Contents:
A significant increase in “TrojanOrders” attacks against Magento 2 websites is being attributed to at least seven hacker groups. These attacks take advantage of a flaw that lets threat actors infiltrate unprotected servers.
Hacking groups are fighting each other to take control of the infected sites. Almost 40% of the Magneto 2 websites are being targeted.
These attacks are used to inject malicious JavaScript code into an online store’s website, which can cause serious disruption and possible credit card theft attempts, considering the busy period of Black Friday and Cyber Monday. The trend is expected to continue to grow as we are heading toward Christmas when online shops are the most vulnerable.
Explaining the TrojanOrders Attack
The major Magento 2 CVE-2022-24086 vulnerability is the target of the TrojanOrders attack, which enables unauthenticated attackers to run code and inject RATs (remote access trojans) on unpatched websites.
Even if Adobe fixed the CVE-2022-24086 in February 2022, cybersecurity experts say that many Magneto 2 sites still need to be patched.
To perform TrojanOrders attacks, hackers generally create accounts on the target website and make orders with malicious template code in the name, VAT, or other fields.
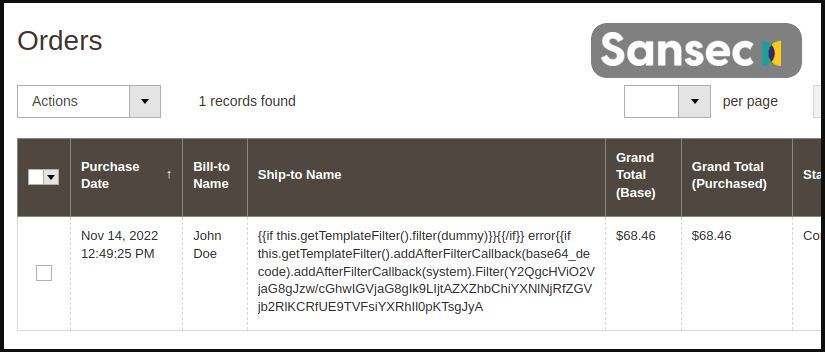
Example of a malicious order on the backend (Source: Sansec)
The above attack will inject a copy of the “health_check.php” file, a method frequently used as observed by Sansec. The file contains a PHP backdoor that can run commands sent via POST requests. Once within the website, the attackers install a remote access trojan to get access permanently and the capacity to carry out more complicated operations.
Ultimately, the attackers will modify the website to include the malicious JavaScript that steals customers’ information and credit card numbers when purchasing products in the infected store.
Long Overdue Resurgence
There are multiple reasons we are seeing a surge in such attacks lately. A large number of Magneto 2 websites remain vulnerable to such attacks months after the patches became available.
Another reason behind the surge is that PoC (proof of concept) attacks have been around for a while, and so exploit kit creators can use them in their products and make money by selling them to less experienced hackers.
According to BleepingComputer, the Magneto exploits are so abundant they are sold for as low as $2,500, whereas in early 2022 they would cost between $20,000 and $30,000.
Additionally, because of the increased website traffic during the holiday season, malicious orders and code injections may be more likely to go unnoticed, making the timing of these attacks optimal.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










