service.
The newly encountered regreSSHion vulnerability stems from a 2020 code design flaw.
The regression function introduced in OpenSSH version 8.5p1, would remove a pre-processor directive from a function that is directly called by the signal handler SIGALRM.
This, in turn, would cause the system to call the SSHD’s SIGALRM handle asynchronously.
The CVE-2024-6387 vulnerability was found to impact Linux servers running OpenSSH versions 8.5 through 9.7.
As a result, this vulnerability allows attackers to perform multiple actions on object.
This includes:
- Generating unauthorized users in some Linux distributions (i.e., systems running OpenBSD were found to be unaffected by CVE-2024-6387) and posing a significant threat to companies globally. This could exacerbate already deep-seated instances of Shadow IT.
- Cause service disruptions (Denial-of-Service).
- Remote Code Execution (RCE) on the compromised machine.
RegreSSHion’s worldwide impact could be massive, considering the high number of businesses and institutions that rely on Linux-based servers for business operations.
ZDnet pointed out that 96.3% of the top million servers are using Linux.
This includes top market players such as Microsoft, Google, Meta, and even Wikipedia.
The Analysis, Implications, and Protective Measures
Heimdal analyzed all available telemetry provided by Shodan, a search engine for internet-connected devices, and concluded that RegreSSHion impacts over 16,400 businesses, including notable academic institutions, utility companies, and government organizations.
We’re keeping the identities hidden to prevent attackers exploiting this vulnerability.
Here’s a rundown of the countries impacted:
- United States: 6,592.
- Germany: 3,784.
- France: 1,164.
- United Kingdom: 1,010.
- Canada: 946.
- Netherlands: 510.
- Russia: 497.
- Australia: 467.
- Japan: 352.
- China: 284.
- India: 212.
- Brazil: 183.
- Italy: 154.
- South Korea: 137.
- Mexico: 124.
The Impact
Systems running vulnerable to CVE-2024-6387 are impacted on several levels.
Remote Code Execution Impact & Implications
-
System Compromise and Unauthorized Access
Attackers can gain control over the server, enabling them to perform any actions that the compromised account or application is capable of.
This could lead to unauthorized access to sensitive data, unauthorized use of system resources, and potential control over other connected systems.
-
Data Theft & Leakage
RCE can be used to exfiltrate sensitive data, including personal information, intellectual property, or confidential business data.
This could lead to data breaches, legal consequences, and loss of trust from clients and partners.
-
Service Disruption and Denial of Service:
Arbitrary code execution can disrupt normal server ops, causing service outages or degradation of service quality.
Attackers might also deploy denial-of-service (DoS) attacks, leading to downtime and affecting the availability of services.
-
Malware Deployment and Propagation
RCE vulnerabilities can be exploited to deploy malware such as ransomware, spyware, crypto miners, or botnets.
This can result in financial loss or further security breaches.
Denial-of-Service Impact & Implications
-
Service Outages and Downtime
A DoS attack can bombard the server with excessive traffic or resource consumption, causing services to become unavailable.
This can lead to prolonged downtime, preventing users from accessing websites, applications, or services hosted on the affected server.
-
Financial Loss
The downtime resulting from a DoS attack can lead to direct financial losses due to missed transactions, and loss of business opportunities.
Additionally, costs may be incurred to mitigate the attack, restore services, and implement stronger defenses.
-
Reputation Damage
Frequent or prolonged service outages can damage an organization’s reputation.
Customers and users may lose trust in the reliability of the services, leading to a potential loss of clientele and negative publicity.
This can have long-term effects on the organization’s brand and market position.
-
Resource Drain & Increased Operational Costs
Responding to and mitigating DoS attacks can consume significant IT resources and staff time.
The increased load on network and server infrastructure can also lead to higher operational costs.
Protection measures
A patch for this vulnerability is available in OpenSSH version 9.8p1.
System administrators are encouraged to update affected systems as soon as possible to avert negative impact on business operations.
Furthermore, regular system audits and stringent access controls are recommended to enhance security.
An alternative workaround is available.
If patching is not viable or threatens data integrity, the system administrator can manually disable the async signal unsafe code.
For additional information on how to perform this operation, please consult PenTestTools’ article on the regreSSHion vulnerability.
Conclusion
CVE-2024-6387 (regreSSHion) affects over 16,000 businesses using OpenSSH versions 8.5 through 9.7, allowing remote code execution and denial-of-service attacks.
Organizations should update to OpenSSH 9.8p1 immediately to mitigate risks. If updating isn’t possible, disable the async signal unsafe code.
Regular audits and stringent access controls are also recommended.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







