Contents:
This specific Cisco ASA vulnerability is a cross-site scripting (XSS) vulnerability tracked as CVE-2020-3580. Cisco was the first to disclose the vulnerability as they issued a fix in October 202o but it seems that the initial patch issued for the Cisco ASA vulnerability CVE-2020-3580 was incomplete, as a further fix was released in April 2021.
The Cisco ASA is a cybersecurity perimeter-defense appliance that combines firewall, antivirus, intrusion prevention, and virtual private network (VPN) capabilities, therefore the successful exploitation in regard to this means that unauthenticated, remote attackers might be able to execute arbitrary code within the [ASA] interface.
XSS attacks happen when an attacker is using an online application in order to send malicious code to a distinct end-user, with this malicious content being able to take the shape of a JavaScript segment.
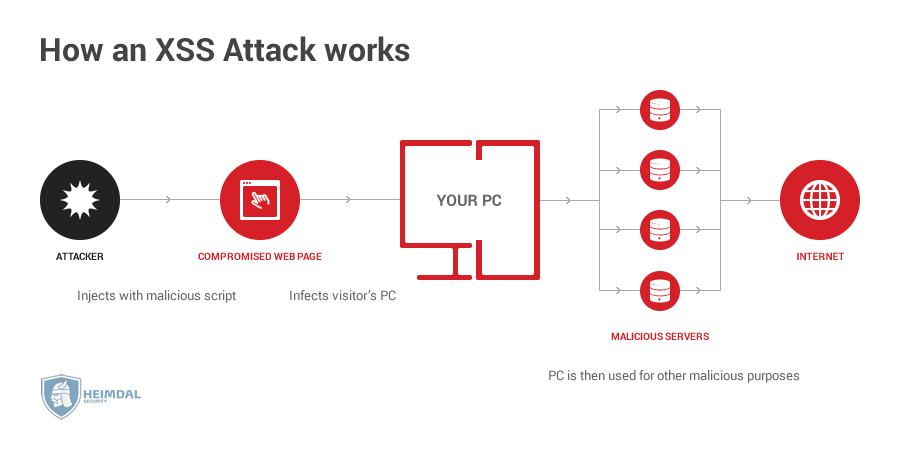
Unfortunately, the possibilities of an XSS attack are almost limitless, oftentimes including the transmission of private data, like cookies or other session information to the attacker.
This Cisco ASA vulnerability is able to allow an unauthenticated threat actor to send targeted phishing emails or malicious links to a user of a Cisco ASA device to execute JavaScript commands in the user’s browser.
A successful exploit could allow the attacker to execute arbitrary script code in the context of the interface or allow the attacker to access sensitive browser-based information.
Hackers Are Exploiting the Cisco ASA Vulnerability
It’s a well-known fact that after a vulnerability is fixed and enough time was given for devices to be upgraded, security researchers usually publish the proof-of-concept (PoC) exploits in an attempt to share the way in which organizations are detecting and preventing associated attacks.
Recently the researchers from Positive Technologies Offensive Team published a PoC exploit for the Cisco ASA CVE-2020-3580 vulnerability on Twitter, that was showing the way in which the exploit was able to display a JavaScript alert in the user’s browser when they visit a specially crafted malicious webpage.
?PoC for XSS in Cisco ASA (CVE-2020-3580)
POST /+CSCOE+/saml/sp/acs?tgname=a HTTP/1.1
Host: ciscoASA.local
Content-Type: application/x-www-form-urlencoded
Content-Length: 44SAMLResponse=”><svg/onload=alert(‘PTSwarm’)> pic.twitter.com/c53MKSK9bg
— PT SWARM (@ptswarm) June 24, 2021
The attackers did not need too much time to start actively exploiting the vulnerability as Tenable received reports that attackers are exploiting the CVE on affected devices but did not say what malicious activity was being performed.
Tenable has also received a report that attackers are exploiting CVE-2020-3580 in the wild.
It’s important to note that it is crucial for administrators to patch any vulnerable Cisco ASA devices so threat actors cannot exploit them as threat actors are now able to actively exploit the vulnerability.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security