Contents:
Researchers warned about the fact that unpatched Hikvision video systems have become the targets of hackers in an attempt to conduct a cyberattack that has the role to drop a DDoS botnet. The botnet under discussion is dubbed Moobot, being a Mirai-based one.
The company released a patch for this during the month of September, however, Hikvision IP Network Video Recorder (NVR) products that are not yet patched will make for Moobot targets.
Moobot: How It Works
The researchers from FortiGuard Labs published a report on this topic and illustrated how Moobot works. It seems that its modus operandi is based on the exploitation of an existent remote code vulnerability (RCE) in the products of Hikvision.
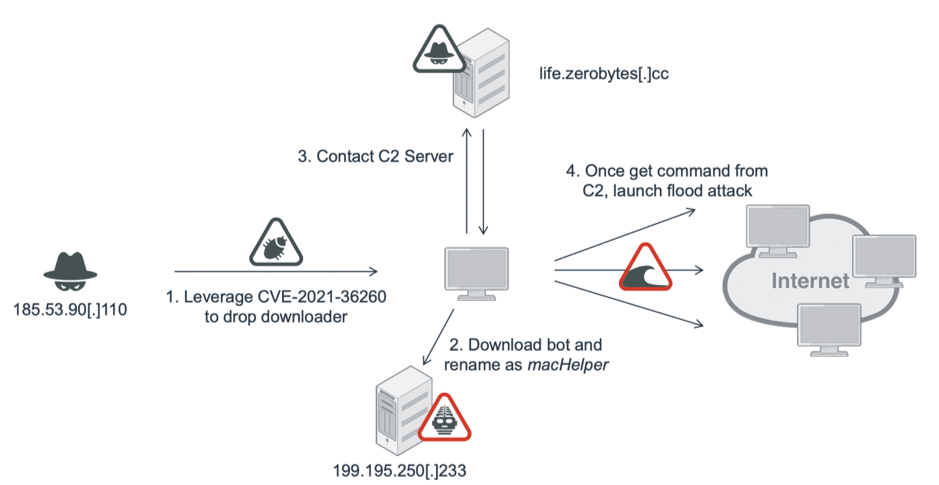
The flaw under discussion was dubbed CVE-2021-36260 and its exploitation has the goal of distributing the botnet named Moobot, which will eventually result in a distributed denial of service (DDoS) cyberattack.
A hacker usually looks for a system that is vulnerable. What happens next when he finds it is that a downloader will drop the malware, in this case, as the researchers underlined, it’s about Moobot which can be described as a Mirai variant that encompasses Satori code traces.
Its most obvious feature is that it contains the data string “w5q6he3dbrsgmclkiu4to18npavj702f”, which is used in the “rand_alphastr” function. It is used to create random alphanumeric strings with different purposes, such as for a setup process name or to generate data for attacking. (…) Since it is based on Mirai, the botnet also contains a data section to store its configuration. (…) After getting the C2 server (life.zerobytes[.]cc) from its configuration, it starts sending heartbeat (\x00\x00) packets and then waits for the next control command from the C2 server. Once the victim system receives the command, it starts a DDoS attack to a specific IP address and port number.
Here is also an illustration from the report depicting an attack scenario:
What Is Mirat Botnet?
As Vladimir highlights in his article on Mirai botnet, Mirai wreaked havoc in 2016, when it took down various targets, among which we can mention Krebs on Security, the DNS provider named Dyn, and also the private cloud provider named OVH. The particularity of Mirai lied in its IoT propensity. Usually, botnets target either servers or PCs and networking peripherals, but Mirai focused on IoT devices.
How Can Heimdal™ Help?
Since Mirai targets domain name systems in its attacks among other methods, an efficient tool that filters DNS traffic and prevents future threats will be a good approach to the risk posed by this botnet. Our Threat Prevention, awarded with the Cloud-Delivered Security Solution of the Year at the Networking Computer Awards 2021, can help you scan the DNS, HTTP, and HTTPS traffic and detect malicious activity. Inbound and outbound traffic is scanned and threats are prevented with a 96% accuracy, as the product encompasses successfully machine learning, AI-based prevention, and also cybercrime intelligence.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










