Contents:
ThreatFabric researchers have recently revealed that in August 2021 they came across a new Android banking trojan. Based on the login panel of the C2 server, the researchers could see that it was named S.O.V.A. by its own creators.
What Is SOVA?
The name is not randomly chosen. “Sova” is the Russian word for owl, hence the trojan’s link to the owl’s nature as quiet but efficient in stalking and capturing its victims.
This new banking malware is capable of stealing credentials through overlay attacks, keylogging, hiding notifications, and manipulating the clipboard to insert modified cryptocurrency wallet addresses, with future plans to incorporate on-device fraud through VNC, carry out DDoS attacks, deploy ransomware, and even intercept 2FA authentication codes.
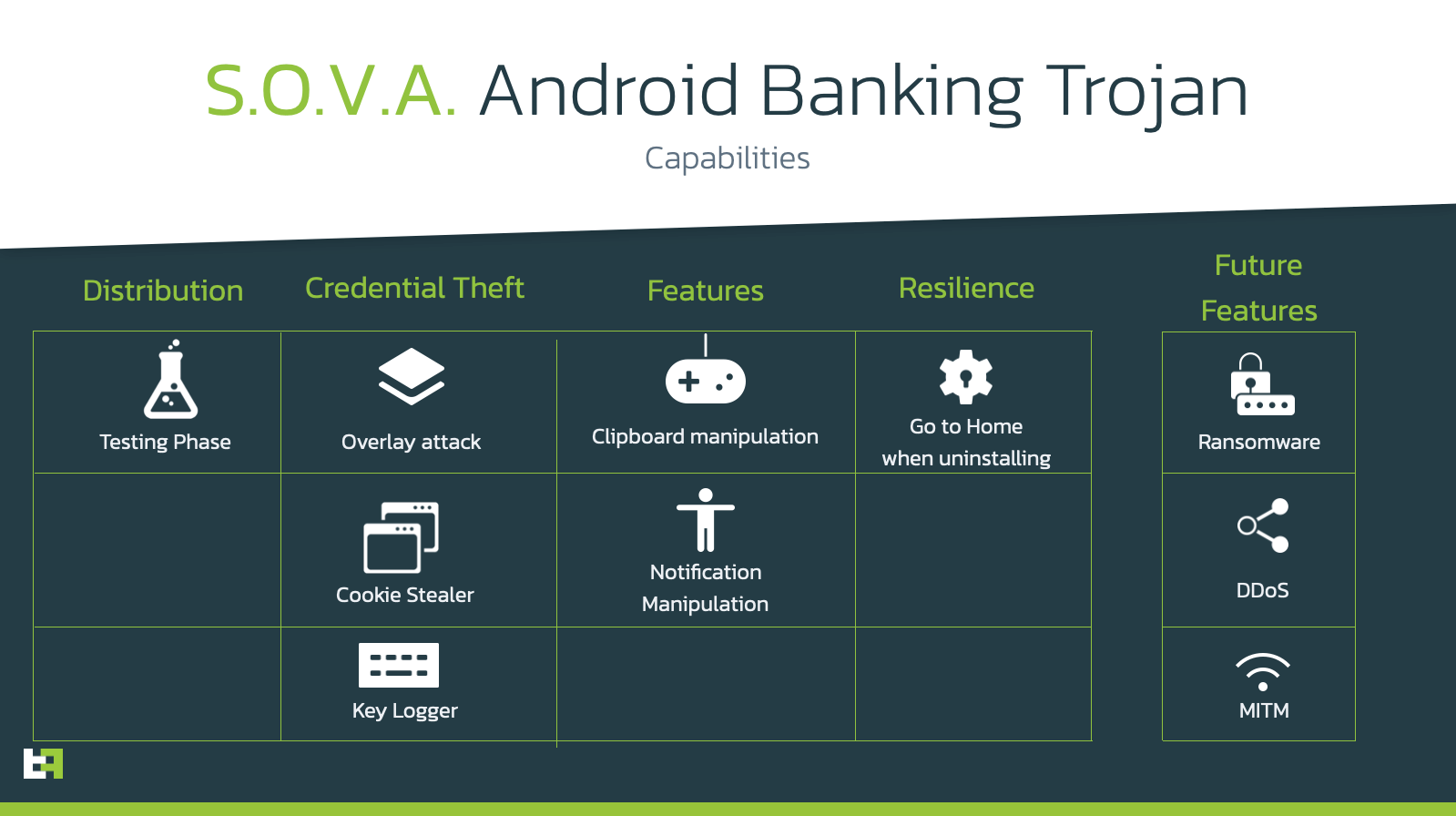
Image Source: ThreatFabric
Additionally, SOVA stands out for its session cookies theft feature that is not as common in Android malware. This functionality allows threat actors to have access to valid logged-in sessions from the users without the need of knowing the banking credentials.
