Contents:
New versions of Prilex point-of-sale (POS) malware have been spotted in the wild. Their new capabilities include blocking Near Field Communication (NFC) credit card transactions. This way clients are obliged to use the machine to pay, allowing the malicious code to steal credit card details.
The NFC chips found in credit cards and mobile devices allow secure, contactless payments with credit cards, smartphones, or even smartwatches. But this method of payment makes it hard for POS malware to steal information, this is why cybercriminals found a new way to do it.
The New Prilex Versions
Kaspersky researchers found three new variants of the Prilex malware, the first one being spotted in November 2022: 06.03.8070, 06.03.8072, and 06.03.8080.
Furthermore, in September 2022, Kaspersky reported that Prilex added EMV cryptogram generation to evade transaction fraud detection and to perform “GHOST transactions” even when the card is protected with CHIP and PIN technology.
All these new variants block contactless transactions, making the POS display “Contactless error, insert your card”. The victim is forced to insert the card to finish the payment, and this is the moment when the data are stolen via the infected machine.
NFC transactions use a unique ID per transaction, making the exfiltrated data useless for cybercriminals, so they block those transactions using a rule-based file from the malware. After stealing the data, the hackers use cryptogram manipulation and “GHOST transaction” attacks.
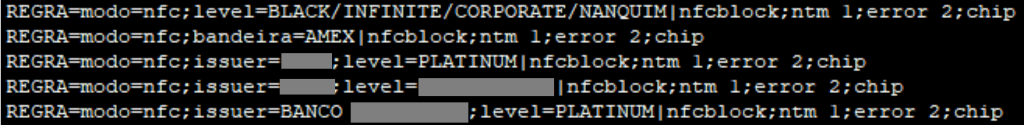
Prilex new variations have also the capability to filter undesired cards and just collect data from particular providers and tiers.
These [filtering] rules can block NFC and capture card data only if the card is a Black/Infinite, Corporate or another tier with a high transaction limit, which is much more attractive than standard credit cards with a low balance/limit.
How to Stay Safe
Customers have only a few measures available to protect themselves from Prilex and other POS malware because it is very hard to tell if a point-of-sale is infected or not.
Here are a few steps you can take:
- Try not to use POS machines that are visibly tampered with.
- Do not use public WiFi to access your bank account.
- Use a VPN when you are using your credit card information.
- Always confirm transaction information before and after completion.
- Closely monitor your bank statement for any suspicious transactions.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









