Contents:
A sophisticated new malware campaign is targeting the Python Package Index and npm for both Python and JavaScript with typosquatted modules that deploy a ransomware strain. It’s yet another way that cybercriminals are infiltrating the software supply chains.
The typosquatted Python packages impersonate the popular requests library: dequests, fequests, gequests, rdquests, reauests, reduests, reeuests, reqhests, reqkests, requesfs, requesta, requeste, requestw, requfsts, resuests, rewuests, rfquests, rrquests, rwquests, telnservrr, and tequests.
A blog post belonging to Phylum explains that the malicious packages download a Golang-based ransomware binary from a remote server depending on the victim’s operating system and CPU architecture.
When successful, this attack kicks off by changing the victim’s desktop background to an actor-controlled image that claims to be from the Central Intelligence Agency (CIA), while also encrypting files in an attempt to extort $100 in cryptocurrency.
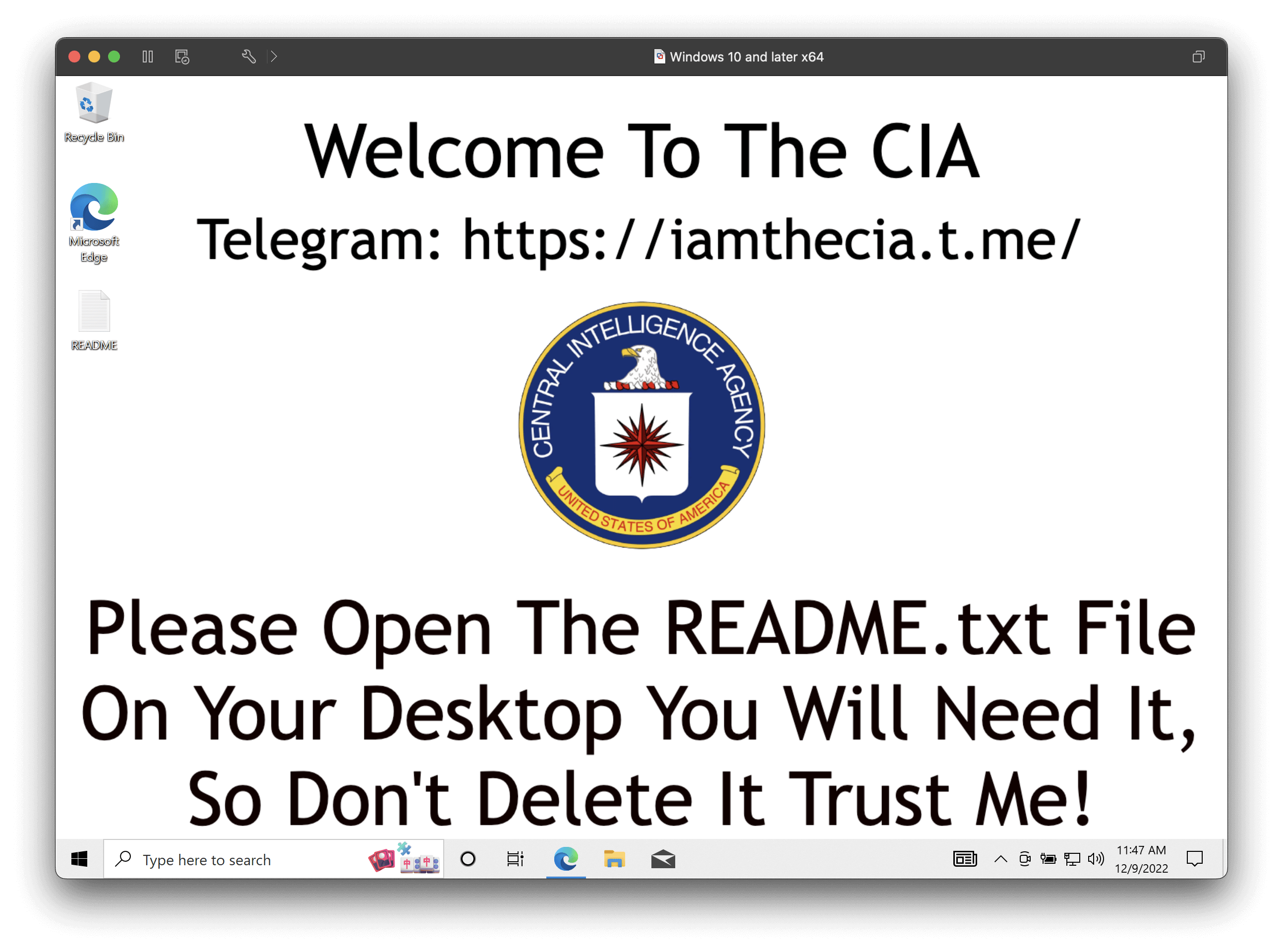
However, the attack is not limited to PyPI, as five different modules in npm (discordallintsbot, discordselfbot16, discord-all-intents-bot, discors.jd, and telnservrr) have been published by the threat actor.
PyPI Packages Used to Push Malware
Earlier this month, ReversingLabs researchers discovered 10 PyPI packages pushing modified versions of W4SP Stealer malware, as part of an ongoing supply chain attack that is believed to have started around September 25, 2022.
Additionally, around the same time, Israel-based software supply chain security firm Legit Security showcased a new attack technique against a Rust repository that abuses GitHub Actions to poison legitimate artifacts.
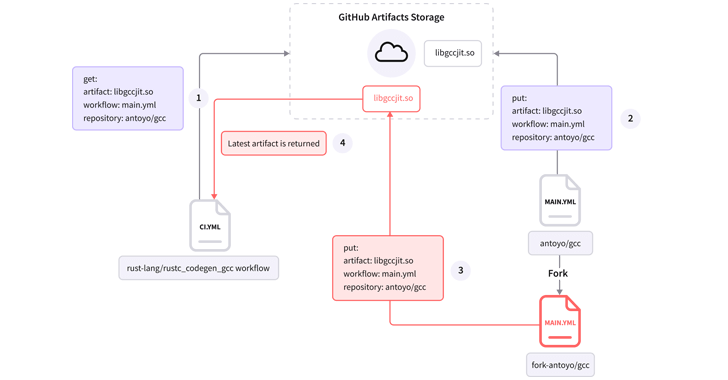
Build artifacts are various files created during the build process. Replacing the original modules with trojanized versions can give an actor a chance to steal sensitive information or deliver additional payloads to all downstream users.
rust-lang is the official Rust project in GitHub, and the vulnerability we found is in the “rust-lang/rustc_codegen_gcc” repository and could allow any user to execute code in a privileged pipeline. This gave any user the ability to write code that extracts repository secrets like cloud credentials, modifies project settings and even tampers with the source code using GitHub API, since the privileged pipeline has access to all that.
The vulnerability was found in a workflow called “ci.yml” which is responsible for building and testing the repository’s code.
By taking advantage of this weakness, the GitHub web service could be tricked into executing an artifact that is laced with malicious software. This would allow attackers to tamper with branches, pull requests, issues, and releases. However, this issue has been addressed on September 26, 2022.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









