Contents:
A Hive ransomware affiliate has been deploying multiple backdoors, including the Cobalt Strike beacon, on Microsoft Exchange servers that are vulnerable to ProxyShell security issues.
As explained by my colleague, Cobalt Strike is a threat emulation software released in 2012 which can be used to deploy beacons on systems to simulate cyberattacks and test network defenses.
The cybercriminals then carry out network reconnaissance to determine potential weaknesses, collect admin login information, exfiltrate sensitive information, and deploy the file-encrypting payload.
The information comes from Varonis, an American software company that was called in to investigate a ransomware incident on one of its clients.
How Did It Happen?
ProxyShell is a group of three security flaws in the Microsoft Exchange Server that enable remote code execution on vulnerable deployments without authentication. As per BleepingComputer, the three vulnerabilities are CVE-2021-34473, CVE-2021-34523, and CVE-2021-31297, with severity ratings varying from 7.2 (high) to 9.8. (critical).
After exploits became available, numerous cybercriminals abused the vulnerabilities, including ransomware organizations such as Conti, BlackByte, Babuk, Cuba, and LockFile.
Although the security flaws were considered fully fixed since May 2021, comprehensive technical aspects about them were only made publicly available in August 2021, and malicious exploitation began shortly after.
The fact that Hive’s affiliate was successful in exploiting ProxyShell in a recent attack shows that there is still room for targeting vulnerable servers.
After the exploitation of ProxyShell, the attackers placed four web shells in an accessible Exchange directory and ran PowerShell code with elevated privileges to download Cobalt Strike stagers.
The web shells employed in this cyberattack were obtained from a public Git repository and were simply changed the name to avoid being detected during manual checks.
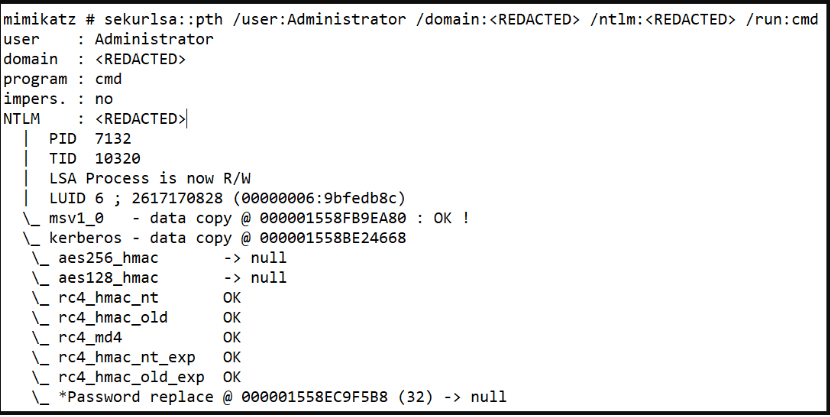
The malicious actors then used Mimikatz, an open-source, credential-dumping application that extracts account username and password information, to steal the password of a domain admin account and execute lateral movement, gaining access to more network assets.
The cybercriminals then conducted extensive file search operations to find the most valuable information in order to compel the victim to pay more money as ransom.
Among others, analysts at Varonis have discovered remains of:
- dropped network scanners,
- IP address lists,
- device and directory enumerations,
- RDPs to backup servers,
- scans for SQL databases.
At last, a ransomware payload called “Windows.exe” was dropped and ran on various devices after all files had been exfiltrated.
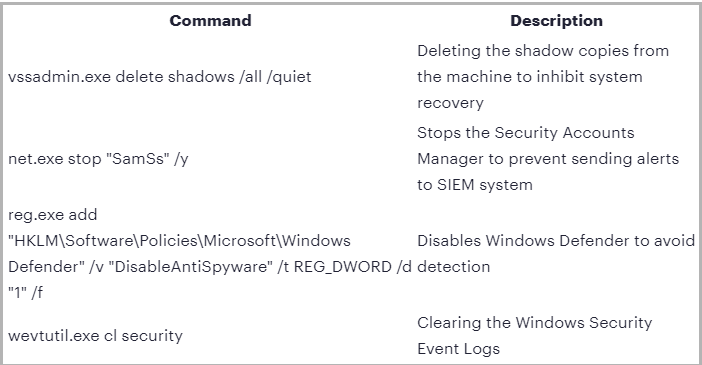
Before the encryption, in order to deactivate alerts, the payload:
- deleted shadow copies,
- disabled Windows Defender,
- cleared Windows event logs,
- killed file-binding processes,
- stopped the Security Accounts Manager.
Hive has come a long way since it was initially discovered in the wild in June 2021, and it has had such a successful start that the FBI has published a report on its methods and indicators of compromise.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










