Contents:
Researchers discovered a new kind of side-channel attack that affects several versions of Intel CPUs and enables data exfiltration. Attackers could leak the data through the EFLAGS register.
The discovery was made by researchers at Tsinghua University, the University of Maryland, and a computer lab run by the Chinese Ministry of Education.
How Is the New Site-Channel Attack Different?
Unlike other side-channel attacks, the new one does not rely on the cache system. Instead, it exploits a flaw in transient execution that enables the user to extract sensitive data from user memory space through timing analysis.
The attack works as a side channel to Meltdown, a critical security flaw discovered in 2018, impacting many x86-based microprocessors.
Meltdown exploits a performance optimization feature called “speculative execution” to enable attackers to bypass memory isolation mechanisms to access secrets stored in kernel memory like passwords, encryption keys, and other private data.
Although Meltdown was mitigated through software patches, microcode updates, and hardware redesigns, no 100% secure solution was found yet. Researchers warn that the latest attack method might also impact fully patched systems.
How Does It Work
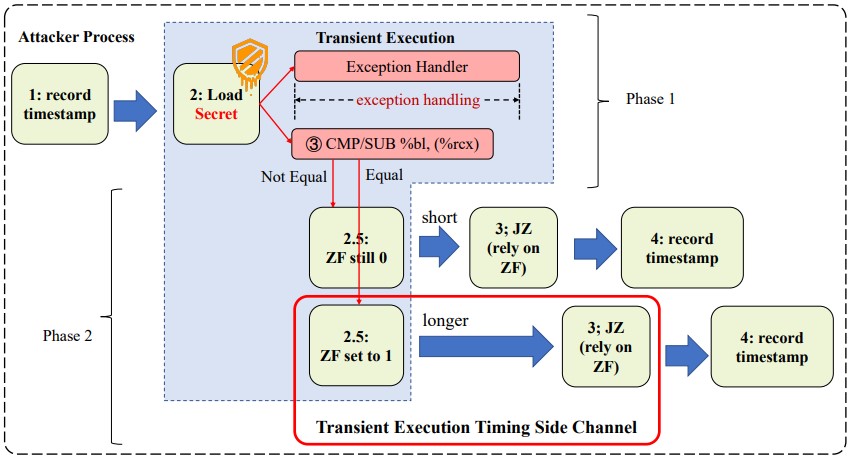
The new method was revealed in a technical paper and exposes a flaw in the change of the EFLAGS register in transient execution. It affects the timing of JCC (jump on condition code) instructions.
The attack works in two steps:
- it triggers transient execution and encodes sensitive data through the EFLAGS register.
- it measures the execution time of the KCC instruction to decode the data.
Researchers conducted the test on Ubuntu 22.04 jammy with Linux kernel version 5.15.0. The results showed that
the attack achieved 100% data retrieval (leak) for the Intel i7-6700 and Intel i7-7700 and had some success against the newer Intel i9-10980XE CPU.
In the end, researchers pointed out that this timing attack isn’t as trustworthy as cache-state side-channel techniques. It would take thousands of repetitions of the attack to improve performance on modern devices.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security