Contents:
The LockBit ransomware operation takes a severe blow after a developer has leaked online the builder of their newest ransomware encryptor. The encryptor, codenamed LockBit Black, was officially released in June, after being in tests for two months.
Compared with the old version, the newest version of the encryptor boasted new anti-analysis features, a ransomware bug bounty program, and new extortion methods.
The Builder Leaked on Twitter
According to security researcher 3xport, a newly registered Twitter user named “Ali Qushji” declared that their team hacked Lockbit’s servers and found a builder for the LockBit Black (3.0) ransomware encryptor.
Unknown person @ali_qushji said his team has hacked the LockBit servers and found the possible builder of LockBit Black (3.0) Ransomware. You can check it on the GitHub repository https://t.co/wkaTaGA8y7 pic.twitter.com/cPSYipyIgs
— 3xp0rt (@3xp0rtblog) September 21, 2022
After 3xport announced the breach, VX-Underground revealed that on September 10th, a user going by the handle “protonleaks” approached them and offered to give a copy of the builder. The relationship between the two Twitter users is still unknown. In contrast to Ali Qushji’s allegations, VX-Underground said that LockBitSupp, the LockBit operation’s public representative, claims that they were not hacked and that instead, an angry developer leaked the private ransomware builder.
The leaked builder is indeed legitimate, BleepingComputer declares after multiple security researchers confirmed the fact.
Anyone Can Use The Builder
The enterprise has suffered a serious loss as a result of the disclosure because more threat actors will use it to launch their attacks. Anyone can easily create the executables needed to start their operation using the builder, which includes an encryptor, a decryptor, and customized tools to run the decryptor in particular ways.
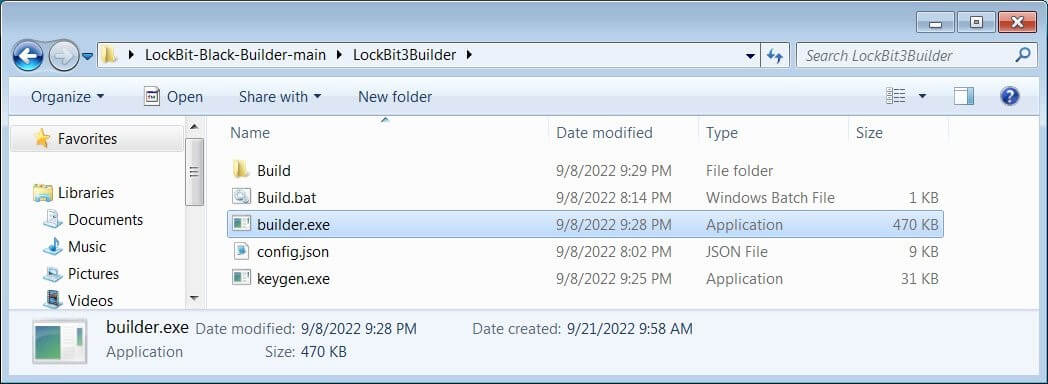
LockBit 3.0 Builder Files (Source: BleepingComputer)
The builder consists of four files, one of them being the “config.json” file. Threat actors can access it and customize the encryptor in multiple ways, including modifying the ransom note, changing configuration options, deciding what processes and services to stop, and even specifying the command and control server that the encryptor.
When testing the builder, BleepingComputer was able to easily modify it to utilize their local command and control server, encrypt their data, and then decrypt them.
This is not the first time a source code or ransomware generator has been leaked online. The Babuk ransomware builder leaked in June 2021, enabling anyone to create encryptors and decryptors. A similar case happened in March 2022, when the Conti ransomware suffered a breach and its source code leaked online.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










