Contents:
The Vice Society ransomware gang declared that it had been behind the recent attack that targeted the capital of the Italian island of Sicily, Palermo. The incident has caused a large-scale service outage.
The cyberattack took place last Friday, and all internet-based services are still down, affecting 1.3 million people and tourists who are there for vacation.
On Monday, the authorities confirmed the gravity of the ransomware attack, explaining that all systems had to be taken offline to control the damage and alerting people that the disruptions could last a few more days.
Because its network was shut down, the incident seemed to be a ransomware attack rather than one of the recent DDoS attacks that impacted the country.
Who’s Responsible for the City of Palermo Attack?
Vice Society ransomware gang has taken credit for the Palermo incident earlier this week when posted an entry on their dark web data leak site, threatening to disclose all stolen data by Sunday if they don’t receive the requested ransom.
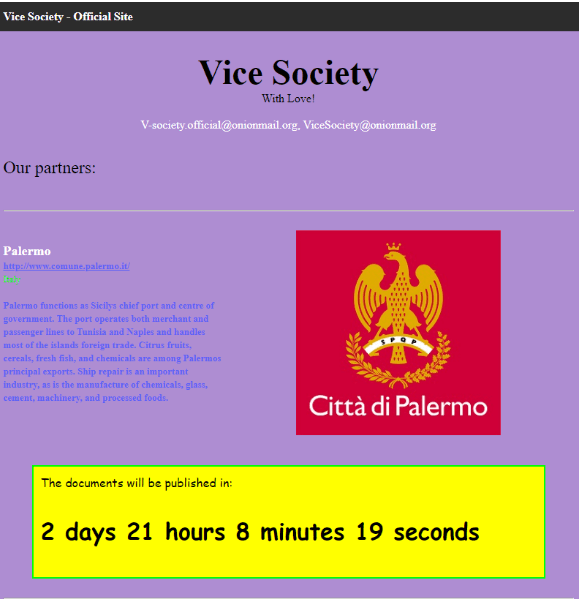
This indicates that the ransom payment negotiations are still in progress, and Vice Society is hoping that its threats to Palermo’s officials will have their intended effect.
Threatening the victim with the exposure of information is a common method for ransomware organizations today, called the “double extortion” tactic (also known as pay-now-or-get-breached), and can be an effective means of persuading victims to pay the ransom.
Vice Society may have in its possession personally identifiable information (PII) belonging to Palermo citizens as well as private data of anyone who has used the municipality’s online services.
It’s worth mentioning that the ransomware group hasn’t published any samples of stolen documents, so the data exfiltration claims haven’t been confirmed yet.
More on the Vice Society Ransomware Group
Vice Society is notorious for breaking into networks by exploiting known flaws in unpatched systems. In August 2021, security experts at Cisco Talos discovered the particular ransomware group deploying a DLL that abused CVE-2021-1675 and CVE-2021-34527, also known as “PrintNightmare” vulnerabilities.
While it’s impossible to tell if Palermo’s computer systems had a security hole that could be exploited for initial access, it wouldn’t be a far-fetched scenario for public-facing state networks.
Palermo authorities have not provided any information regarding the cyberattack, despite the fact that it has been almost a week since they turned off the entire IT system that operates all of the city’s services.
If Ransomware Concerns You…
Join us on Tuesday, June 21st, 1pm BST/2pm CEST for our next webinar, when Cyber-Security & Heimdal Product Expert Andrei Hinodache and Pre-Sales Engineering Manager Robertino Matausch will explain why ransomware is on the rise, and how should executives evaluate their company’s ability to prevent and recover from ransomware attacks.
What’s more, we will be showing you how to do this LIVE! Our experts will walk you through ransomware incident preparedness, technical testing through live simulations, detection, and suggestions for thwarting attackers by hardening systems and infrastructure.
Make sure you register here!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










