Contents:
Recently, Australian hospitals have been hit by a wave of Gootkit malware loader attacks that leverage legitimate software like VLC Media Player as cover. To get initial access, Gootkit (also known as Gootloader) is reported to use search engine optimization (SEO) poisoning techniques. It often operates by infiltrating and exploiting legitimate infrastructure and seeding those sites with common keywords.
Gootkit, like other malware of its type, is capable of stealing data from browsers, performing adversary-in-the-browser (AitB) attacks, keylogging, screenshotting, and other malicious activities.
A new report from Trend Micro reveals that the phrases “hospital,” “health,” “medical,” and “enterprise agreement” have been matched with numerous Australian city names, indicating the malware’s expansion outside accounting and legal businesses.
How Gootkit Operates
The initial step of the cyberattack is to redirect users searching for identical keywords to an infected WordPress blog that tricks them into downloading ZIP files containing malware.
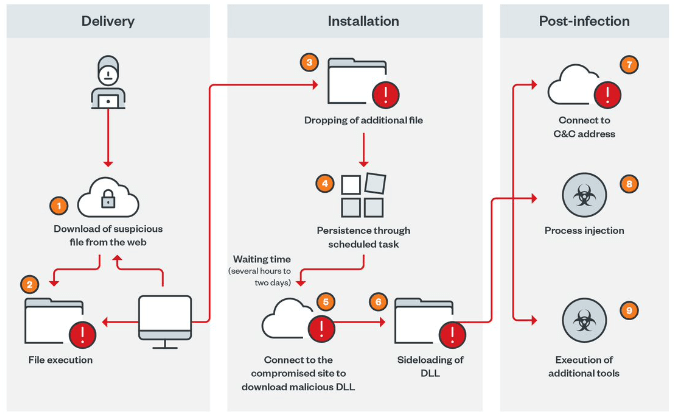
Upon accessing the site, the user is presented with a screen that has been made to look like a legitimate forum.(…) Users are led to access the link so that the malicious ZIP file can be downloaded.
Additionally, the malicious JavaScript code is injected into legitimate JavaScript files at random locations on the compromised website, explains The Hacker News.
The downloaded ZIP file contains a JavaScript file that, when run, uses obfuscation to avoid being analyzed and a scheduled task to stay on the machine. The execution chain then proceeds to a PowerShell script designed to retrieve files from a remote server for post-exploitation activity, which begins only after a waiting time that can range from a few hours to two days.
This latency, which clearly separates the initial infection stage from the second stage, is a distinctive feature of Gootkit loader’s operation. The malicious actors behind [Gootkit] are actively implementing their campaign. (…)The threats targeting specific job sectors, industries, and geographic areas are becoming more aggressive.
Following the wait period, two further payloads are dropped: msdtc.exe and libvlc.dll, the former of which is a valid VLC Media Player binary used to load the Cobalt Strike DLL component, followed by the download of additional tools to aid in discovery.
The full research report published by Trend Micro is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.
Do you work for an NHS Trust? Heimdal is giving you free ransomware licenses to combat growing cyber attacks.
Get your free ransomware protection here.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








