Contents:
WD My Book Live NAS devices have been victims of cyberattacks lately. As we also reported last week, a My Book Live Exploit led to a mass-factory reset of the devices, all users’ data vanishing all of a sudden. At that time, the company thought hackers might be making use of an old 2018 vulnerability. However, it’s quite the contrary. Threat actors applied a new method, operating through a zero-day bug in the system.
What is a Zero-Day Attack?
A Zero-Day attack stands for a computer threat that targets a yet undetected system vulnerability. Basically, security holes in the code allow threat actors’ access to unauthorized data, leading to devices being compromised.
What Generated the My Book Live Exploit?
My Book Live (also known as WD My Book Live NAS) is basically a repository, therefore a device where you can store various files and has the size of a book, hence its name. Its feature that makes this different from other devices is that it can directly connect through a router using an Ethernet cable. This way, users can have access to their data remotely.
After the wave of panic users went through last week, Censys’ Chief Technology Officer Derek Abdine led an investigation in order to determine where did the system flaw lie and how the My Book Live Exploit was made possible.
Western Digital, at a first glance, said that hackers might exploit an old 2018 bug tracked as CVE-2018-18472. This could happen because there was no maintenance since 2015.
However, this was not the reason this time. Wiping out all stored data was possible through a zero-day vulnerability called CVE-2021-35941.
From Abdine’s research, it came out that some parts of the code were not properly written. This allowed a factory reset. Factory resets permit users to return to the initial configuration by erasing all the information from the device. Factory resets are not something unusual, the thing is that they cannot be performed by everyone, thus admin authentication steps are required. This is mandatory precisely because the device connects to the Internet, so it is clearly exposed to threats.
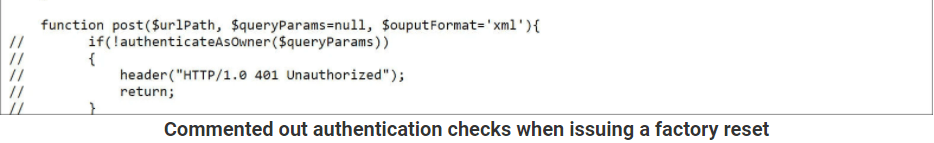
In our case, as described by ArsTechnica, the PHP script “system_factory_restore” from My Book Live that allows resets and is located in aptly file contained a flaw in the code that skipped the authentication part. The developer wrote 5 lines of code to specifically protect the reset command. What is curious is that by using “//” at the beginning of each line, this determined the code to be inefficient by disabling the protection command, in other words, the lines were commented out. This symbol opened the door to threat actors that probably knew the XML format and could skip the authentication steps and reset the device and wipe out all of the data.
However, BleepingComputer also mentions that the My Book Live Exploit Zero-Day attack is not the only one targeting NAS devices. The 2018 CVE-2018-18472 bug did not take a back in the seat and it is said that system vulnerabilities have been allowing cyberattacks in these appliances for a while now. Hackers could use this flaw to add the devices to a botnet permitting them to execute commands, steal data or even perform DDoS attacks.
If the 2 performed bugs have the same authors or not and why were 2 different attacks necessary, is still not clear.
Recommendations from Western Digital
Western Digital, the company that produces these devices, has recently announced the measures the will be implemented to fight against this My Book Live Exploit.
- Affected users will benefit from data recovery services and a trade program through which they can upgrade to MyCloud starting July.
- The other users are advised to interrupt the connection of My Book Live and My Book Live Duo to the internet as a threat prevention measure.
- They also provided new updates on the zero-attack matter.
We have determined that the unauthenticated factory reset vulnerability was introduced to the My Book Live in April of 2011 as part of a refactor of authentication logic in the device firmware. The refactor centralized the authentication logic into a single file, which is present on the device as includes/component_config.php and contains the authentication type required by each endpoint. In this refactor, the authentication logic in system_factory_restore.php was correctly disabled, but the appropriate authentication type of ADMIN_AUTH_LAN_ALL was not added to component_config.php, resulting in the vulnerability.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










