Contents:
Microsoft is once again confronted with reports of a new zero-day vulnerability being used to hack Exchange servers which might have led to the launch LockBit ransomware attacks.
In July 2022, two servers operated by a customer of the South Korean AhnLab cybersecurity firm were infected with LockBit 3.0 ransomware.
Another Zero-Day Vulnerability
As reported, threat actors initially deployed web shell on a compromised Exchange server and needed just 7 days to escalate privileges to Active Directory admin, stealing roughly 1.3 TB of data before encrypting systems hosted in the network.
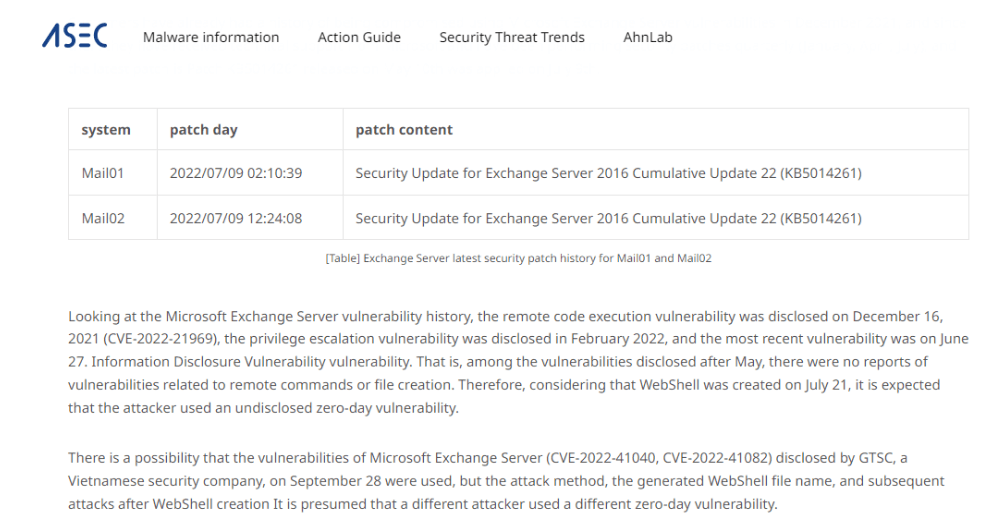
AhnLab`s forensic analysis experts claim the Exchange servers were likely hacked using an “undisclosed zero-day vulnerability,” at a time when Microsoft is already working on security patches to address two actively exploited Microsoft Exchange zero-days, CVE-2022-41040 and CVE-2022-41082. AhnLab experts believe the one used to gain access to the Exchange server in July might be different since attack tactics differ. However, other experts do not seem too convinced that it might not be a zero-day altogether.
It is worth noting that the analysis is no longer accessible on the cybersecurity company`s site.
Undiscovered Vulnerabilities
Whether this event was truly caused by a zero-day flaw or not, there is a security vendor that claims it knows of three other undisclosed Exchange flaws and provides “vaccines” to block exploitation attempts. Discovered by Zero Day Initiative vulnerability researcher Piotr Bazydlo and already reported to Microsoft, they are tracked as ZDI-CAN-18881, ZDI-CAN-18882, and ZDI-CAN-18932.
Microsoft is yet to disclose any information regarding these three security flaws since they were reported by Trend Micro Zero Day Initiative, nor has a CVE ID been assigned to track them.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







