Contents:
A highly efficient phishing kit spreads the most among users from the United States and Canada. The scam targets online shoppers looking for “holiday specials” by impersonating popular brands.
The phishing campaign was first discovered in September 2022 and its kit uses social engineering, and sophisticated evasion detection techniques.
The novelty of this malicious campaign is the use of the URI fragmentation technique to keep non-victims away.
Details about the Phishing Campaign
An intriguing feature on the phishing kit is the implementation of a token-based system that allows each victim to be redirected to a different URL, Akamai security researchers are saying.
The phishing email tricks users into believing that they have the opportunity to win a gift from a well-known brand. The link contained by the phishing message leads to a malicious site through a series of redirections and using URL shorteners so it will not raise any suspicions.
To bypass security software, the hackers abuse legitimate cloud services like Google, AWS, and Azure.
The sites impersonate brands like sporting goods firm Dick’s, high-end luggage maker Tumi, Delta Airlines, Sam’s Club, and Costco, including even fake user testimonials to seem more real.
The kit is geographically targeted, to the point of blocking access outside of the intended target geography. This campaign is targeting North America, which has made up 89% of the victims.
Every victim landing on the fake site is welcomed by a timer that creates the feeling of urgency for completing a brief survey to win the promised gift. The last step is for the naive user to enter his card details to cover the shipping costs of the prize, allowing the threat actors to steal them.
URI Fragmentation Technique
This phishing campaign raises interest also due to a new technique among threat actors: URI fragmentation is used not as an HTML anchor, but as an evasive move.
An identifier for URL fragments is the hash mark (#), also known as an HTML anchor. This points to a certain spot on a webpage, and the value that is after the hash mark is not viewed as HTTP, not being sent to the server, but still accessible by JavaScript code present on the user’s browser.
Threat actors are now using this to evade security products.
In the context of a phishing scam, the value placed after the HTML anchor might be ignored or overlooked when scanned by security products that are verifying whether it is malicious or not. This value will also be missed if viewed by a traffic inspection tool.
Victims received a link in the phishing email that contains an HTML anchor followed by a token used by JavaScript to reconstruct the URI link to which that victim will be redirected.
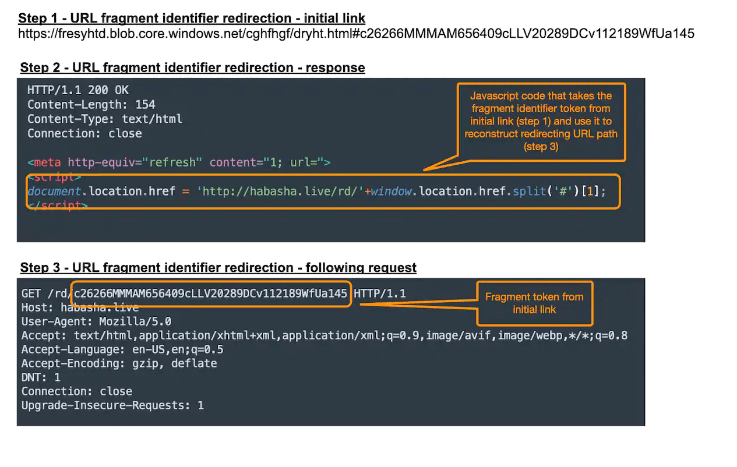
Access to the fake sites is restricted for whoever does not use that token or is not redirected by JavaScript, keeping away random users, or any unwanted traffic. The browser must be able to assemble the redirect URI to reach the malicious landing page.
Any access to a phishing scam without obtaining and using that token will be restricted from accessing the phishing landing page, meaning that visitors without the initial link will be filtered out. On top of that, browser-based access that is not running JavaScript as part of rendering of redirecting pages will also fail.
Such measures are intended to circumvent security barriers such as crawlers that scan suspicious links but do not use headless browser capabilities.
Tokens can be also used to make phishing campaigns more successful by tracking victims to obtain statistics about engagement. Leveraging these statistics with things that work and things that don’t, hackers could learn how to better target future scams.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









