Contents:
In December 2021, a new tendency in phishing attempts appeared, with cybercriminals exploiting the Google Docs commenting feature to send out emails that seemed legitimate.
Before that,
In June, Avanan reported on an exploit in Google Docs that allowed hackers to easily deliver malicious phishing websites to end-users. Now, hackers have found a new way to do the same thing.
Last October, it was reported that hackers could easily send malicious links through comments in Google apps like Docs and Slides. This known vulnerability has not been fully closed or mitigated by Google since then.
Because numerous employees who work or collaborate remotely use Google Docs, the majority of the recipients of these emails are familiar with the messages. As Google is being swindled into sending these emails, the likelihood of them being flagged as possibly dangerous is essentially nil.
The Attack
In the recently published study conducted by Avanan is explained that during this type of attack, cybercriminals post a comment to a Google Doc. The comment mentions the victim with an @.
An email is automatically sent to the target’s inbox as a result of this action. The entire comment, including the malicious links and content, is included in that email, which comes from Google. Furthermore, only the hacker’s name is displayed, the email address is hidden.
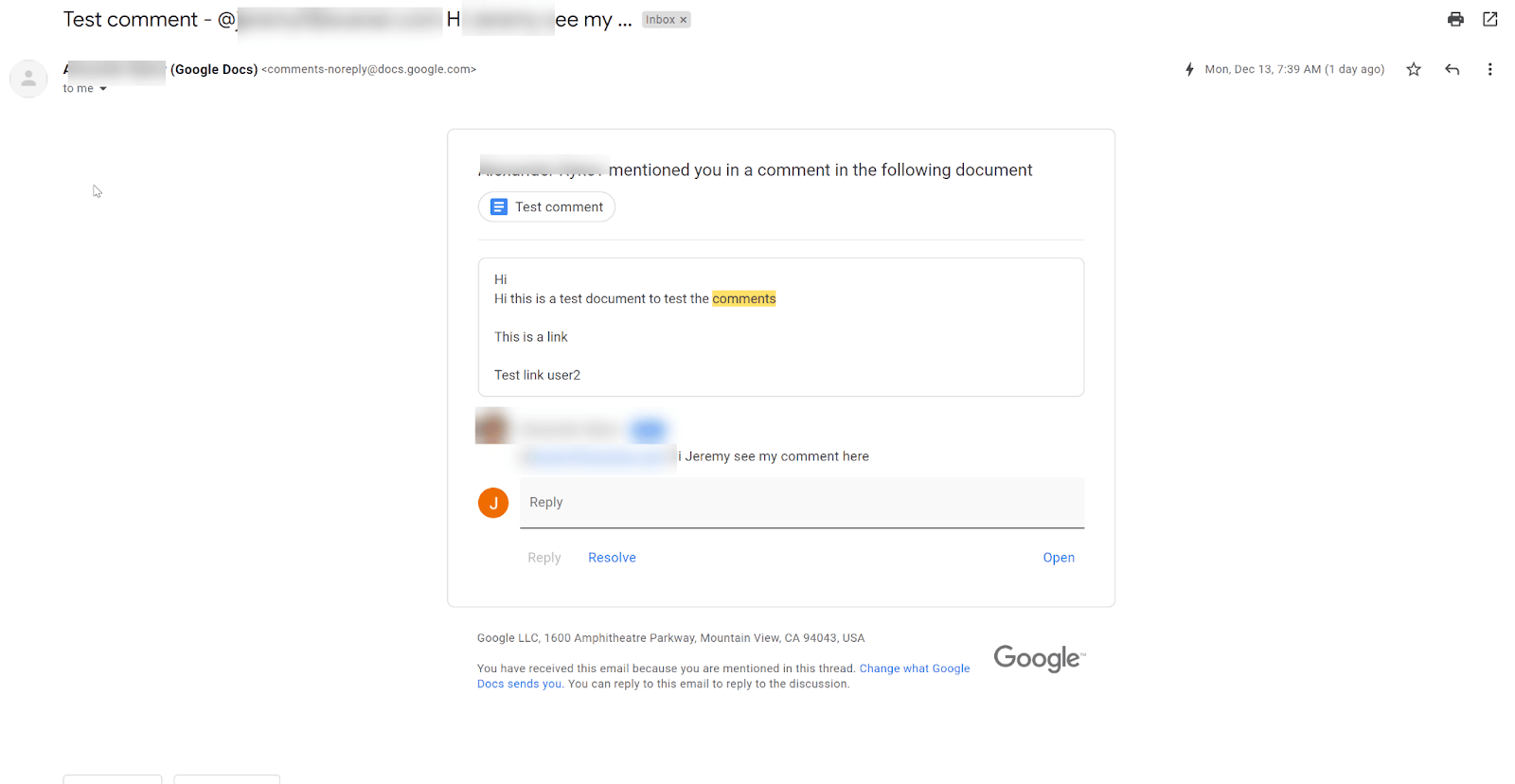
As explained by BleepingComputer, the email comment can contain harmful links that could result in malware dropping websites or phishing webpages, indicating that there are no checking/filtering mechanisms in place.
