Contents:
Lazarus, a North Korean hacking group, now spreads macOS malware via fake Crypto.com job offers.
They are targeting employees from the crypto space with malicious files that, once opened, can be used to breach crypto companies’ networks. The goal is to steal as much cryptocurrency and NFTs as possible or even carry out corporate espionage acts.
One of the biggest platforms for cryptocurrency exchange, Crypto.com, first came into the public eye in 2021 when it bought and renamed the Los Angeles Staples Center arena into ‘Crypto.com Arena’ and created TV advertisements for its services.
How This Campaign Works
Sentinel One reported that victims are usually targeted on LinkedIn through a direct message that informs them about a job opening at Crypto.com. Then they receive a macOS binary named ‘Crypto.com_Job_Opportunities_2022_confidential.pdf’ posing as a PDF file with details about the offer.
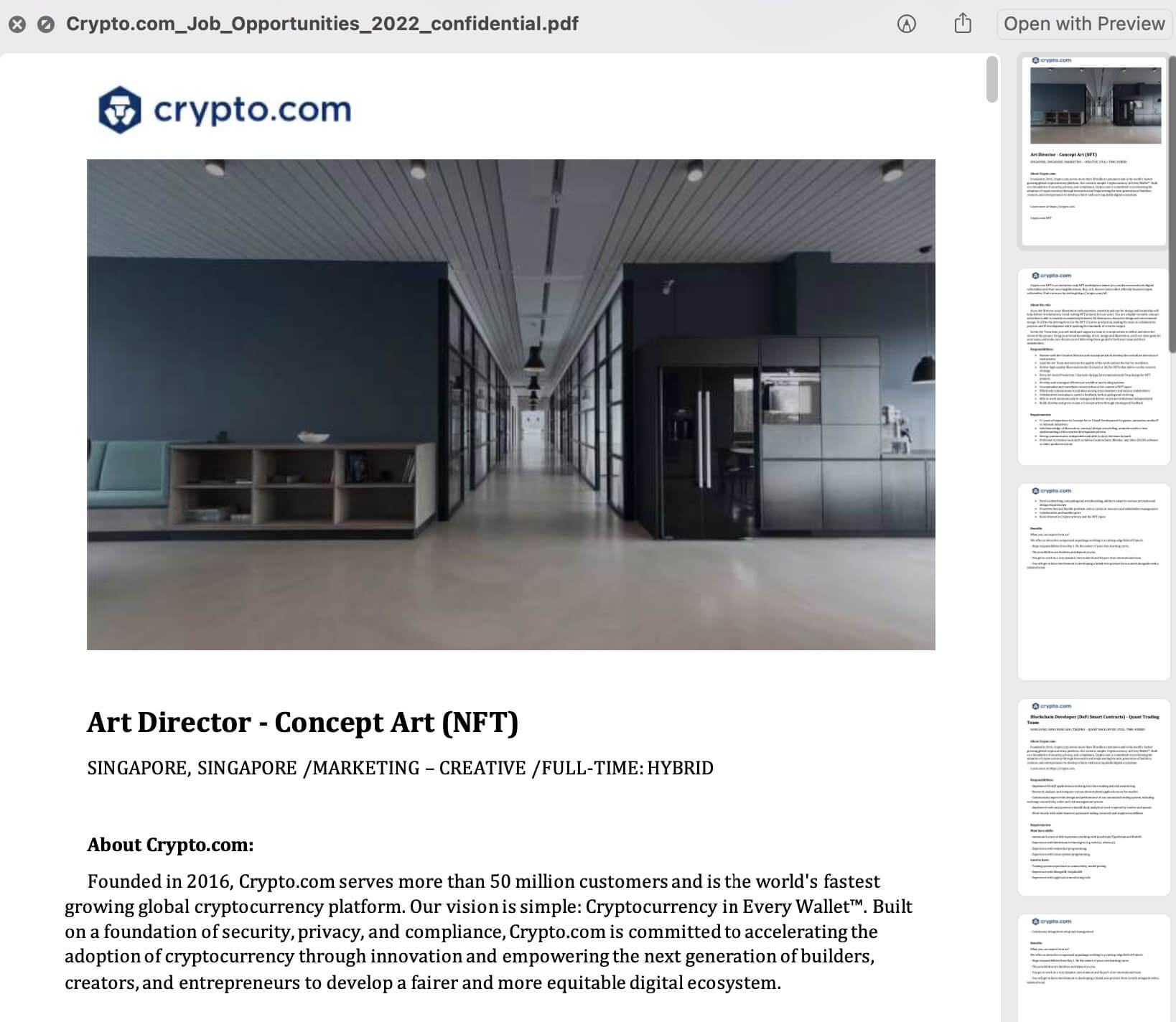
Meantime the Mach-O binary creates a folder in the Library directory of the device (“WifiPreference”) and releases the files for the second and third stages of the malware.
The second stage is “WifiAnalyticsServ.app” that loads a persistence agent (“wifianalyticsagent”), which eventually connects to the C2 server at “market.contradecapital[.]com” to fetch the final payload, “WiFiCloudWidget.”
The security researchers couldn’t retrieve the final payload for analysis due to the C2 being offline at the time of the investigation.
The binaries can bypass Apple Gatekeeper checks thanks to an ad hoc signature that helps them to appear as legitim software.
There are signs that Lazarus hackers will soon change the company that they impersonating in this campaign as they “made no effort to encrypt or obfuscate any of the binaries, possibly indicating short-term campaigns and/or little fear of detection by their targets,” according to Sentinel One.
Operation In(ter)ception
Operation In(ter)ception is a campaign led by Lazarus hacking group since 2020 that focuses on the cryptocurrency industry. It is believed that they managed to steal over $600 million in cryptocurrency until now.
The campaign first started by deploying trojan cryptocurrency wallets and malicious trading apps that steal users’ credentials and empty their accounts.
In April 2022 Lazarus group was linked to an attack over Axie Infinity that resulted in over $617 million worth of stolen Ethereum and USDC tokens. More recently, in August 2022, they impersonated Coinbase and sent fake job offers, targeting IT workers this time.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









