Contents:
ALPHV ransomware operators published stolen data on a replica of a victim’s site as part of their extortion tactic. Also known as BlackCat ransomware, ALPHV is known for testing new ways to force their victims into paying.
Even though these tactics have not yet been successful, ransomware targets are faced with an ever-growing threat landscape as a result.
Using a Clone to Leak Data
The cybercriminals announced, on December 26, that they had compromised a financial services company on a data leak site. As the victim did not meet the threat actor’s demands, BlackCat published all the stolen files as a penalty, which is the usual outcome in these instances.
However, what differed from the common procedure was that the hackers also published the data on a site that had the same domain name and looked just like the original. The only visible changes were the headings, which the hackers used to organize the leaked data.
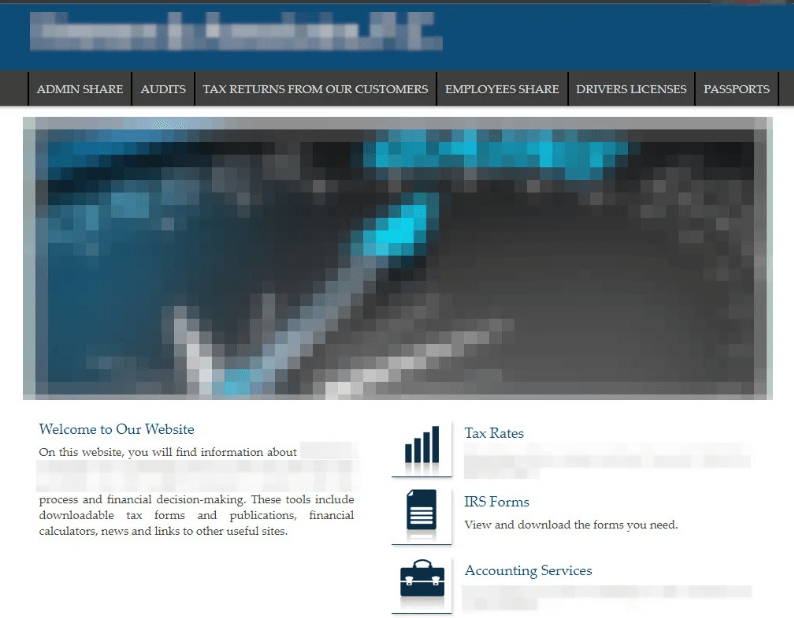
In order to ensure wide access, the cloned site is on the clear web, displaying a total 3.5GB of various documents, such as memos to staff, payment forms, employee information, assets and expenses, financial data for partners, and passport scans. Furthermore, ALPHV also shared the stolen data on a file-sharing service and distributed the link on its leak site.
The Rise of a New Trend
According to BleepingComputer, Emisoft threat analyst Brett Callow said that sharing the data on a typosquatted domain would be a much bigger concern, as this tactic could represent the start of a new trend that may be adopted by other ransomware gangs.
To extort their victims, ransomware groups have always sought new methods. With the threat of publishing the name of the breached company, stealing data and threatening to publish it if the ransom is not paid, and the DDoS threat, this tactic could turn into a new trend that other cybercrime gangs may adopt, especially since the costs to do it are considerably lower.
However, it is unclear for now how successful this strategy actually is, but it exposes the breach to a larger audience, putting the victim into a more delicate position as its data is readily available without any restriction.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