The newly-discovered trojan also stands out for being fully developed in Kotlin, a coding language supported by Android.
Like many others, S.O.V.A. is also taking a page out of traditional desktop malware, confirming a trend that has been existing for the past few years in mobile malware. Including DDoS, Man in the Middle, and Ransomware to its arsenal could mean incredible damage to end users, in addition to the already very dangerous threat that overlay and keylogging attacks serve.
How Does SOVA Work?
SOVA’s main objective is to gather its victims’ personal identifiable information.
The trojan tries its best to remain undetected by abusing the overlay mechanic to trick victims into revealing their credentials, and other sensitive information. This is a common technique used by banking Trojans that create windows identical to a banking app’s login page, which is in fact controlled by the attacker.
The operators revealed that future SOVA releases will have a so-called 3-stage-overlay. Below you can see a demonstration of this 3-stage-overlay that could mean a more advanced and realistic process, probably implying download of additional software to the device.
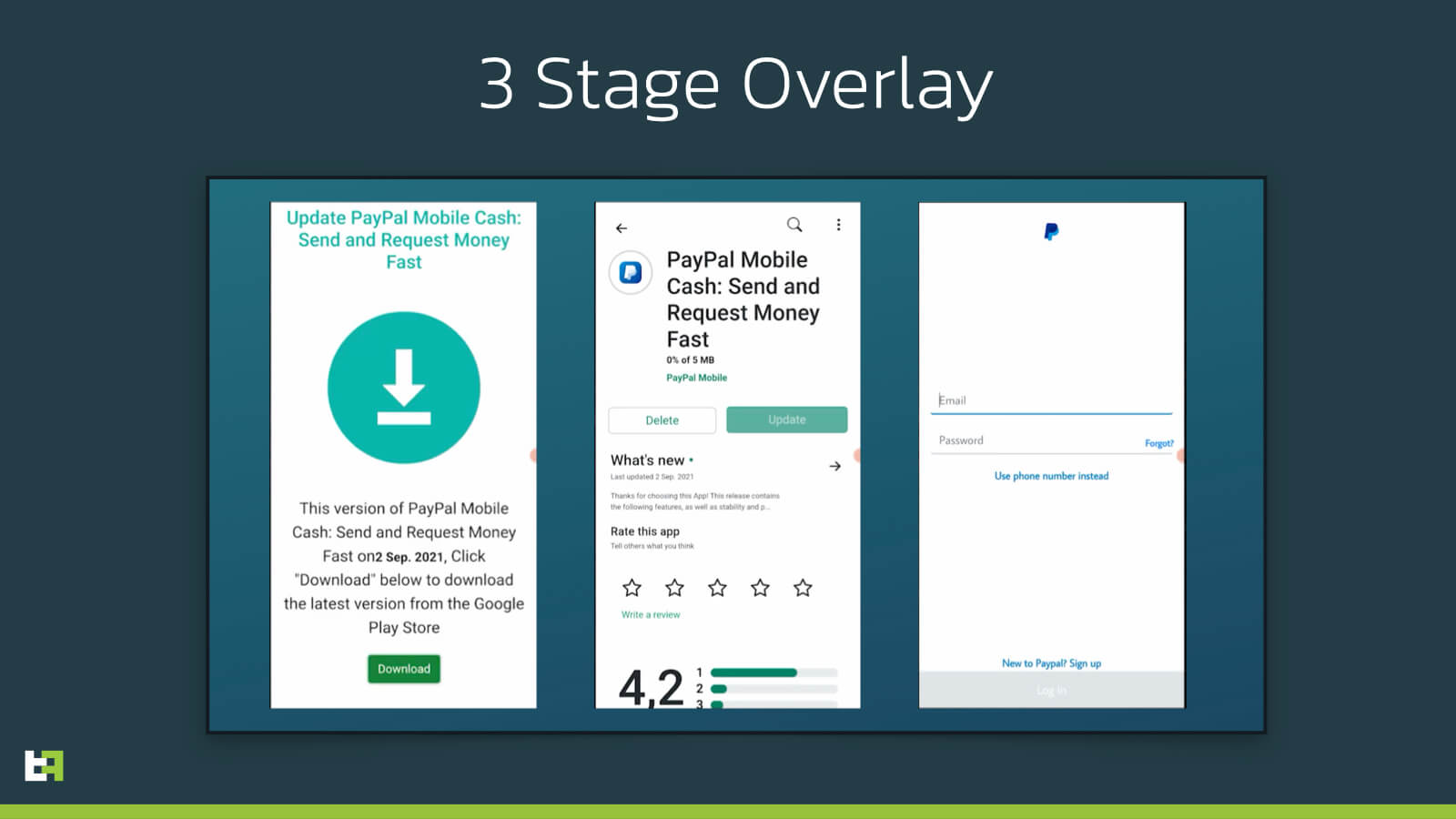
Image Source: ThreatFabric
As detailed in the report, functionalities of the bot include:
- Steal Device Data.
