Contents:
Following a prosperous month that brought them a total of $350,000 from victims they extorted by exploiting flaws in QNAP NAS devices, the Qlocker ransomware group is shutting down.
On April 19th, a huge ransomware operation targeting QNAP devices around the world began storing users’ files in password-protected 7zip archives.
Threat actors used 7-zip to transfer files on QNAP devices into password-protected archives with the .7z extension. While the files were being locked, the QNAP Resource Monitor would show several ‘7z’ processes which were the 7zip command-line executable. The victims were supposed to enter a password known only by the hacker to extract these archives.
Also, QNAP possessors discovered a !!!READ_ME.txt ransom message explaining that their files were encrypted and needed to visit a Tor site to pay a ransom in order to recover their files.
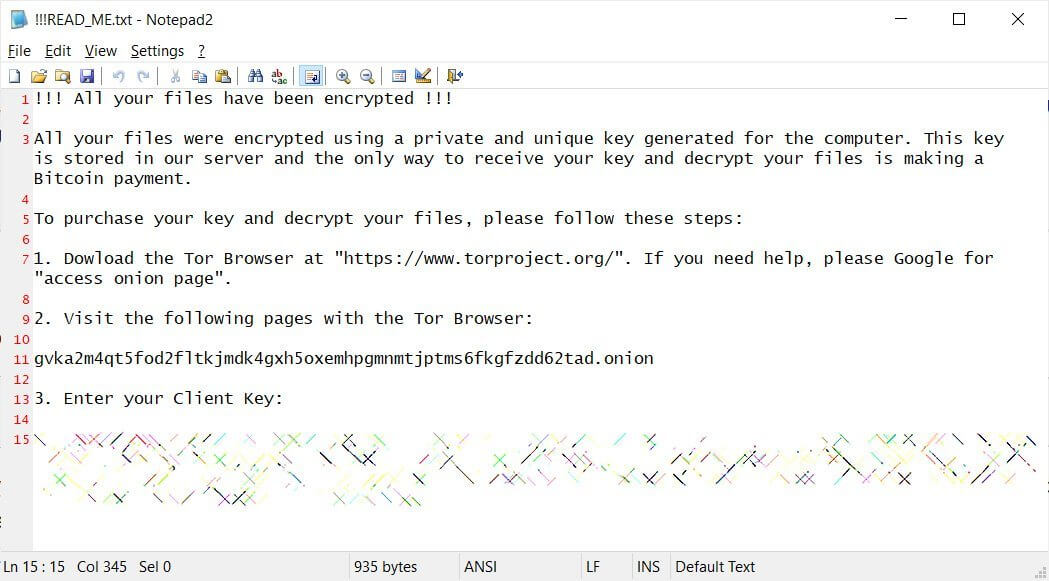
The cybercriminals have been recognized by the Tor website as Qlocker ransomware gang and requested .01 bitcoins, around $550, to obtain the password for their files.
It was eventually established that hackers organized the cyber assault via QNAP flaws revealed not long ago that enabled them to encrypt users’ files employing the built 7-zip app remotely.
This method enabled the hackers to encrypt maybe thousands of devices in the course of a month.
A “This site will be closed soon.” message started to appear on Qlocker Tor sites.
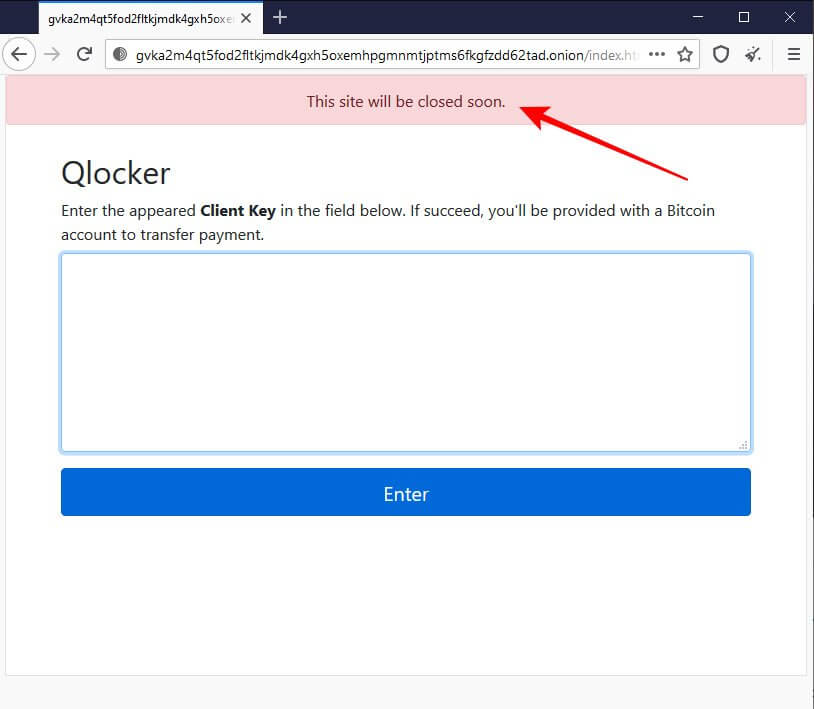
The impacted users announced that after they paid the requested ransom and submitted the transaction ID on the Qlocker Tor site, the site would ask them to pay an extra 0.02 bitcoins in order to recover their files.
According to BleepingComputer, all of the Qlocker Tor sites are no longer available, and victims no longer have a way to pay the ransom.
Following the DarkSide ransomware attack on Colonial Pipeline and pressured by the US law enforcement, the DarkSide ransomware gang ceased operation, and REvil decided to impose restrictions on who they attack.
Several ransomware operations’ Tor sites such as Ako/Ranzy and Everest shut down ever since.
The Qlocker ransomware gang tactic was different. They didn’t ask for millions of dollars to recover files, establishing a $500 ransom instead. This strategy led to many businesses paying the ransom in order to get their files back.
Because the Qlocker ransomware campaign utilized a predetermined set of Bitcoin addresses that victims were rotated through, it has been possible to track how many bitcoins they received in ransom payments.
According to BleepingComputer, approximately 893 victims paid a total of 8.93258497 bitcoins in ransomware.
Today that is worth $353,708, but before this week’s Bitcoin crash, those same bitcoins would be worth almost $450,000.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










