Contents:
After several Western Digital My Book Live NAS owners all over the world noticed that their devices have been mysteriously wiped clean overnight, Western Digital has declared that it might have been targeted with malicious software.
Western Digital has made a few popular My Book external storage solutions, but the My Book Live became popular for one unique feature. It connected directly to a router through an Ethernet cable, enabling users to access data from the driver remotely.
Of course, that also comes with a higher risk of getting attacked, which may be what happened in this case.
Some users report on Western Digital Community Forums that their devices seem to have been factory reset, while others state they are seeing a page asking for a password they don’t know.
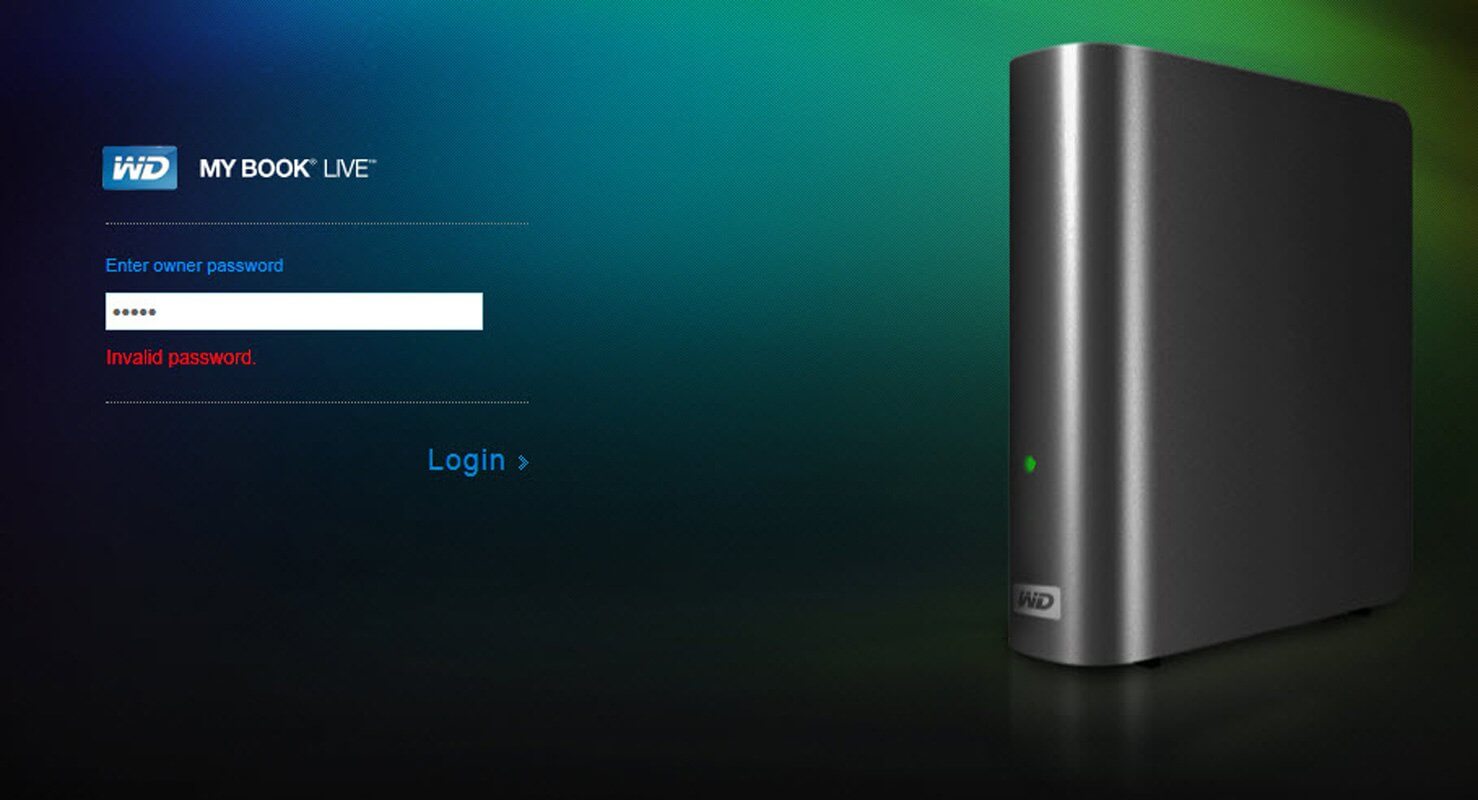
Here are some of the WD My Book owner posts:
I have a WD My Book live connected to my home LAN and worked fine for years. I have just found that somehow all the data on it is gone today, while the directories seem there but empty. Previously the 2T volume was almost full but now it shows full capacity.
The even strange thing is when I try to log into the control UI for diagnosis I was only able to get to this landing page with an input box for “owner password”. I have tried the default password “admin” and also what I could set for it with no luck.
Another user said that they found the following script in the user.log of their drive:
“Jun 23 15:14:05 MyBookLive factoryRestore.sh: begin script:
Jun 23 15:14:05 MyBookLive shutdown[24582]: shutting down for system reboot
Jun 23 16:02:26 MyBookLive S15mountDataVolume.sh: begin script: start
Jun 23 16:02:29 MyBookLive _: pkg: wd-nas
Jun 23 16:02:30 MyBookLive _: pkg: networking-general
Jun 23 16:02:30 MyBookLive _: pkg: apache-php-webdav
Jun 23 16:02:31 MyBookLive _: pkg: date-time
Jun 23 16:02:31 MyBookLive _: pkg: alerts
Jun 23 16:02:31 MyBookLive logger: hostname=MyBookLive
Jun 23 16:02:32 MyBookLive _: pkg: admin-rest-api”
Unlike QNAP devices, which are frequently connected to the Internet being vulnerable to cyber assaults such as the QLocker Ransomware, the Western Digital My Book devices are stored behind a firewall and communicate via the My Book Live cloud servers to offer remote access.
It is obvious that the attacker’s intention was to cause damage as nobody has reported any ransom requests yet.
However, Western Digital didn’t reveal who might be responsible for distributing the software, or whether the organization itself has been compromised by a cyberattack.
All the Western Digital My Book NAS device owners are urged to disconnect the devices from the network until more details about the incident will be revealed.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










