Contents:
Hackers use phishing techniques to deploy NetSupport RAT through Microsoft Office documents.
NetSupport RAT is an offshoot of NetSupport Manager, a remote support solution with over 21 million users worldwide. The remote access trojan (RAT) mimics the legitimate remote-control software to:
- evade detection
- monitor victim’s behavior
- capture keystrokes
- exfiltrate data
- take over system resources
- move laterally within the network
How they use phishing to deploy NetSupport RAT
Hackers use phishing techniques to gain initial access to the system. Researchers observed that in this case, they used an unusual way to deploy NetSupport RAT.
The Object Linking and Embedding (OLE) method takes advantage of legitimate Microsoft Office document templates to go unnoticed while installing malware. An OLE package is a legitimate feature in Microsoft Windows. It permits embedding and linking to documents. It also enables hackers to mix documents with elements from different programs.
What is unusual in the OLE template manipulation TTP is that it hides the payload outside the document. The payload only executes upon user interaction.
Source – Windowsreport.com
Here’s the process:
- The attackers use Brevo, an email marketing platform, to deliver their phishing messages in a legitimate looking way.
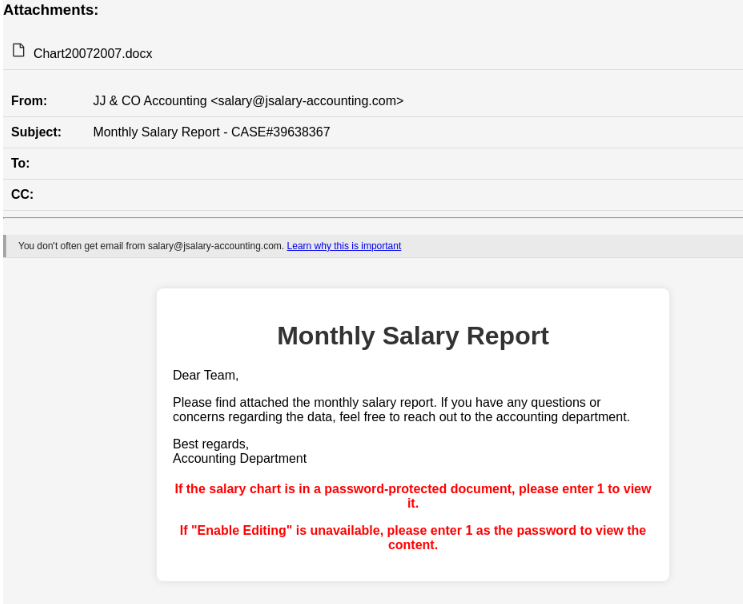
- The victim gets a salary-themed phishing email. The email appears to be from accounting and has a Microsoft Word document attached which is supposedly a “monthly salary report”.
- Once the victim opens the document, they are told to enter a password included in the phishing email body. To view the salary report, they should press enable editing, and double-click a printer icon embedded in the doc. The printer image is an OLE package.
- Further on, a ZIP archive file opens. The archive only includes a Windows shortcut file which is in fact a PowerShell dropper that retrieves and executes a NetSupport RAT binary from a remote server.
Phishing Attacks Prevention Measures
To prevent falling victim to phishing attacks, I recommend applying three prevention measures:
- Use an advanced protection tool against spam and phishing to avoid malicious emails getting into your team’s inboxes.
- Educate employees to identify phishing emails
- Use DNS filtering to block malicious inbound and outbound communication. In case one of your colleagues clicks a malicious link, the tool will cut the connection.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