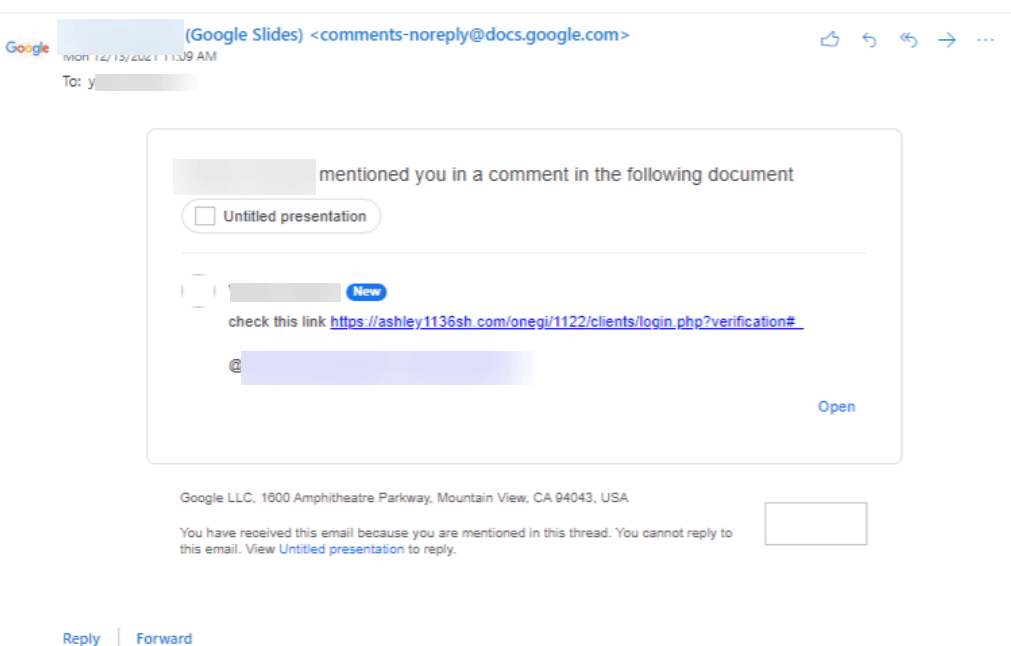
In this email-based campaign, cybercriminals discovered a way to send malicious URLs via Google Docs and other Google collaboration tools. It appears to primarily target Outlook users, but not entirely, according to researchers.
Malicious actors used over 100 different Gmail accounts to attack over 500 inboxes across 30 businesses.
How to Stay Safe?
Security experts can take the following steps to safeguard against these attacks:
- Before clicking on Google Docs comments, advise users to double-check the email address in the comment to make sure it’s authentic;
- Remind end-users to practice basic cyber hygiene, such as double-checking links and grammar;
- When in doubt, contact the legitimate sender and verify that they intended to send that document;
- Implement security solutions that protect the entire suite, including file-sharing and collaboration applications.
How Can Heimdal™ Help You?
Heimdal Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.

If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