- Send SMS.
- Overlay and Cookie injection.
- Overlay and Cookie injection via Push notification.
- USSD execution.
- Credit Card overlays with validity check.
- Hidden interception for SMS.
- Hidden interception for Notifications.
- Uninstallation of the app.
- Resilience from uninstallation from victims.
However, the operators behind SOVA are very proactive and have also released a detailed roadmap of the features to be included in the future releases of the trojan:
- Automatic 3 stage overlay injections.
- Automatic cookie injections.
- Clipboard manipulation.
- DDoS
- Improved Panel Health.
- Ransomware (with overlay for card number).
- Man-in-the-Middle (MitM).
- Normal Push notifications.
- More overlays.
- 2FA interception.
The threat actors declared in their online advertisement that at the moment they only have mobile banking overlays for banks in Spain and the USA, but as it usually happens with many other Android banking trojans, it is very easy for criminals to add new overlays in a very short amount of time.
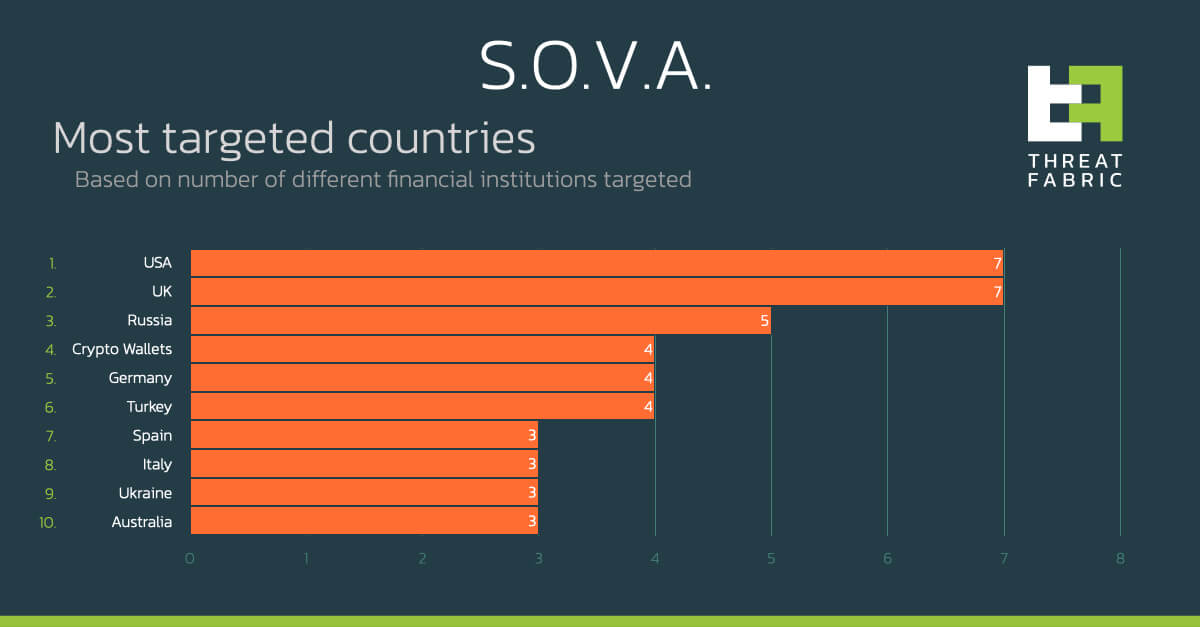
SOVA is still a project in its infancy, and now provides the same basic features as most other modern Android banking malware. However, the author behind this bot clearly has high expectations for his product, and this is demonstrated by the author’s dedication to test S.O.V.A. with third parties, as well as by S.O.V.A.’s explicit feature roadmap.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security