Contents:
A new IoT bug was discovered that impacts devices that connect through the cloud platform named ThroughTek.
Products that make use of the Kalay network are the ones affected, counting to millions of them. Among these, we can name appliances from producers that engage in video surveillance solutions and IoT systems for home usage.
What Are the Characteristics of the New IoT Bug?
The ones who discovered this IoT bug were Mandiant’s Red Team experts back in 2020. This is now classified CVE-2021-28372, with a score no less than 9.6 out of 10.
According to the BleepingComputer publication, the characteristics of the new IoT bug, defined by researchers while investigating it together with ThroughTek and CISA are:
- The target is the protocol of Kalay.
- This is a mobile and desktop software application kit.
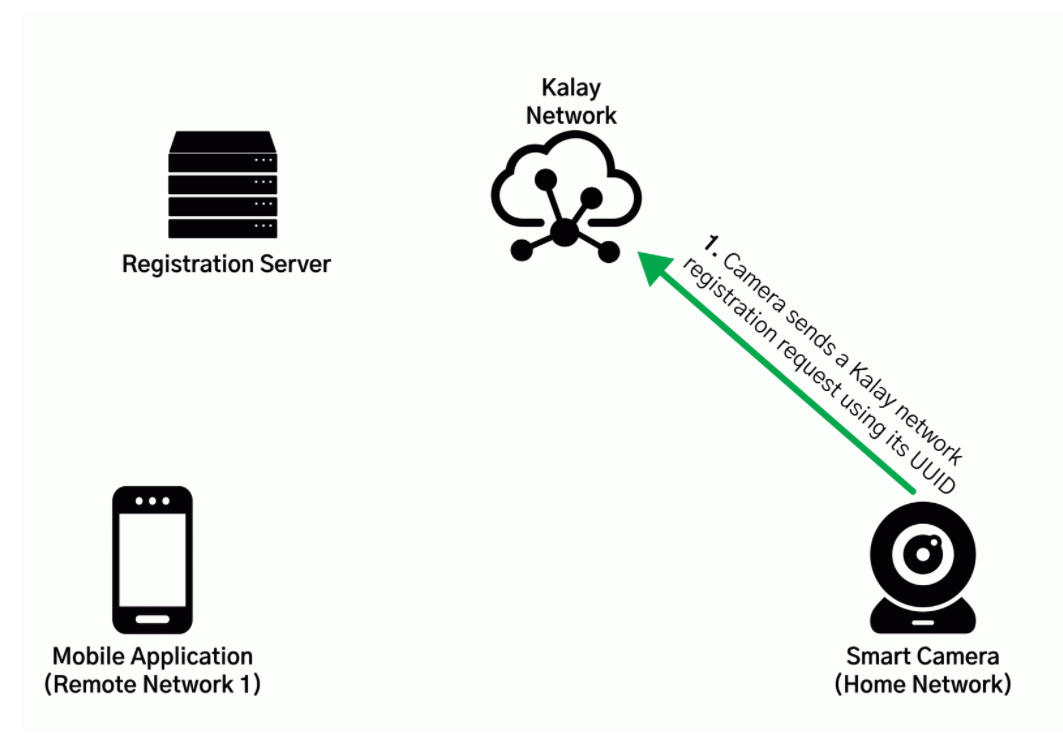
- Connecting a device to the Kalay network could be managed only via the UID (Unique Identifier).
- This will be generated by the vendor through a web-hosted API
- If hackers get this UID, they will connect a compromised device to the Kalay network.
- This leads to credential theft: threat actors will have access to the users’ data, meaning video or audio information.
Mandiant observed that the binaries on IoT devices processing Kalay data typically ran as the privileged user root and lacked common binary protections such as Address Space Layout Randomization (“ASLR”), Platform Independent Execution (“PIE”), stack canaries, and NX bits.
Researchers have tested this new IoT bug and they could identify and register devices by the method of a working development of Kalay protocol. They could also authenticate and connect to the remote customers or operate video information. Later on, a proof of concept code was built and what they managed with this was to impersonate a device on the Kalay network.
What Mitigation Measures Experts Recommend
ThroughTek and Mandiant came with some mitigation measures.
ThroughTek released an updated security advisory of the 13th of August to mitigate the new IoT bug. They recommend:
- AuthKey and DTLS (Datagram Transport Layer Security) should be enabled when version 3.1.10 or higher of ThroughTek SDK is in use. It will keep data safe while in transit.
- Older versions of ThroughTek SDK before v3.1.10 should be updated to v3.3.1.0 or v3.4.2.0. Then, of course, perform the AuthKey and DTLS enablement.
In their report, Mandiant experts recommend that APIs with Kalay UIDs should have their security control checked one more time.
Of course, general mitigation measures remain also valid, such as ensuring you are up to date with your software and also that the password you use is a complex one, hard to guess. Avoiding mistrusted network connections when using an IoT device is also a best practice.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security