Contents:
A team of researchers at Ben-Gurion University discovered a new type of attack dubbed Glowworm, which measures an audio output device’s LED power light changes and converts them to audio reproductions, allowing threat actors to listen to private conversations.
According to the researchers,
The Glowworm attack is an optical TEMPEST (Telecommunications Electronics Material Protected from Emanating Spurious Transmissions) attack that can be used by eavesdroppers to recover sound by analyzing optical measurements obtained via an electro-optical sensor directed at the power indicator LED of various devices (e.g., speakers, USB hub splitters, and microcontrollers).
Ever since the COVID-19 pandemic, an increasing amount of organizations have been conducting their daily businesses over platforms such as Microsoft Teams, Google Meet, Zoom, Skype, and others, making their data even more vulnerable to cyberattacks.
Now, as Becky Bracken explains for the Threat Post, these new findings present an entirely new attack vector for electronic communications. The spurious transmission is an almost imperceptible flicker on a speaker, USB hub, splitters or microcontroller LED power.
Federal agencies are required to protect classified information from TEMPEST attacks.
How Glowworm Works
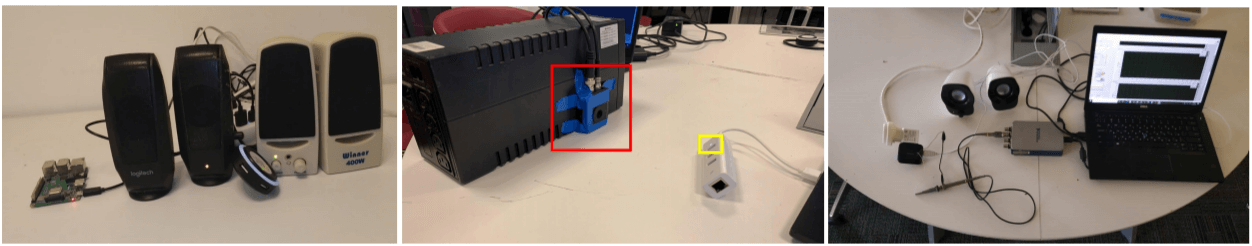
To demonstrate exactly how a Glowworm attack works, the researchers at Ben-Gurion University have pointed a telescope with an electro-optical sensor from 35 meters away at speakers connected to a laptop. The sensor was aimed at the speakers’ power-indicator LED and the laptop screen was not visible.
The team successfully captured a statement played on the speakers and translated by Glowworm.
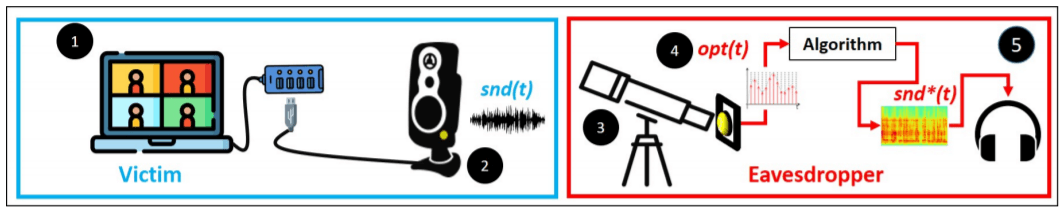
The Glowworm attack can be applied by eavesdroppers to recover: (1) the speech of any person speaking to the victim during a virtual meeting, and (2) any sound (e.g., music from YouTube, videos from the Internet) that is played by the speakers during the virtual meeting, which may or may not be related to the meeting; in this paper, we present the attack in the context of recovering speech from a virtual meeting.
While most business being conducted over platforms like Skype is far from sensitive enough to attract eavesdroppers armed with telescopes and Glowworm, the researchers’ discovery is a good reminder that despite the government’s best efforts, manufacturers can’t always be relied upon to consider these types of TEMPEST attacks.
Although Glowworm is able to spy on victims without drawing attention to itself, people won’t have to worry much about it. Unlike the listening devices, Glowworm does not interact with actual audio – but only with a side effect of electronic devices that produce audio.
Therefore, a Glowworm attack used to spy on a conference call would not capture the audio of the participants in the room – only of the remote participants whose voices are played over the conference room audio system.
We recommend that other hardware manufacturers empirically test whether their devices are vulnerable to the Glowworm attack. (…) Given the cost-driven nature of consumers and the profit-driven nature of manufacturers, known vulnerabilities are often ignored as a means of reducing costs. This fact may leave many electrical circuits vulnerable to Glowworm attacks for years to come.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










