Contents:
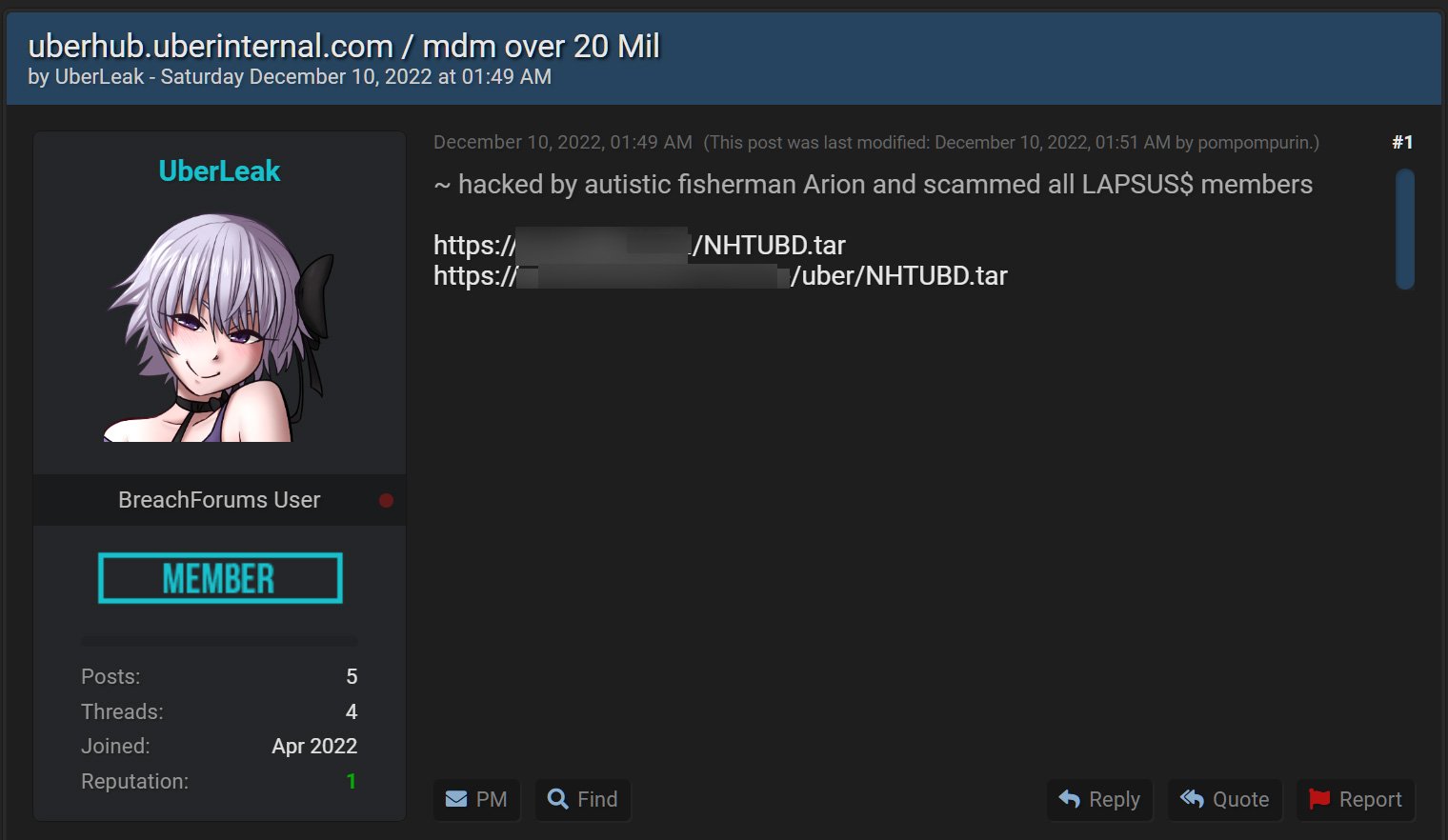
Uber suffered a new data breach on December 10th after the ”UberLeaks” threat actor spilled stolen data on a notorious hacking forum.
According to Uber, the data was stolen in a breach on Teqtivity, their collaborator on asset management and tracking services. This time it seems that Uber`s customers can be at ease, as none of their information was spilled, only internal Uber corporate data.
What’s at Risk after the Data Spillage?
Cyber researchers said the leaked data only included corporate information such as source code, IT asset management reports, data destruction reports, Windows domain login names, and email addresses.
Uber claims that the source code leaked Saturday was created by Teqtivity for managing their services. After the threat actor obtained access to one of Teqtivity`s AWS backup servers, where customers` data were stored, he got a series of information about client companies, such as Uber.
They are now in possession of intelligence about their devices – serial numbers, models, technical specs, etc. and sensitive user information: complete name, work email, and location. 77,000 Uber employees` had their email addresses exposed in this data leakage.
Cyber researchers warn that this could lead to targeted phishing attacks on Uber employees. Threat actors now have all the information they need to impersonate Uber IT support, for example.
Is This Attack Related to the Previous One in September?
Earlier this year, on September 15th, Uber announced they were victims of a cyberattack. That time, threat actors got access to the company’s Slack server, Amazon Web Services console, VMware ESXi virtual machines, and Google Workspace email admin dashboard.
According to Uber, no connection was found yet between the recent data leakage, that came from Teqtivity, and the previous attack, which was indeed performed on Uber`s computer system.
Uber has also reiterated that the Lapsus$ group was not related to this breach, even though the forum posts reference one of the threat actors associated with the group. While the forum posts state that they breached ‘uberinternal.com,’ Uber has said that they have not seen any malicious access to their systems.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









