Contents:
Since September 2021, over a thousand vulnerable Redis servers online have been infected by a stealthy malware dubbed “HeadCrab”, designed to build a botnet that mines Monero cryptocurrency.
At least 1,200 servers have been infected by the HeadCrab malware, which was first discovered by Aqua Security researchers Nitzan Yaakov and Asaf Eitani.
This advanced threat actor utilizes a state-of-the-art, custom-made malware that is undetectable by agentless and traditional anti-virus solutions to compromise a large number of Redis servers. (…) We discovered not only the HeadCrab malware but also a unique method to detect its infections in Redis servers. Our method found approximately 1,200 actively infected servers when applied to exposed servers in the wild.
HeadCrab Attack Flow
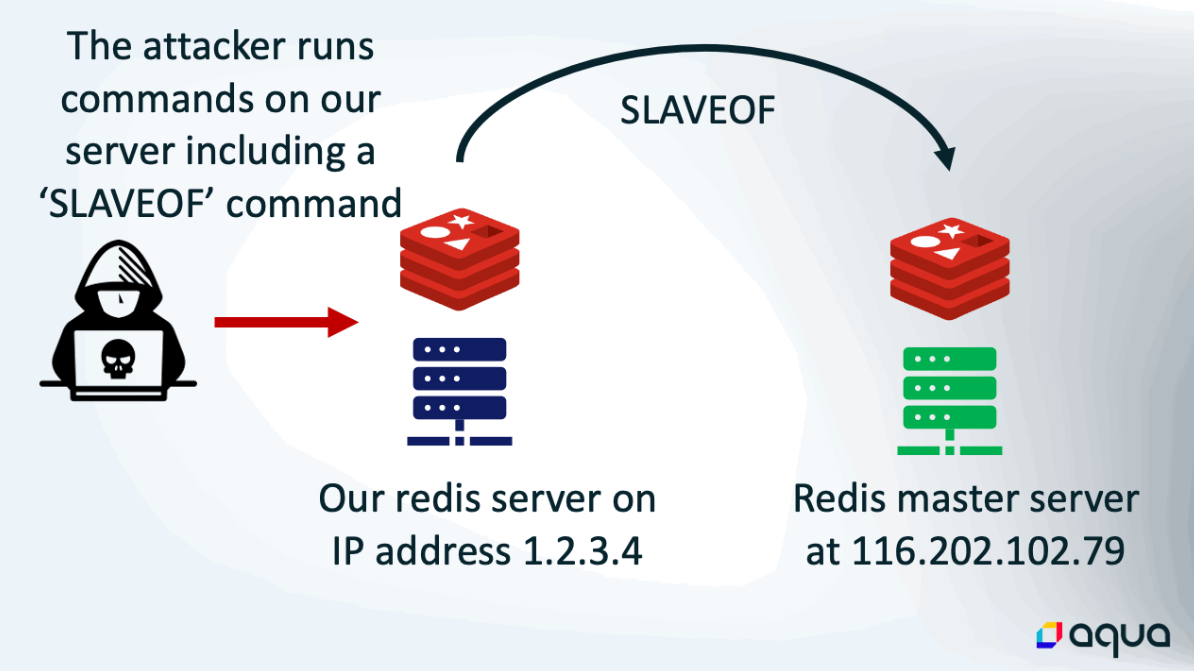
The threat actors behind this botnet exploit the fact that Redis servers do not have authentication enabled by default, as they are meant to be used within an organization’s network and should not have Internet access.
If administrators fail to secure them and unintentionally set them up so that users outside of their local network may access them, attackers can quickly infiltrate and hijack them using malicious tools or malware, explains Bleeping Computer.
Once they have gained access to servers that don’t require authentication, the threat actors execute a ‘SLAVEOF’ command to synchronize a master server under their control in order to distribute the HeadCrab malware onto the newly hijacked system. After being installed and launched, HeadCrab gives the attackers complete control of the targeted server and adds it to their crypto mining botnet.
It can evade anti-malware software by running in memory on infected machines, and Aqua Security’s analysis of sample data has turned up no detections on VirusTotal.
To further avoid detection, it wipes all activity records and only contacts other servers under its master’s control.
The attacker communicates with legitimate IP addresses, primarily other infected servers, to evade detection and reduce the likelihood of being blacklisted by security solutions. (…) The malware is primarily based on Redis processes which are unlikely to be flagged as malicious. Payloads are loaded through memfd, memory-only files, and kernel modules are loaded directly from memory, avoiding disk writes.
They also discovered that the attackers mostly employ mining pools located on previously compromised servers to complicate attribution and detection. Moreover, the Monero wallet linked to this botnet revealed that the attackers are making an estimated annual profit of roughly $4,500 per worker, which is significantly greater than the average $200/per worker for such activities.
Disable the “Slaveof” Feature
To protect their Redis servers, administrators should ensure that only clients within their networks can access them, disable the “slaveof” feature if it’s not in use, and enable protected mode, which configures the instance to only respond to the loopback address and refuse connections from other IP addresses.
To date, a large number of infections have been reported in China, Malaysia, India, Germany, the United Kingdom, and the United States. The threat actor’s origins are currently unknown.
The results come two months after the cloud security firm revealed Redigo, a Go-based malware that was discovered affecting Redis servers.
The complete analysis of the HeadCrab malware is available here.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








