Contents:
A new malware named “NullMixer” is making waves as it infects Windows devices with a dozen different malware families simultaneously. The malware is infecting devices through fake software cracks promoted on malicious websites on Google Search.
Using a single Windows executable to spawn 12 separate malware families, NullMixer serves as an infection funnel, resulting in over 20 infections running on a single device. These include malware loaders, bankers, fake Windows system cleaners, clipboard hijackers, cryptocurrency miners, and password-stealing trojans.
How the Malware Spreads?
According to BleepingComputer, the distributors of the malware are using “blackhat SEO”, to display the websites hosting the fake cracks and software activators in high search positions on Google. The news outlet tested the claim by searching for “software crack” on Google’s search engine, and many of the sites said to be distributing the malware were highly ranked in search results.
When unaware users try to download software from these websites, they are instead taken to other malicious websites that drop a password-protected ZIP archive with a copy of the NullMixer dropper. Users downloading cracks typically ignore AV warnings since they frequently need to edit game files.
Launching the Malware
Typically, NullMixer is downloaded as files with names that sound like “win-setup-i864.exe,” which, when run, produce a new file called “setup installer.exe.” The newly produced file then triggers a chain reaction which allows the malware to infect the machine. The file launches another executable called “setup_install.exe”, which then launches a third file. This third file is the one launching all the malware in the compromised machine, by using a hardcoded list of their names and the Windows’ “cmd.exe” tool.
Some of the malware families dropped by NullMixer include Redline Stealer, Danabot, Raccoon Stealer, Vidar Stealer, SmokeLoader, PrivateLoader, ColdStealer, Fabookie, PseudoManuscrypt, and more.
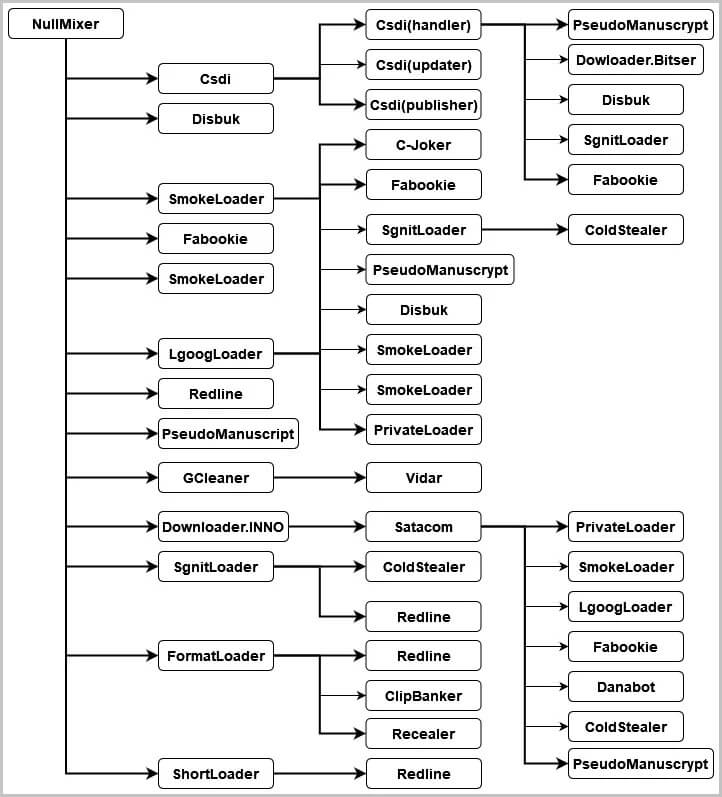
Malware Strains Dropped by NullMixer (Source)
It is unclear why the operators of NullMixer chose to install and launch all these malware families simultaneously, as it would be practically impossible for the malware to run on a breached machine and to not generate symptoms of compromise for the victim to observe the infection.
Some symptoms that your machine has been infected with NullMixer could include heavy hard disk activity, increased CPU and memory utilization, unusual windows opening for no reason, or other performance issues.
Therefore, NullMixer is less of a covert threat and more of a disastrous encounter that will probably only be remedied by a Windows reinstall, so users must always consider the risks of downloading executables from unsafe sources.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










