Contents:
A new GLS Spam campaign is underway. It works via an e-mail that informs the victim about some details that need to be filled out for a certain shipment. The email text that we have intercepted was split into multiple HTML spans, so an NLP network analyzers cannot label its contents as spam.
The new GLS Spam sophisticated campaign is currently underway, leveraging advanced obfuscation techniques such as NLP ‘dodging’ to bypass common spam filter. As stated, it works via an e-mail that informs the victim about some details that need to be filled out for a certain shipment. The victim should click on the provided link in order to perform a set of instructions, a link that, as its name says, will lead to a page with “delivery options”.
The e-mail also informs about the fact that as soon as the package is paid, this will be delivered. Additional shipping fees to the tune of 14.99 DKK (2.01 EUR) might apply.
Our CEO, Morten Kjærsgaard, received this kind of email on Sunday, posing as a legitimate email from GLS Denmark.
In the print screen below you can see the original email:

And here is the translation:
Please do not reply to this automatically generated email.
GLS informs you that you need to fill in some instructions for your shipment DK08327164901.
To perform instructions, click on the link below:
Link to delivery options
(Malicious Link Enclosed. Do not Follow!)
It is delivered as soon as the cost is paid.
Additional shipping fees: 14.99 DKK
We apologize for the inconvenience and thank you for your cooperation.
GLS SPAM Campaign: Where Does the IP Come From?
We wanted to dive further into the issue and see where this message is coming from. By using a free tool like IP Tracker we wanted to find more about this IP address.
We discovered that the malicious IP is 209.85.220.41. It seems that this is an IP address from North America, United States, so it’s definitely not sent by GLS Denmark.
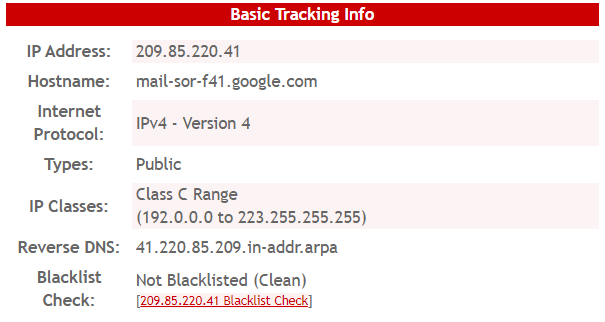
As it comes out from the image above, the threat actors have used a public IPv4 – Version 4 from the C class range.
The name servers vary from 32 to 34 as seen below:
A Closer Look at How This Phishing Campaign Works
Outlining the incident, Heimdal™ has unearthed a new GLS Spam sophisticated campaign. Unlike akin campaigns, the newly dubbed GLS credit card credential phishing campaign leverages NLP obfuscation techniques that renders the message illegible when attempting to inspect or duplicate the contents. It’s modus operandi closely resembles past parcel-delivery phishing scams, whereupon e-mail that informs the victim about some details that need to be filled out for a certain shipment. The victim should click on the provided link in order to perform a set of instructions, a link that, as its name says, will lead to a page with “delivery options”.
On closer inspection of the link’s origin, we have discovered that the user would have been redirected to a forged GLS parcel tracking and payment notification page. Another interesting aspect about the email delivery system is that the attackers employed alphanumerical permutations and/or additions in an attempt to circumvent spam filters. Additional means of obfuscations were not uncovered during the course of the investigation. The duplicitous nature of the forged GLS page (see enclosed picture) wouldn’t have attracted suspicion as to its contents closely resembling the original Danish page.
Upon trying to duplicate the contents of the message by clipboard exportation, the user would have been left with illegible text. Subsequent analysis revealed that the API employed HTML span tags that would have the aforementioned effect on this text if the user would have attempted to interact with it in an unexpected manner. NLP obfuscation to this degree proves that most spam/phishing filters function below par, allowing dangerous emails to pass.
The credit card credential phishing campaign was highly focused, as previous attempts to access the page failed. VPN-tunneling was successful, our team being able to render the page’s contents using a Denmark VPN.
The threat scenario is as follows: the user was prompted via email that a package was in waiting. After landing on the page, the user would have been instructed to supply all necessary credit card details (i.e., card number, expiration month & date, and CVV2 code) in order to receive the package in waiting. The payment information about the extra tax read “GLS Postage [taxes]”. The operation would have been completed by pressing the “Pay” button. However, upon closer examination, it was discovered that the forged page was brokered by an API whose purpose was to relay the credit card information to an undisclosed Telegram account, tracked to Turkey, in the outskirts of Istanbul.
While Heimdal™ is not at liberty to disclose further information regarding the perpetrators, we can state that this is the work of a group of phishers that may have illegally acquired the credit card information of over 3,000 Danish citizens. Furthermore, the API in question has a remarkable bot proliferation rate, meaning that the attackers have the capacity (and infrastructure) to hit more than one target at a time. The investigation is ongoing. We’ll update this article a soon as new information comes to light.
How to Protect Yourself from SPAM emails
Here are some tips on how to stay away from SPAM e-mails:
- make sure your e-mail address is not public, so hackers could easily collect it and send you phishing emails
- if an e-mail seems suspicious, make sure you do not click on that link, like in this example, especially when you don’t know what invoice they are talking about. You can just call the delivery company and see if they really sent the message.
- you should never reply to a SPAM email.
- make sure you have SPAM filtering tools and antivirus software in place.
- make sure you are well informed. For instance, GLS specifically mentions on their website that they never send such kinds of e-mails:
GLS will never send e-mails requesting that goods be paid for using an online payment system, credit card, or bank transfer. GLS does not offer a cash-on-delivery service. Delivery drivers will therefore not collect any payments for parcels. Fraudulent e-mails frequently include spelling and grammatical errors, as well as blurred company logos. If the sender is unknown, attachments and links should generally not be opened. GLS shall not be liable for any damage resulting from fraudulent activities by third parties who abuse the name of GLS.
GLS also advises on what to look for in case of doubt:
Please be aware that if you receive a GLS parcel notification, the following will always be clearly stated:
– that it comes from GLS (e.g. correct header)
– your personal parcel number
– who sent you the parcel
How Can Heimdal™ Help You?
Heimdal™ is always ready for any cybersecurity threat that might occur. We have two stunning products on e-mail protection: Email Fraud Prevention and Email Security. The first manages through 125 analysis vectors to block BEC (Business Email Compromise), CEO fraud, phishing e-mails, and malware. Fraudulent invoices can trigger monetary loss and that’s what our product does, it stop malicious e-mails before they can make you lose money. The latter comes as a cloud and on-premises email protection product that will merge Office 365 support with proprietary e-mail threat prevention to stop malware distributed via e-mails and make sure that supply chain attacks won’t happen.
This article was written in collaboration with my colleague Andra Andrioaie.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







